Photo Gallery
 |

 |
Cognito platform from Vectra

Additional Info
| Company | Vectra |
| Company size | 100 - 499 employees |
| Website | http://www.vectra.ai |
NOMINATION HIGHLIGHTS
Vectra protects businesses in the cloud by stopping catastrophic data breaches.
Cyberattacks – whether driven by financial gain, political and social disruption, state-sponsored espionage, or insider threats – are prompting cloud, data center and enterprise organizations to rethink how to best protect their business and critical data. With businesses facing devastating reputational and financial damage from data breaches, the stakes have never been higher.
Unfortunately, the status quo’s outdated approach to security – designed to prevent cyberattackers from getting inside networks – isn’t working. Traditional legacy security designed to keep out attackers are blind to these ever-changing threat behaviors, giving cybercriminals free rein to spy, spread and steal.
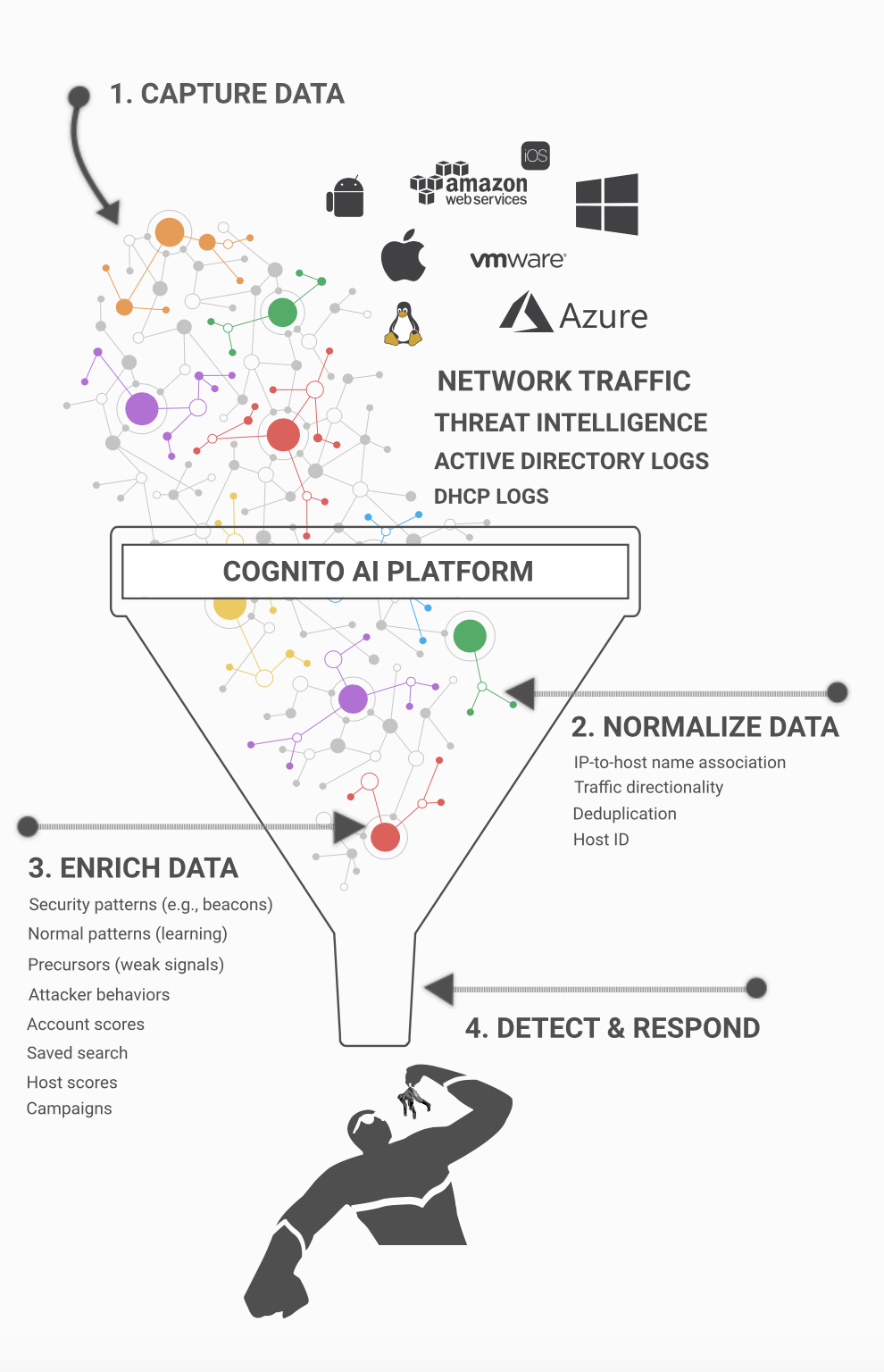
That’s why Vectra created the Cognito® platform. The Cognito platform is a reliable way to detect hidden attackers who get inside and respond instantly to stop in-progress threats from becoming a data breach. It empowers security teams to proactively hunt for evasive threats, augments organizations existing security investments, keeps up with the changing threat landscape, and offers exceptional scale across cloud, data center and enterprise infrastructures.
Vectra offers three applications on the AI-driven Cognito platform to address high-priority use cases.
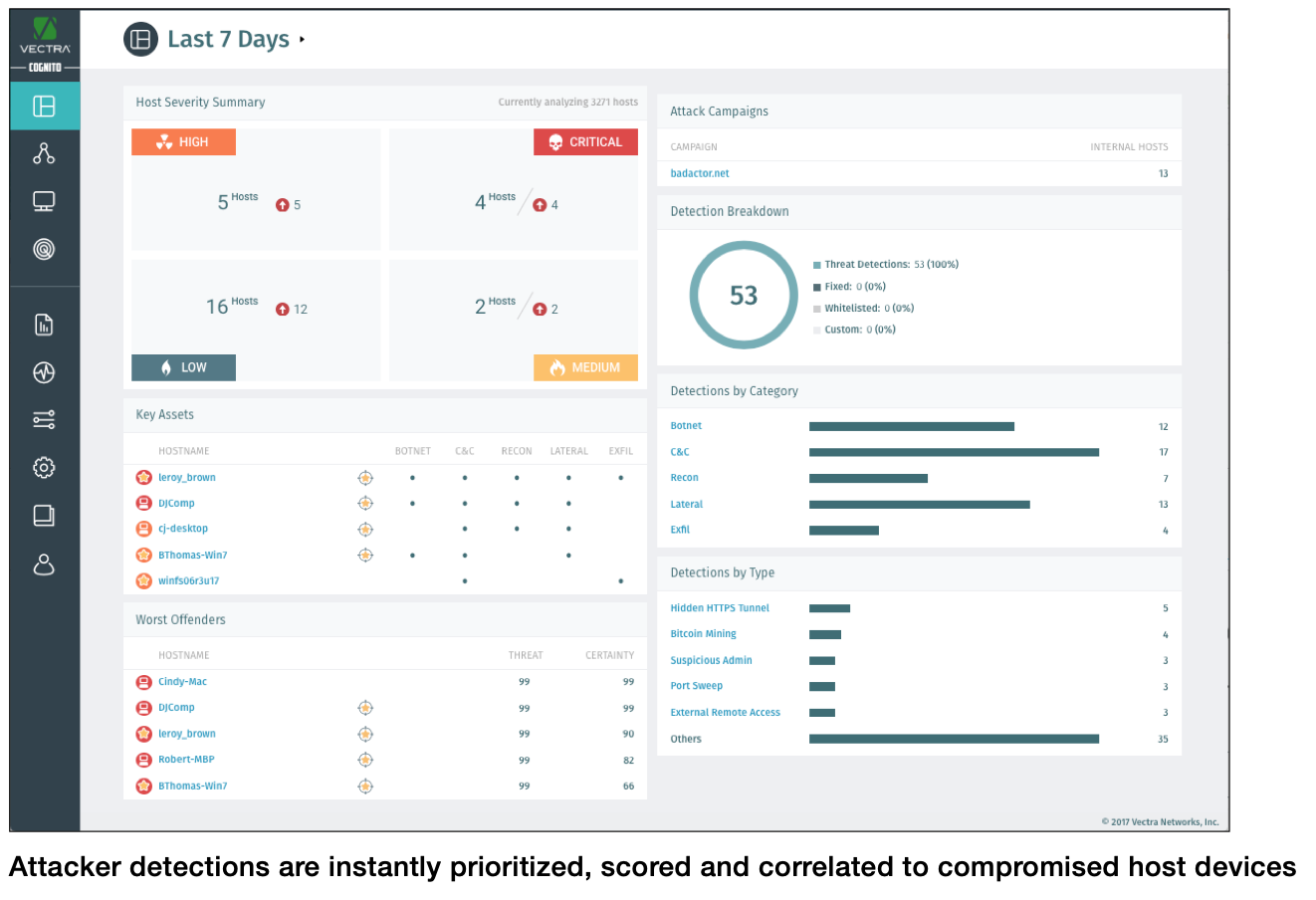
• Cognito Detect™ AI software automates the detection of hidden cyberattacker behaviors and prioritizes the ones that posed the highest risk. Cognito Detect reduces the security operations workload by 34X and gives security professionals more time to focus on the all-important task of stopping data breaches.
• Cognito Recall™ is a cloud-based investigative workbench that enables security professionals to proactively hunt for threats and perform conclusive attack investigations.
• Cognito Stream™ is an indispensable cybersecurity weapon correlates security-enriched metadata with other data sources and lets security researchers and analysts hunt retrospectively for threats based on high-value indicators of compromise.
How we are different
Vectra is the leader in network threat detection and response across cloud, data center, and enterprise infrastructures. We hold 15 patents for AI that automates the hunt for cyberattacker behaviors and 18 patent applications are pending.
• Cognito automates threat detection and speeds-up response. Always-learning behavioral models reveal hidden attackers across cloud, data center and enterprise infrastructures. With Cognito, security analysts can intervene and analyze, triage, and respond decisively.
Cognito prioritizes in-progress attacks that pose the highest business risk so you know where to focus your attention first. Cognito also identifies the scope and precise locations of attacks so enterprises can stop them from spreading.
Detecting attackers is incomplete without a quick response, and Vectra responds with deliberate speed. Cognito works in real time with the entire ecosystem of cybersecurity investments to accelerate response time, stop the progression of attacks and avoid data breaches.
All of which give us bragging rights as the leader in network threat detection and response that extends across cloud, data center and enterprise infrastructures.
• Cognito empowers threat hunters. Security analysts can launch deeper incident investigations detected by Cognito and other security controls and hunt retrospectively for covert attackers. Cognito addresses the overwhelming workload of security analysts who manually investigate thousands of threat alerts per day that might or might not be an attack. And it Cognito helps address the worldwide shortage of talented security professionals, empowering security analysts and threat hunters to focus on the all-important task of stopping data breaches.
• Cognito exposes hidden attackers while maintaining data privacy. Cognito collects, analyzes and stores network metadata, logs and cloud events, protecting organizations from threats without violating data privacy. This ensures compliance with data privacy mandates like the European Union General Data Protection Regulation (GDPR).

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



