Photo Gallery
 |

 |
ColorTokens Xshield for micro-segmentation

Additional Info
| Company | ColorTokens Inc. |
| Company size | 100 - 499 employees |
| Website | http://www.colortokens.com |
NOMINATION HIGHLIGHTS
ColorTokens’ Xshield, is a cloud-based solution that addresses the four most important security considerations put forth by CIOs and enterprise security teams to achieve proactive security on multi-cloud data centers:
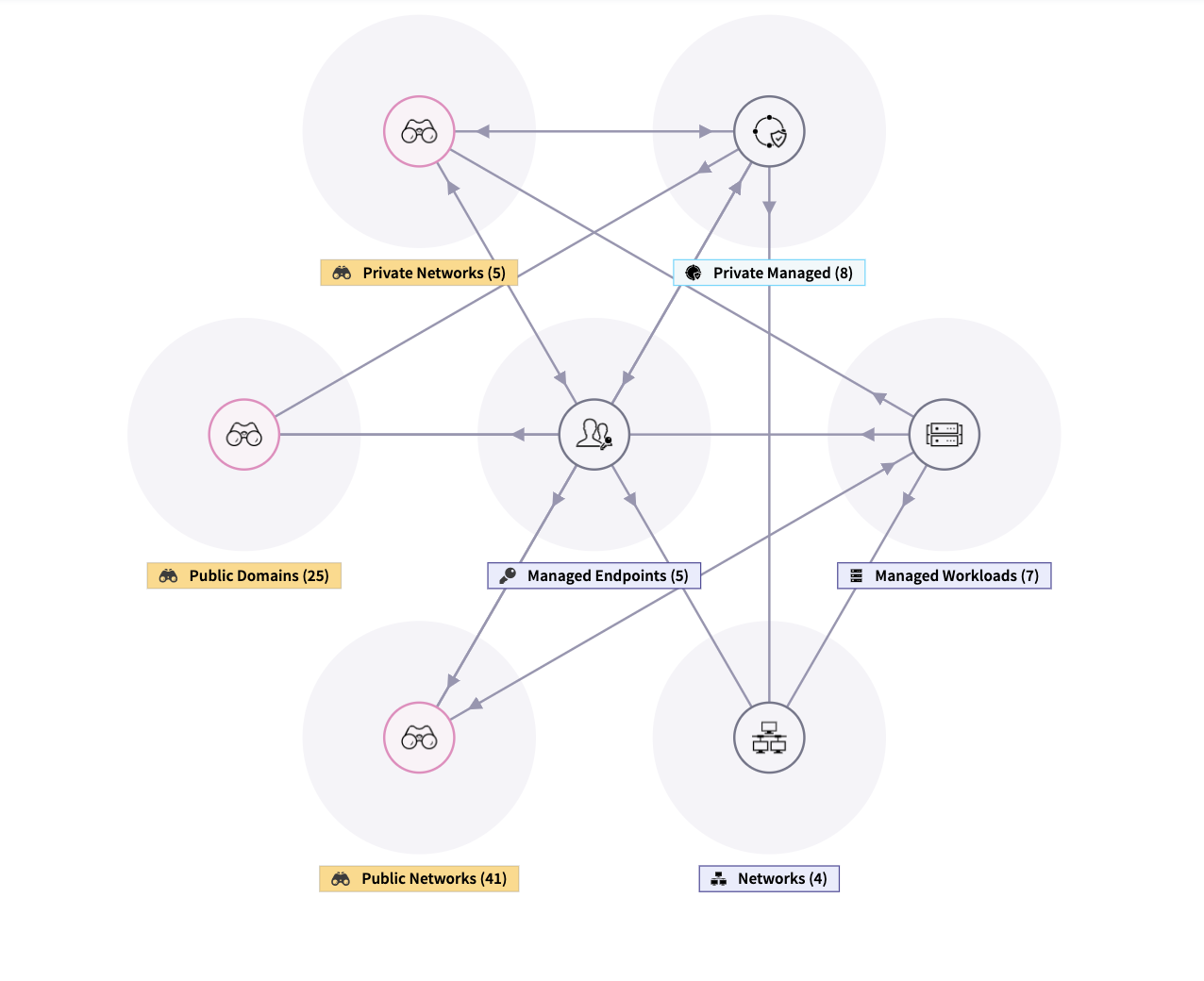
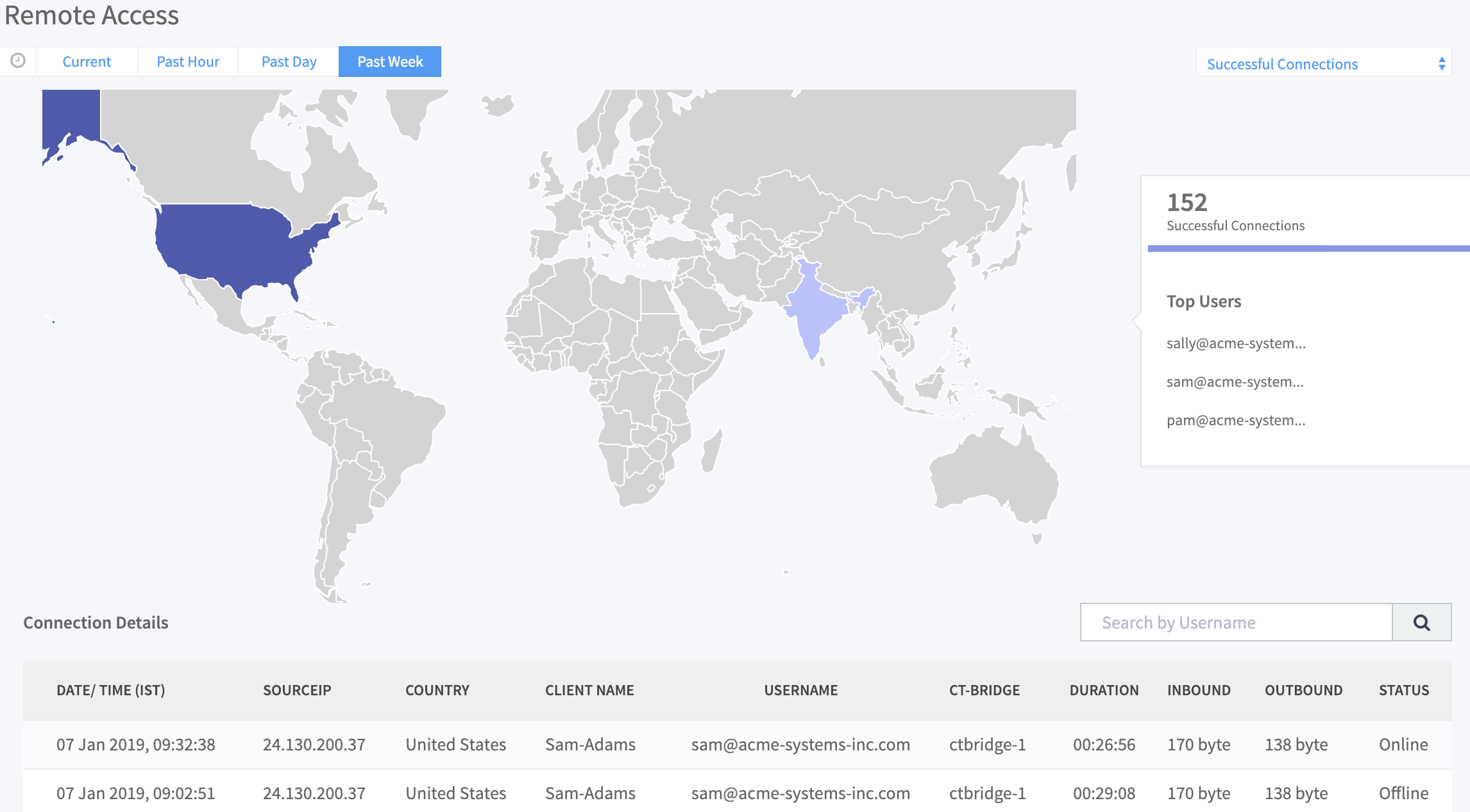
1) Visualize how secure you are in real-time - Gain unprecedented asset, traffic, and vulnerability visibility
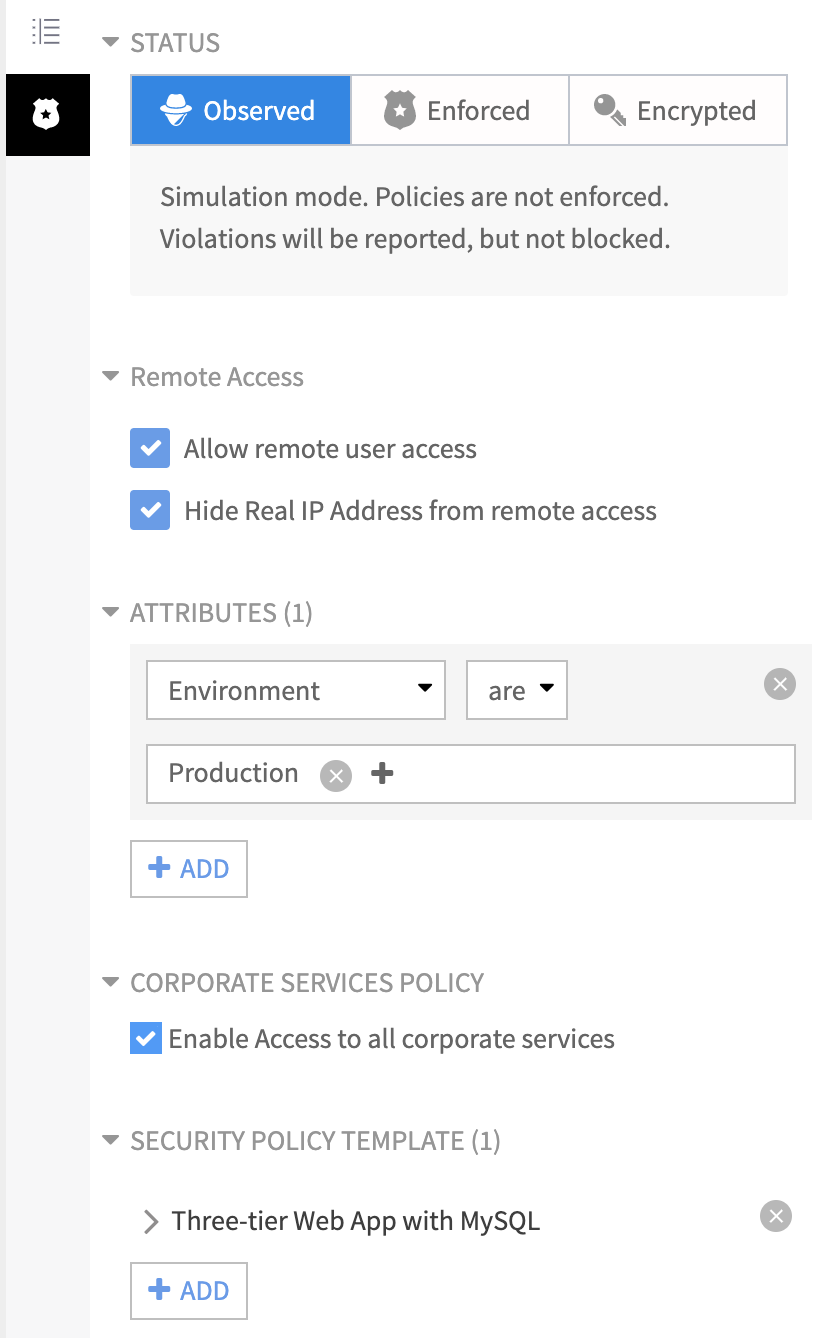
2) Progressive security with zero trust micro-segmentation - Create segments to fit your needs – group workload by native attributes (OS name, network, etc.) or create based on custom tags (location, compliance scope, etc.). Remove uncertainty before enforcing micro-segmentation policies using observation mode to improve their effectiveness
3) Provide continuous assurance - Proactively assess, report and mitigate risks
4) Reduce the cost of compliance - Limit the scope of audits even in dynamic application environments
ColorTokens enables all the above, across on-premise and multi-cloud data centers, without needing siloed point security products, additional hardware, or multiple visibility tools.
Most importantly, with ColorTokens, security and risk teams can achieve the desired security posture and reduce the attack surface in minutes, as opposed to weeks or months with traditional security products involving firewalls, VPN, and other cumbersome technologies for segmenting the network.
ColorTokens is vendor and environment agnostic. The solution comes with a visual policy editor to define security policies through a central console. The security policies can be simulated, refined, and then enforced. Once enforced, the workloads can move from on-premise to cloud or vice-e-versa. The security posture of the asset will remain intact. This helps enterprises take benefit of cloud and virtual environments without compromising security.
“Fantastic visibility to my entire network. Helped save time and money as we found and plugged a perimeter firewall vulnerability, just in time before the external audit.” Tony Bazurto, EVP, Compex Legal Services.
How we are different
1) Environment and technology agnostic micro-segmentation in minutes - Data centers running business-critical workloads need proactive security solutions to protect from hidden and emerging threats. Enterprises invest in several high-capacity firewalls and intrusion detection systems but continuously worry about Advanced Persistent Threats (APTs), malware, and other security breaches that may be lurking undetected anywhere in the data center. Traditional methods of detecting and preventing the spread of lateral threats involve several challenges:
- Segmenting using subnets – Creating multiple VLANs/ACLs is cumbersome and time-
consuming
- Segmenting using firewalls – Capital intensive, operational overhead, and performance
choking
- Segmenting using hypervisors – Not effective in multi-hypervisor or multi-cloud
environments
2) Zero-Trust based approach with automatic enforcement - ColorTokens Xshield for micro-segmentation, built around zero trust security architecture, enables software-defined application micro-segmentation in minutes, reducing the attack surface and improving the overall security posture of your data center. Automatically enforce micro-segmentation policies on new workloads and applications with the dynamic policy engine. Dynamic policy re-computation based on changing workload behavior and redistribution in minutes, all from the cloud
3) Zero-Trust network access - As businesses improve their security posture with micro-segmentation, one gaping hole is unfettered access of users to the micro-segmented and protected workloads. Micro-segmentation solutions from most vendors have little to no awareness of user identity and application authorization. ColorTokens micro-segmentation technology doesn’t stop just at the workloads and applications. Leveraging ColorTokens’ powerful software-defined micro-segmentation technology, ColorTokens Secure User Access brings in the awareness of users and their roles tied to the business requirements. This surpasses any other competitor in the market today and provides operational ease to the end customers and a single management console.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



