Photo Gallery
 |
 |
CyberArk: The Identity Security Company

Additional Info
| Company size | 1,000 - 4,999 employees |
| World Region | North America |
| Website | https://www.cyberark.com/ |
NOMINATION HIGHLIGHTS
With identity-based cyberattacks on the rise (ex: Cisco, Twilio, Cloudflare and Uber), it’s no longer enough to just manage identities – they must be secured. Identity has become the attack surface, making Identity Security critical to building cyber-resilient organizations.
Identity Security combines the strength of identity and access management, identity governance and administration and privileged access management.
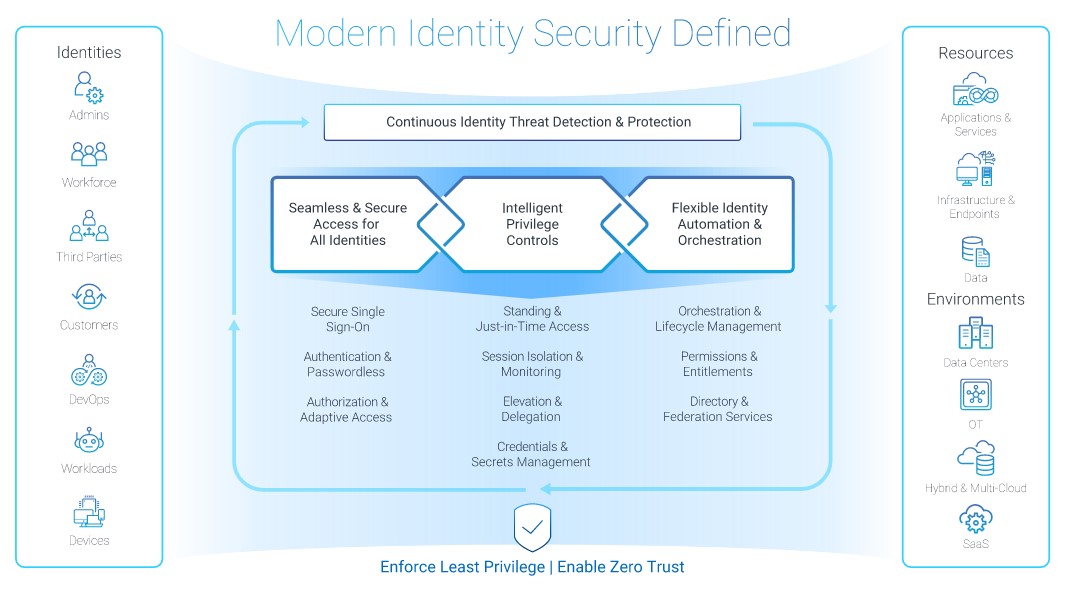
As the global leader in Identity Security, only CyberArk applies intelligent privilege controls to all identities—human and machine—with continuous threat detection and prevention across the entire identity lifecycle, including business applications, distributed workforces, hybrid cloud workloads and DevOps. With CyberArk, businesses can enable Zero Trust and enforce least privilege with complete visibility, ensuring that every identity can securely access any resource from anywhere with a single platform.
The CyberArk Identity Security Platform enables protection of any identity across the widest range of devices from a single, comprehensive platform, helping enterprises achieve heightened protection and enhanced productivity.
To protect the Identity attack surface, CyberArk halts credential-based attacks with privilege controls such as just-in-time (JIT) access, session isolation and monitoring, privilege elevation and delegation, and secrets management. CyberArk adaptive MFA protects against popular techniques like MFA Fatigue with user behavior analytics to detect anomalous behaviors or block user authentication from suspicious IP addresses.
CyberArk is also dedicated to nurturing an ecosystem of cybersecurity innovators with its C3 Technology Alliance, with over 200 market-leading integrations in areas like cloud, IoT and DevSecOps. The company also launched a $30 million global investment fund, CyberArk Ventures, designed to empower cyber disruptors. Additionally, CyberArk launched a series of initiatives to expand channel program features to capitalize on the surge of interest in MSP models and drive value while helping partners grow Identity Security-related business opportunities.
How we are different
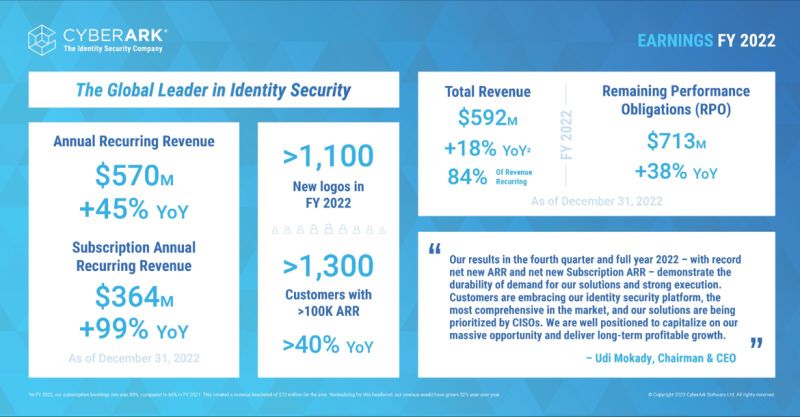
Market Leadership: As a trusted advisor to 8,000+ global organizations, servicing over 50% of the Fortune 500 and over 35% of the Global 2000, CyberArk continues to lead the Identity Security category amid heightened geopolitical and economic pressures. In 2022, the company’s recurring revenue was $498.3M, a 43% year-over-year increase. The company also signed more than 380 new customers in Q4 of 2022 and surpassed 2,750 employees globally. Most importantly, in 2022 CyberArk completed its transition to a subscription-based business, with its bookings mix reaching a new record of 90% in Q4—underscoring customer adoption and expanding use of the platform.
Technology Leadership: The market consistently lists CyberArk as a cybersecurity leader. Last year, it was the only vendor positioned as a Leader in both the 2022 Gartner® Magic Quadrant™ for Access Management and Privileged Access Management reports. CyberArk was also recognized as a leader in KuppingerCole Analysts’ Leadership Compass reports for Passwordless Authentication, and CIEM and Dynamic Resource Entitlement and Access Management (DREAM).
Trend Spotting Leadership - CyberArk heavily invests in R&D to deliver cutting-edge solutions that protect against emerging threats. Influencing product innovation is CyberArk Labs – an elite group of white hat hackers and intelligence experts whose research on emerging attack techniques help shape CyberArk’s product roadmap. CyberArk is the only Identity Security vendor to have a dedicated Labs research team. The team regularly publishes novel research on emerging attack vectors, most recently focusing on how ChatGPT can be manipulated to create malware – driving more than 20 articles worldwide. It also regularly explores common tools used in DevSecOps environments to identify potential weaknesses that could introduce risk to the organization.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



