Photo Gallery
 |
 |
Core Access


Additional Info
| Company | Core Security, A HelpSystems Company |
| Company size | 500 - 999 employees |
| Website | http://www.coresecurity.com |
NOMINATION HIGHLIGHTS
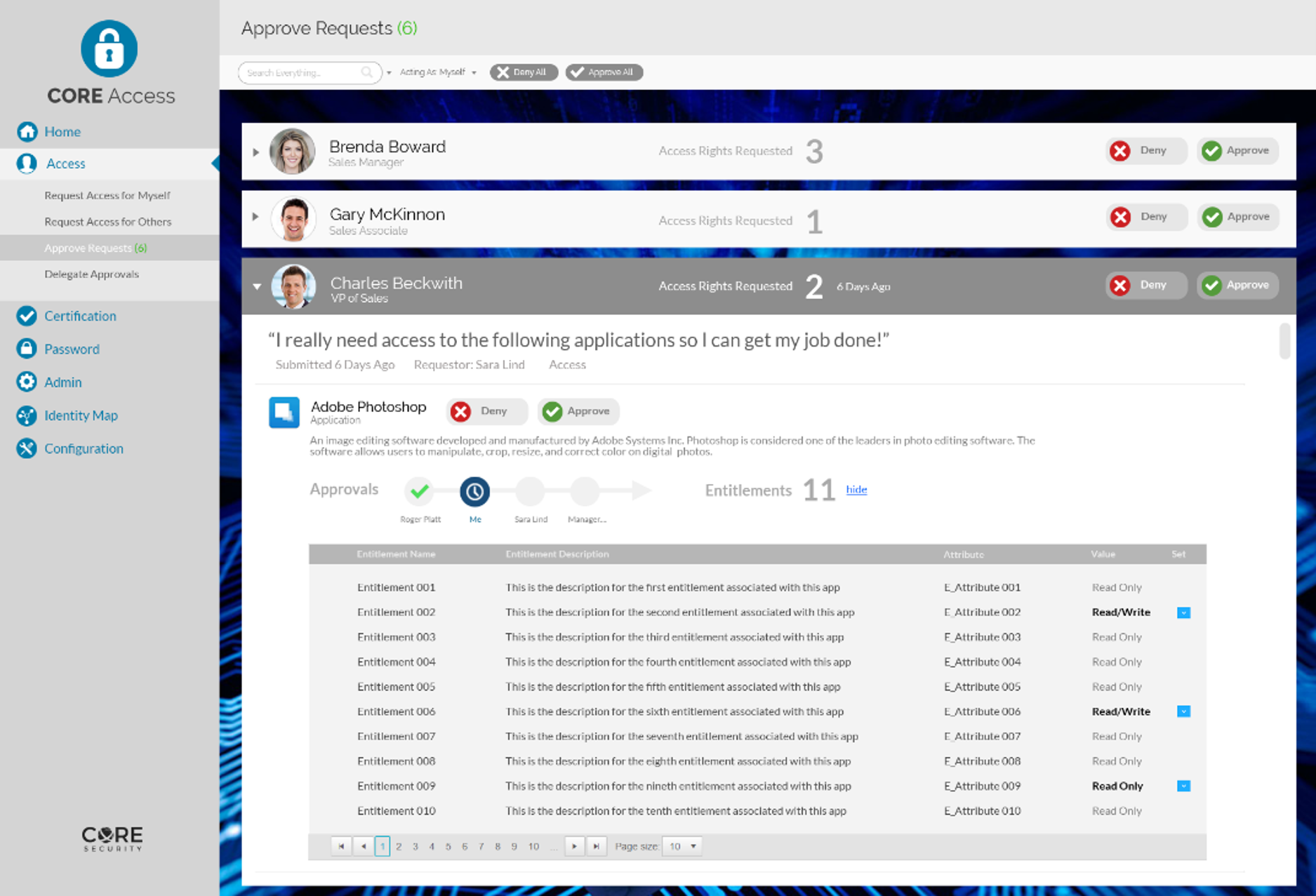
As part of the Core Security portfolio of solutions, Core Access is a convenient web portal where end users can request access and managers can review, approve, or deny access. Using a shopping cart approach, Core Access delivers an efficient and user-friendly experience—replacing paper forms, emails, and tickets used to manage access. Plus the ability to leverage roles enables access to be assigned quickly and accurately
Core Access provides centralized and simplified access control by managing how access is requested. Users easily request access to the systems and applications they need, and can track the status of their request in the user-friendly web portal. As users log into the centralized Core Access portal, they receive a personalized page with all their current requests and statuses. This personalized view streamlines the access request process for the employees, managers, and IT teams.
Providing one place for users to request access ensures users go through the appropriate channels and reinforces that proper approval and fulfillment policies are followed. Core Access also enables unique approval workflows to be built or tailored to align with any type of organizational structure. Organizations can also use Core Access to automate provisioning around the user lifecycle. This enables authorized individuals to leverage Core Access for quickly disabling user access, preventing any opportunity for employees or other users to retain access to data upon their departure from the organization.
How we are different
Core Access is an industry-leading user access request management system that enables organizations to effectively:
- Simplify and Streamline Access Requests at Scale: Users can easily request access to necessary applications and track their status in the intuitive web portal. Requests are automatically routed to the appropriate approver to review requests, grant approvals, and manage access. Approvers can easily retrieve detailed user-request information, providing a simple and clear view of access requests and their context.
- Improve Security and Mitigate Risk: Making sure that users have appropriate access goes a long way towards bolstering an organization’s risk management and its security posture, ensuring that users are operating within well-defined roles and are not overprovisioned. Core Access ensures users receive only the access needed to do their job with an easy-to-use approval system, which follows company policies to determine the appropriate approvers.
- Enhance Compliance, Review, and Certification Processes: Limiting access to only those individuals that need it enables companies to stay more compliant with government regulations and industry standards. Core Access ensures that access is strictly controlled and enables organizations to prove they are taking action to meet compliance requirements, creating a comprehensive audit trail of requests and approval activities for auditing and compliance activities.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



