Photo Gallery
 |
 |
ColorTokens Xtended ZeroTrust Security Platform

Additional Info
| Company | ColorTokens Inc. |
| Company size | 100 - 499 employees |
| Website | http://www.colortokens.com |
NOMINATION HIGHLIGHTS
ColorTokens Xtended ZeroTrust Security Platform provides unified visibility, micro-segmentation, zero-trust network access, cloud workload, and endpoint protection. The cloud-based platform addresses the four most important security considerations put forth by CIOs and enterprise security teams to achieve proactive security on multi-cloud data centers:
1) Visualize how secure you are in real-time - Gain unprecedented visibility into multi-cloud assets, cross-segment traffic, and vulnerabilities
2) Understand the security gaps and act on them - Identify suspicious traffic patterns across cloud workloads, applications & users and isolate critical assets
3) Provide continuous assurance - Proactively assess, report and mitigate risks
4) Reduce the cost of compliance - Limit the scope of audits even in dynamic application environments
Built on a zero-trust security model, ColorTokens delivers all the above, across multi-cloud infrastructure, without siloed point security products, additional hardware, or multiple visibility tools. With ColorTokens, security and risk teams can achieve the desired security posture and reduce the attack surface in minutes, as opposed to weeks or months with traditional security products involving internal firewalls, VPN, and so on. Moreover, the traditional tools that you had access to in your data center are no longer available to you on the cloud – this is a significant cloud scalability limitation.
ColorTokens is vendor and environment agnostic. The solution comes with a visual policy editor to define security policies through a central console. The security policies can be simulated, refined, and then enforced. Once enforced, the workloads can move from on-premise to cloud or vice-e-versa. The security posture of the asset will remain intact. This helps enterprises take benefit of cloud and virtual environments without compromising security.
How we are different
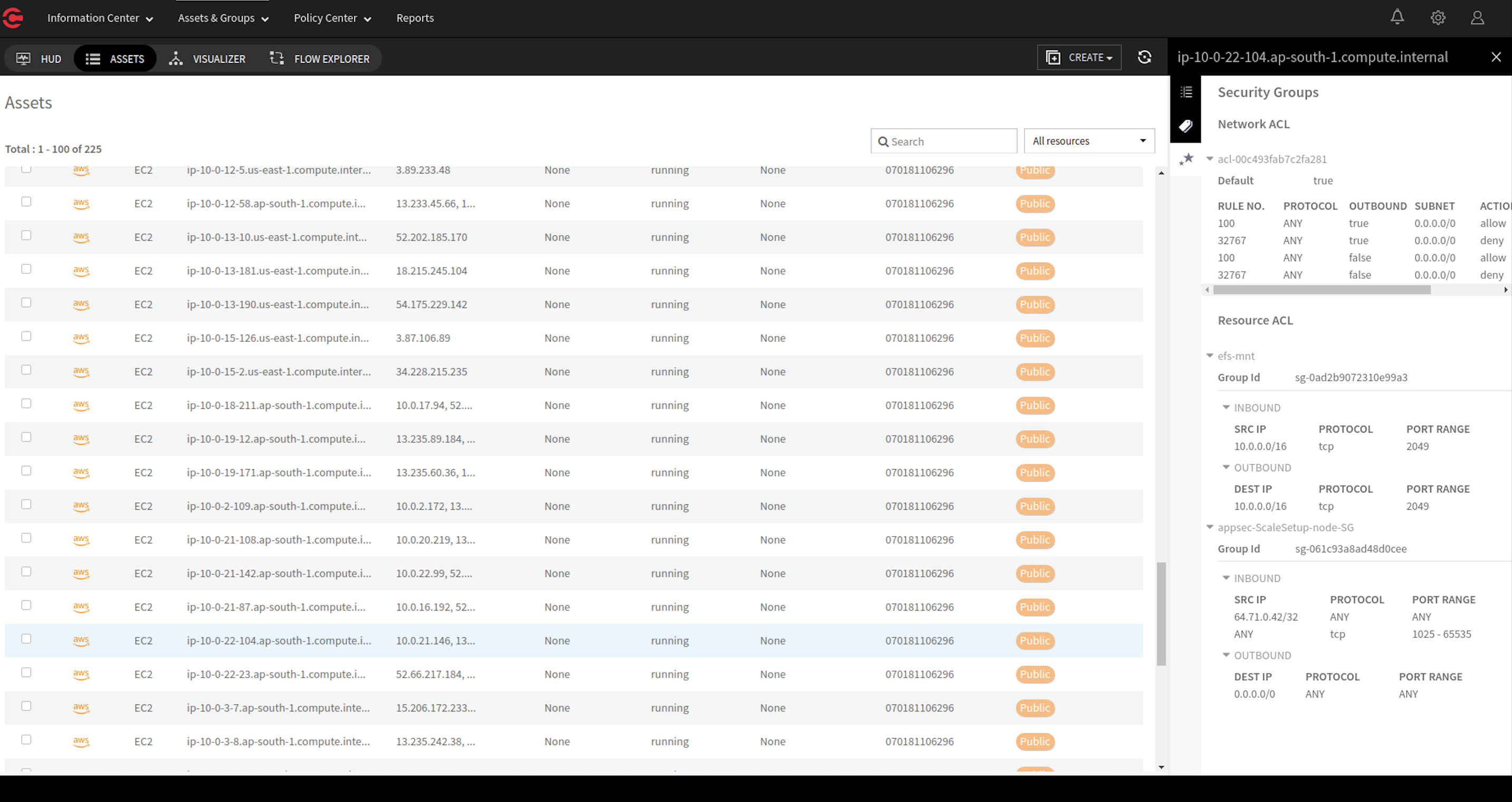
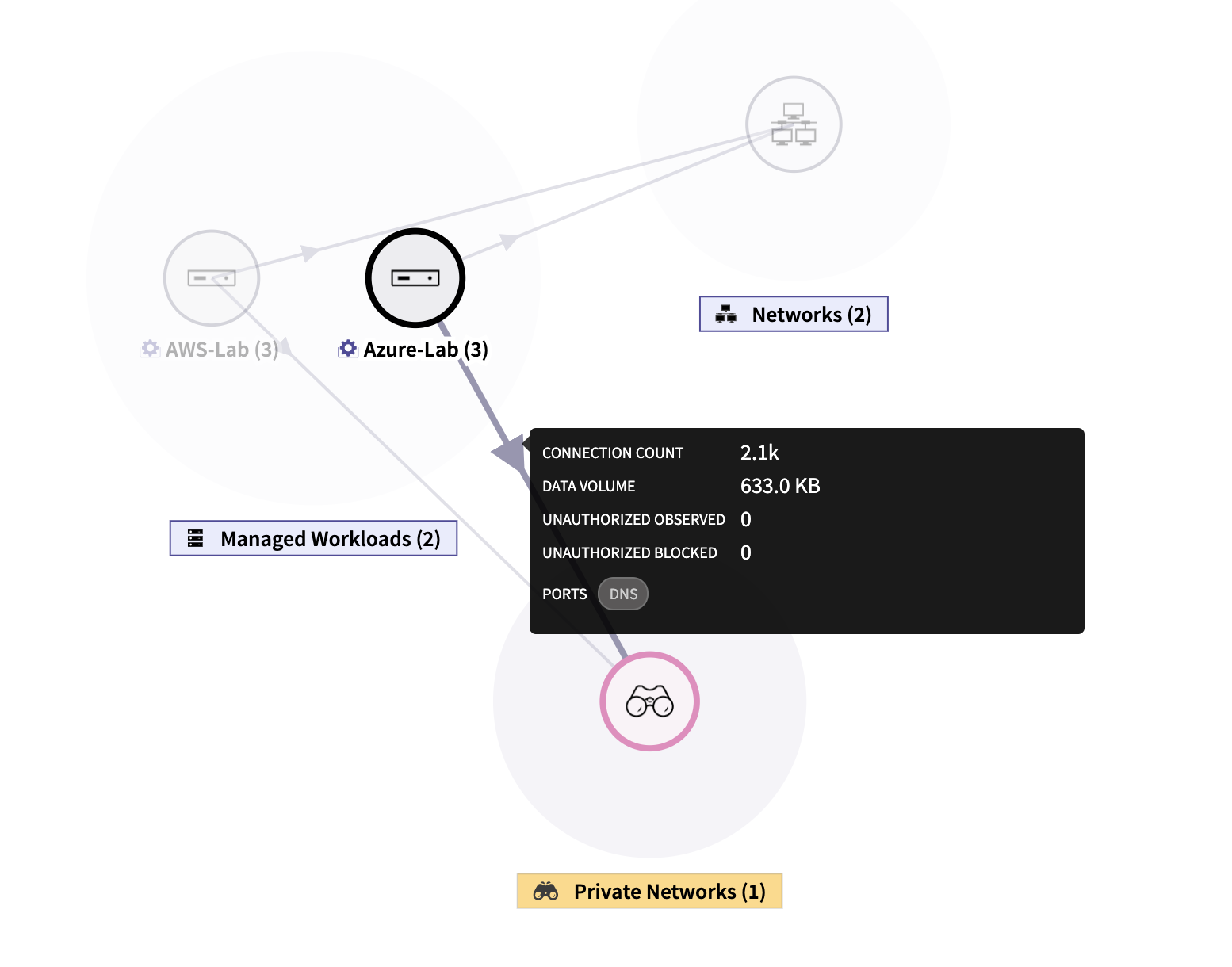
1) Visibility – For decades, organizations have primarily relied on reactive, perimeter-based defense – looking for the known bad or mitigating the threats after the damage is done. The other overlooked challenge is insider threats, and lateral East-West traffic comprises over 75% of the overall data center and cloud traffic, this lateral spread is going undetected by current security tools – leading to security blind spots. ColorTokens allows users to gain Zero Trust view into networks and cloud workloads across on-premise and hybrid clouds, understand threat traversal for forensics, and faster incident response and mitigation. It also helps users quickly uncover unwarranted open ports and misconfigurations across all assets using built-in vulnerability port scanner and integration with market-leading threat intelligence and monitor security control violations for applications and workloads.
2) Agentless cloud security - ColorTokens provides an agent-less solution to deliver unrivaled security for cloud infrastructure. The solution provides augmented visibility into flow logs (for Amazon Web Services (AWS), Azure, and Google Cloud Platform (GPC) Application Programming Interface (API)) that includes session awareness, source-destination correlation, and data enrichment with metadata. This allows security and risk teams to visualize the cloud infrastructure and the ability to customize views based on region, zone, and Virtual Private Cloud (VPC). Continuous security monitoring flags VPC Access Control List (ACL) changes, security group changes, or any changes to the existing group configurations. The teams get a consolidated view and can micro-segment cloud applications and get complete access control.
3) Achieve consistent security posture across cloud workloads - Rapidly migrate and deploy cloud workloads without security being an afterthought. Xshield helps users understand the attack surface, limit lateral movements with unique attribute-based security automates policies across workloads. The policies also move with the workloads ensuring continuous protection and eliminating manual policy configurations.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



