Photo Gallery

|
|
Cyber Risk Protection Platform

Additional Info
| Company | Happiest Minds Technologies |
| Company size | 2000 employees |
| Website | http://www.happiestminds.com |
NOMINATION HIGHLIGHTS
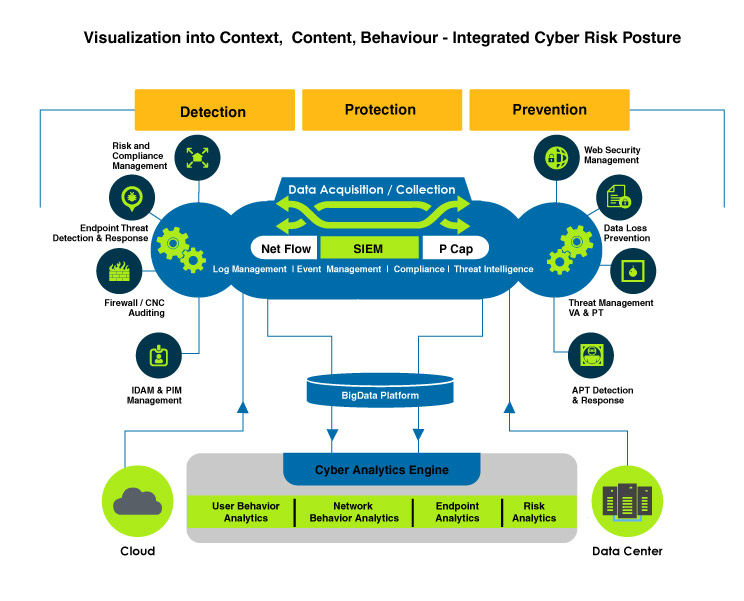
Happiest Minds Cyber Risk Protection platform helps organizations leverage on multiple security technologies including SIEM, advanced and next generation network, endpoint security and DLP, providing deeper analytics and insights for an integrated approach to handle overall threat lifecycle and address security holistically.
The overall risk management which includes the steps- Protect,
Detect, Mitigate and Adapt is undergoing a deep transformation in
an organizational point of view. The key executives of organizations
are viewing cyber risk management as an influential factor in
business decision making capable of delivering more value to
business. Since cyber risk is the business risk itself, addressing it
effectively is top most priority for any organization. If cyber risks
are not effectively managed, organizations will not be able to
protect the Confidentiality, Integrity and Availability of the
information it holds. It may lead to irreparable reputation damage,
huge financial implications in terms of regulatory fines and legal
complications. At a time when attack models are getting more and
more sophisticated and the current defensive measures fail to
provide the required coverage, Cyber Risk Protection Platform (CRPP), developed by Happiest Minds helps address the challenge.
The Key benefits include:
> Consolidated internal and external intelligence to contextualize and prioritize
> Tighter integration between data, processes, and products to improve visibility, enable more effective analytics, and action
> Detect, interpret, and respond to events effectively & comprehensively
> Enable cost reduction of incident response and compliance despite an increasing volume of events, incidents, and regulatory actions.
> Real time visibility, to effectively detect, investigate, and adapt to future attacks and remediate
> Comprehensive security and management that narrows the time to detection and resolution from days, weeks, or months to hours, minutes, or even seconds
How we are different
> Integrated threat detection and response across multiple layers of enterprise IT, removing siloed approach to security
> Enhanced visibility and situational awareness across network, end points and cloud
> Tiered approach to address security needs based on threat/risk profile of organization
> Analytics driven framework for better contextualization
> Automated, adaptable for continuous monitoring and response


