Photo Gallery
|
|
Cyberbit EDR

Additional Info
| Company | Cyberbit |
| Company size | 100 - 499 employees |
| Website | https://www.cyberbit.com/solutions/endpoint-detection-response/ |
NOMINATION HIGHLIGHTS
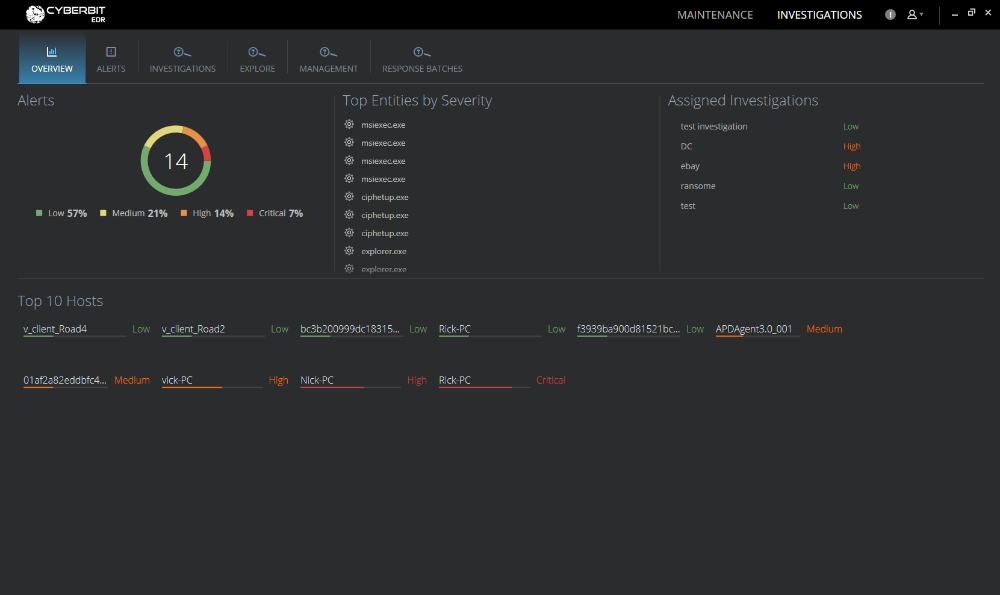
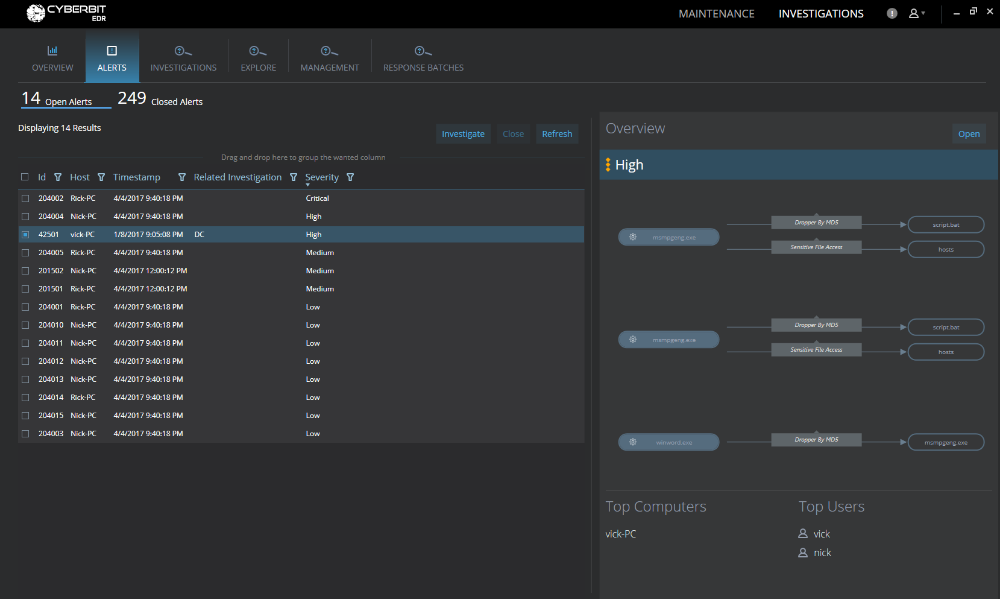
Cyberbit EDR incorporates endpoint detection and response, NGAV and ransomware prevention – all in one agent. The solution combines machine learning and behavioral analytics over big data to allow detection of the most evasive threats, including file-less attacks, while keeping low false positives. Cyberbit EDR does not rely on IOCs for detection, and does not require external connectivity for analysis, response or blocking. All data is analyzed locally, and never sent outside of the organization.
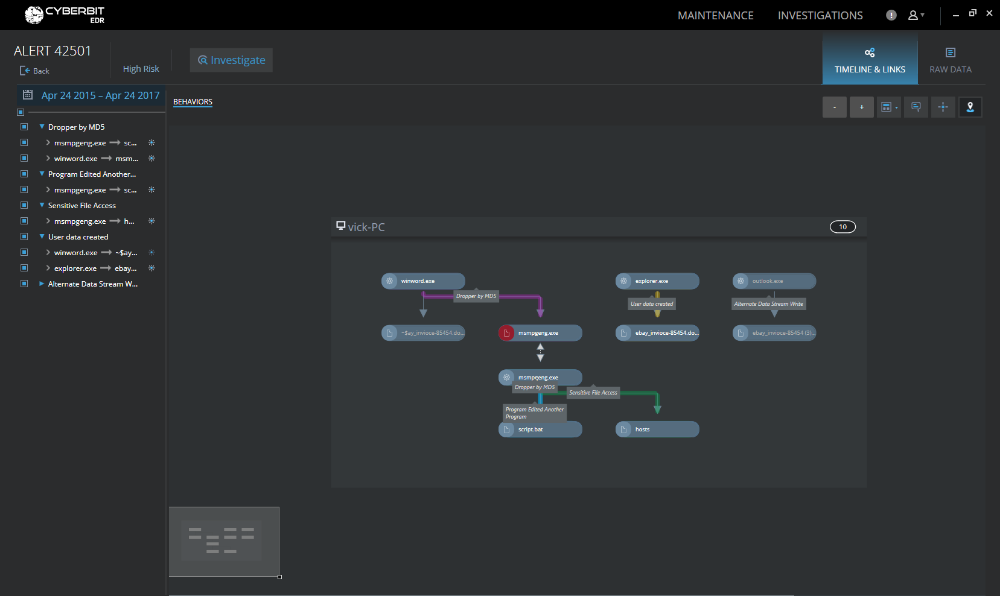
Cyberbit EDR continuously records kernel-level endpoint activity. This data is sent to a big-data repository for behavioral analysis. Behavioral analytics, leveraging expert threat analysis research, together with machine learning algorithms that tailor detection to the specific characteristics of the customer’s network, detect threats and anomalies while minimizing false positive alerts.
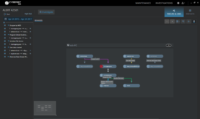
Cyberbit EDR’s detection mechanism is independent of IOCs, able to detect threats that were never seen before. Cyberbit EDR automatically visualizes the attack story in a graph view, saving hours of analyst investigations and facilitating quick identification of root cause and threat propagation. Data stored in the big data repository can also be used for hunting, using natural language.
Remediation and response measures are initiated with a click, supporting a variety of actions to block the threat and allow quick remediation.
Cyberbit EDR is a NGAV that prevents the execution and propagation of malware infection by automatically identifying and blocking unknown and known threats, including ransomware, pre-execution.
Cyberbit Anti-Ransomware blocks known and unknown ransomware from executing and propagating by using advanced deception techniques such as decoys. It automatically prevents file encryption and restores valuable files.
Cyberbit EDR architecture is optimized to provide 3 capabilities in 1 installation. Its open APIs and SDKs allow it to easily integrate to 3rd party tools, while its secured design assures data will be kept safe and untampered, reliable and available.
How we are different
• Blocks ransomware automatically
• Detects sophisticated hidden threats without requiring externally IOCs
• Improves threat visibility and analyst productivity


