Photo Gallery
|

|
Cogility Counter Insider Threat
Additional Info
| Company | Cogility |
| Company size | 50 - 99 employees |
| World Region | North America |
| Website | https://www.cogility.com |
NOMINATION HIGHLIGHTS
Current insider threat management programs are predominantly reactive – solely monitoring for security violations and anomalies. Organizations need to detect and respond to suspicious and malicious user activity, but a reactive insider risk posture is too late and too costly. Cogility Counter-Insider Threat (C-InT) provides a comprehensive, whole person approach to detect, prevent, and mitigate insider threats. Cogility continuously monitors and analyzes both technical and behavioral potential risk indicators (PRIs) at machine-speed to identify insider threats with full explainability. Combined with its advanced case management, Cogility C-Int modernizes insider threat management programs to help organizations more efficiently and effectively respond to and avoid impactful incidents.
Analysts typically respond to and gather incident evidence, after the fact, from SIEM, UBA, and other tools. They aren’t equipped to identify high-risk individuals early enough to mitigate their consequential actions. While security controls are monitored, underlying behavioral risk indicators such as from H.R. and other available sources, are largely unaccounted for — undermining proactive intervention. C-InT programs are further hindered due to data and team isolation, threat analysis and collaboration delay, and cobbled toolsets that impede case workflow efficacy. Cogility C-InT integrated solution overcomes these limitations with a scalable platform, powered by AI, patented analytics and foundational insider risk model, that adapts to your existing policies, technical security and behavioral data sources, and processes.
Key capabilities include:
– Continuously monitor for explicit and predictive insider threats
– Increase C-InT coverage, capacity, assessment, and response coordination
– Improve analyst case workload productivity with automated risk scoring, profiling, case workflow, and collaboration.
– Leverage existing security data and readily incorporate human resources, operational, and other data sources.
– Non-disruptive deployment, extensible foundational C-InT model, customizable dashboards and reports, and integrated case management.
– Early insider threat warnings to preempt high-consequence incidents and help those personnel in need of support
Key Capabilities / Features
Cogility’s Counter-Insider Threat solution, powered by our Cogynt unified real-time platform (URP), is uniquely designed and proven to meet the immense and dynamic information-processing, complex analytics, and workflow challenges faced by insider threat analysts across government and industry. With Cogility's Counter-Insider Threat solution, organizations can increase insider threat monitoring capacity, analyst and case manager productivity, and overall program efficacy. Additional features include:
- Multiple, simultaneous data source ingestion and processing
- Semantic analysis to process structured or unstructured data at scale
- Complete, no-code behavioral modeling environment that is self-documenting
- Extend models from a pre-defined set of risk profile types to align to your organizations security and HR policy
- Patented, real-time behavioral analytic to hierarchically process technical and behavioral event patterns to yield actionable intelligence
- Predictive Intelligence to continuously monitor and assess the insider risk surface with stateful profiling, scoring, and alerting
- Identify immediate insider threats and individuals on the critical path to insider risk
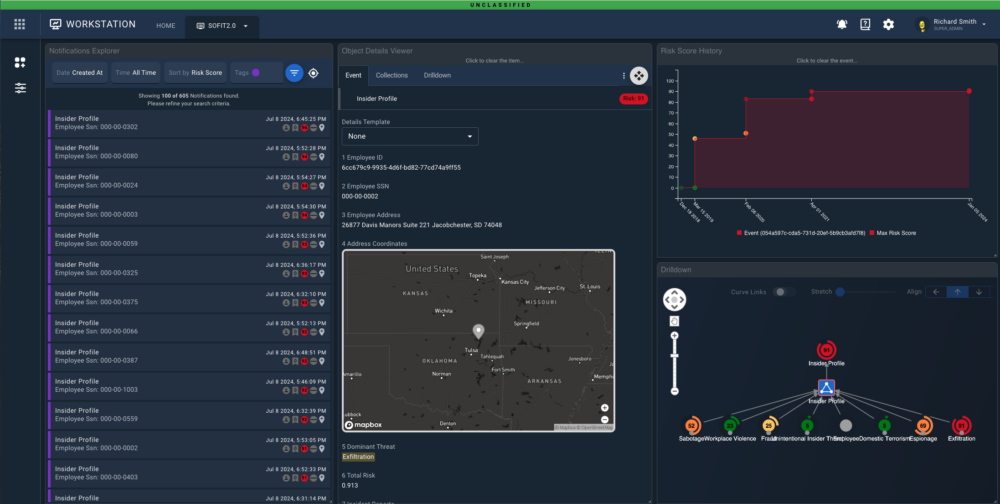
- Gain full risk history, indicator traceability, and auditable evidence to support informed assessment and response
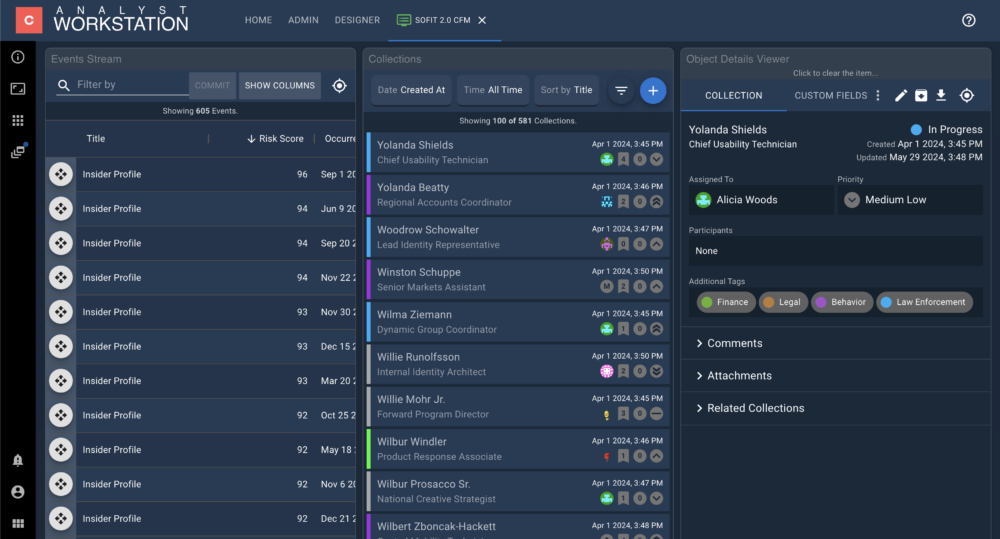
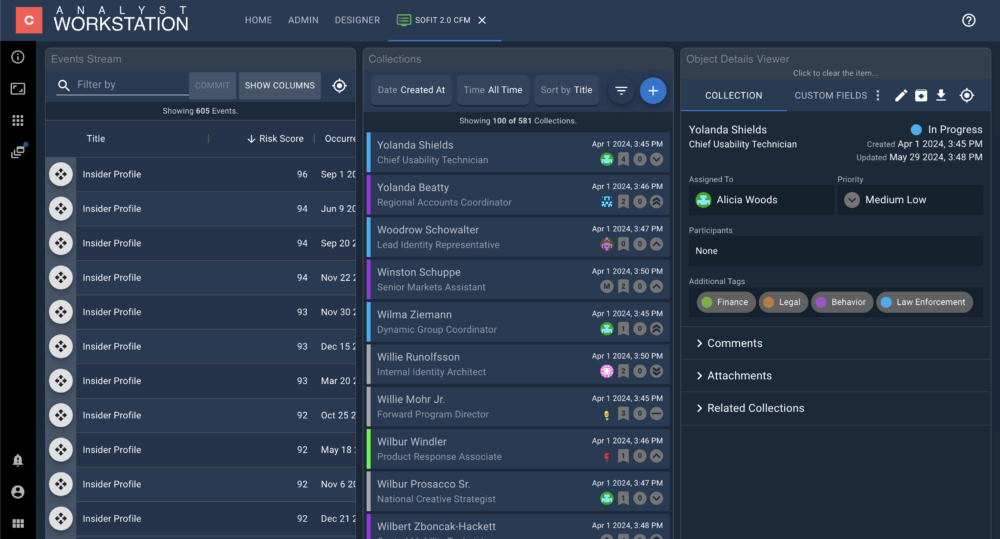
- Visualizations to present and manipulate complex data and relationships in various contexts (geospatial, link charts, hierarchy charts, graphs and histograms, lists)
- Case management dashboards, workflow tracking, and collaboration enabling efficient file creation, risk assessment, recommendations, annotation, review, and response coordination
- Operational insights across your entire program to simplify tracking and reporting KPIs
- Open architecture to facilitate integration with other applications and data stores
- Secure operation in your private cloud for scalable, real-time data processing and analysis
How we are different
- Whole Person Insider Risk Management
Cogility C-InT provides comprehensive, whole-person insider threat management to enable analysts and case assessors to make more informed decisions and expedite intervention. Powered by our patented Cogynt Hierarchical Complex Event Processing (HCEP) technology, the solution dynamically analyzes technical and behavioral potential risk indicators (PRIs), informed by the SOFIT ontology, to identify insider threats, such as data exfiltration, espionage, workplace violence, and fraud, in progress and early in the critical path – allowing organizations to get left harm. AI-based modeling provides predictive risk analytics to continuously assess complex patterns of high-risk behaviors, maintaining state and applying risk decay. This significantly enhances insider threat profiling, scoring, and alerting accuracy with full explainability for effective assessment, response, and prevention.
- Case Management and Program Oversight
Cogility C-InT offers extensive case management and program monitoring capabilities to enhance analyst workload productivity, auditing, and oversight. The solution provides insider threat teams with customizable dashboards, risk scoring, profiling, tagging, case assessment, status tracking, and respond coordination. Robust workflow features streamline case prioritization and assignment, remote case submission, evidence compilation, rich assessment annotation, collaborative contribution and review, and intervention processes. An integrated BI visualization and reporting provides management views to gauge case performance and program trends.
- Non-disruptive, Customizable, and Rapid Integration
Cogility C-InT solution incorporates foundational insider risk models that can be tailored to meet your organization’s mission requirements, policies, and priorities. The base set of insider risk models can be readily tuned and expanded within a self-documenting, no-code authoring environment. The solution’s stream data analysis processes technical security and behavioral data sources at scale and offers flexible data ingestion (stream, batch, structured, and unstructured) that is non-disruptive. The cloud-scalable, high available solution operates in your virtual private cloud for enhanced security and privacy. Optional integration services help meet operational timeframes and program objectives.


