Photo Gallery
 |

|
Constellation Analytics Platform™


Additional Info
| Company | Haystax Technology |
| Company size | 10 - 49 employees |
| Website | http://www.haystax.com/ |
NOMINATION HIGHLIGHTS
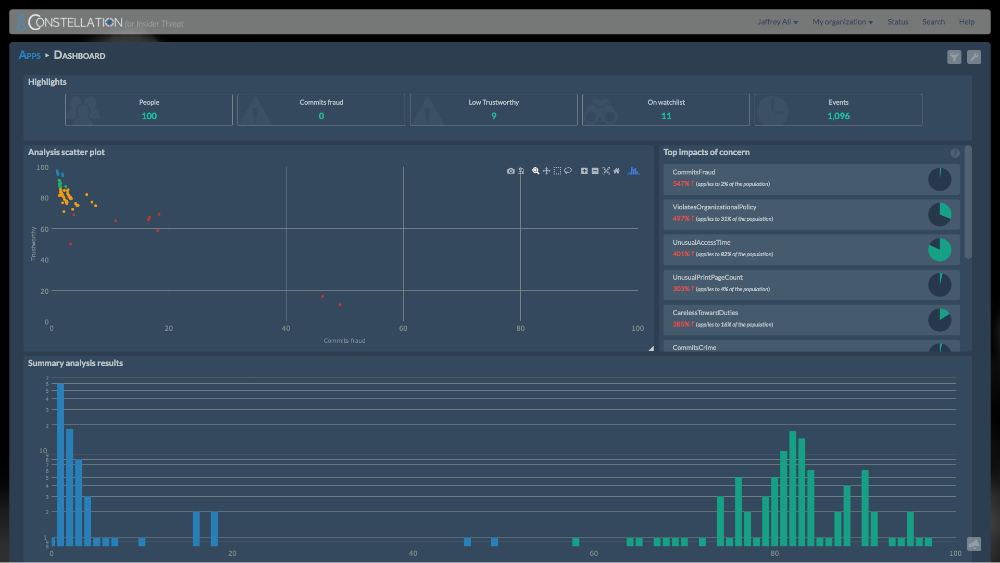
Haystax Technology’s Constellation Analytics Platform™ delivers advanced security analytics and risk-management solutions that enable rapid understanding and response to virtually any type of cyber or physical threat. Based on a patented model-driven approach that applies multiple artificial intelligence techniques, it reasons like a team of expert analysts to detect complex threats and prioritize risks in real time at scale. Constellation pinpoints an organization’s greatest threats, dramatically reduces events warranting investigation, and even detects and predicts threats that may go undetected by other solutions, significantly improving the effectiveness of security and response teams. When these complex threats are detected and a risk has been prioritized, Constellation automatically generates alerts and recommended actions to the user. Accompanying events, timelines, and risk assessments – including risk determination analysis – make it clear to decision-makers why a risk was identified and needs to be addressed immediately.
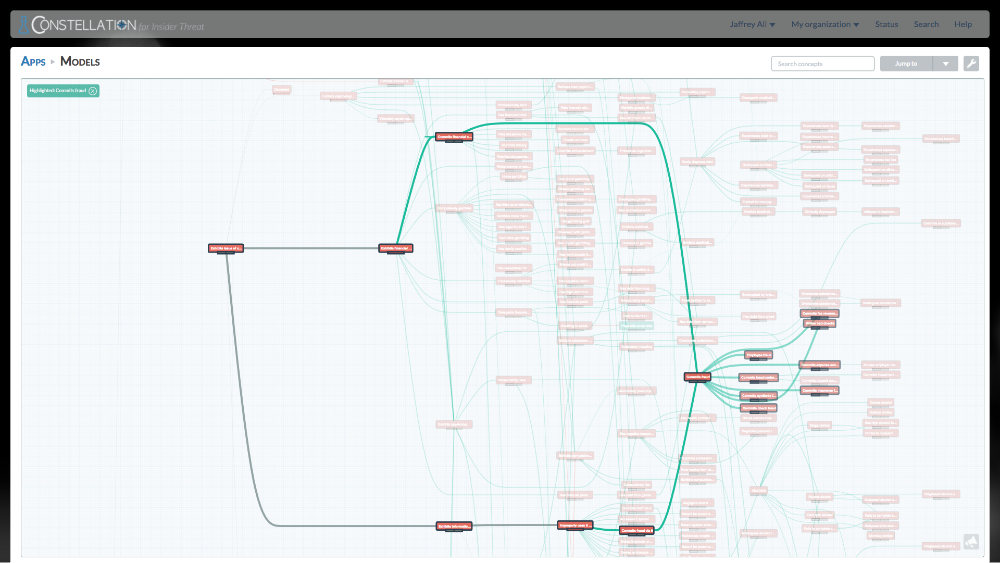
A highly-secure, cloud-based software platform, Constellation has two major product lines: Constellation for Incident Management and Constellation for Insider Threat. The first, Constellation for Incident Management, detects, monitors, analyzes, communicates and responds to emerging threats and ongoing incidents from a single incident management system – whether it’s used for corporate security, law enforcement, school or public safety. Alternatively, Constellation for Insider Threat, is the only solution that establishes and continuously evaluates a ‘whole person’ model of trustworthiness to pinpoint insider threats accurately and early.
With Constellation, organizations move to a dynamic and predictive risk posture, make quicker decisions, and speed remediation for more effective protection of their critical assets. Unlike other solutions that require extensive professional services to create a baseline model, Constellation is delivered with an out-of-the-box model of over 700 key risk indicators that covers over 80% of all customer needs. And its models can easily be extended or adapted to address enterprise-specific threat concerns or new domains.
How we are different
• Haystax Technology’s novel security analytics engine is fueled by a model-driven approach vs. a data-driven approach. That means rather than mining a massive amount of data for threat intelligence, Constellation begins with a model of key risk indicators for a domain problem and then evaluates relevant data against the model continuously in real-time to pinpoint threats early and accurately. It dramatically reduces the number of events to be investigated from tens – or even hundreds – of thousands to the thousand or so most important, and then prioritizes to the handful or so risks that need to be addressed.
• Constellation boosts analyst/investigator/responder productivity by reasoning like a team of experts at scale to prioritize risk for quicker decisions and faster responses and remediation. Seamlessly working with an organization’s existing security and IT infrastructure, it lowers overall TCO – including prevention and remediation costs – and produces a force multiplier for more effective protection of critical systems, data, facilities, and people. Constellation transforms an organization’s risk posture from reactive and static to predictive and dynamic – this strategic benefit is matched by no other product or solution in the security analytics market.
• Beyond gaining significant traction in top-tier financial institutions, having been selected over other security analytics providers for its innovative approach and effectiveness, Constellation has been proven at scale. It’s deployed by the state of California for their Common Operating Picture (Cal COP) for Threat Awareness, protecting 85% of California’s population across eight major urban areas. Constellation is also successfully implemented in the nation’s largest insider threat program for more than a million personnel.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



