Photo Gallery
|
|
Cybereason's Threat Hunting Platform

Additional Info
| Company | Cybereason |
| Company size | 100 - 499 employees |
| Website | https://www.cybereason.com |
NOMINATION HIGHLIGHTS
Threat hunting allows security analysts to identify attacks faster, and minimize damage and the likelihood of business disruption. Yet, for many organizations continuous threat hunting is challenging: many security teams struggle to understand the full scope of an attack in time to contain and respond effectively.
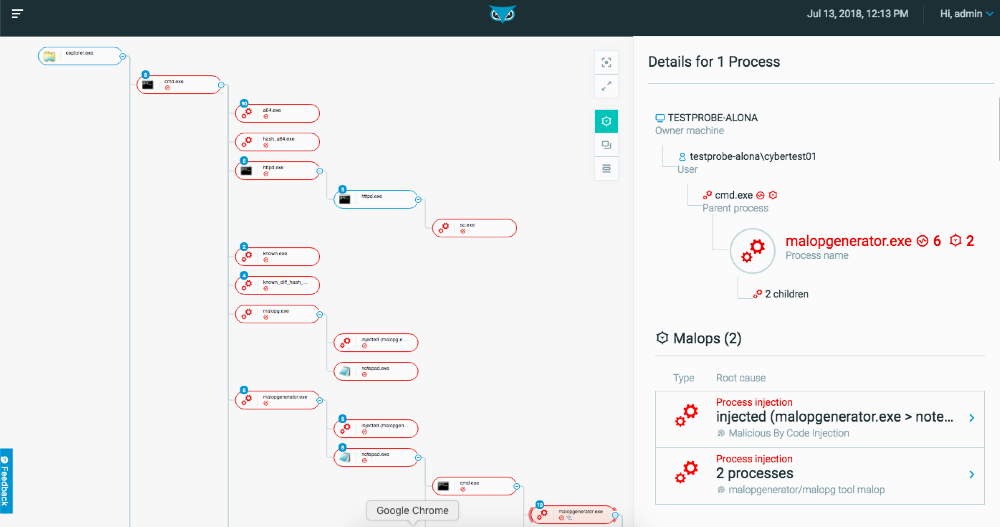
Cybereason’s end-to-end threat hunting solution helps analysts understand the full attack by automatically correlating activity across all machines in an enterprise. This correlation enables defenders to quickly understand the full scope of an attack and easily investigate for behaviors and activities across all endpoints in their environment without the need for complex queries.
Starting with Actionable Data
Cybereason’s Malops™ present customers with actionable data to start hunting. Malops are collections of related suspicious activities that are highly likely part of a security incident. Customers can search for evidence and suspicions tied with Malops™ to see how prevalent they are in their environment.
Empowering the Team To Hunt
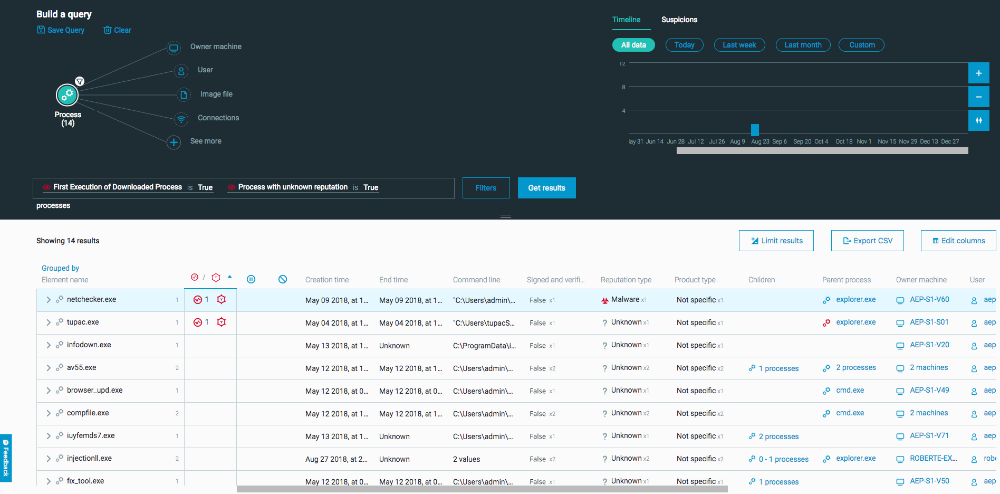
With Cybereason’s query builder, analysts don’t need to learn advanced queries to hunt. Instead, query builder is an interactive hunting tool that lets analysts hunt easily based on attack indicators, threat intelligence, observed behaviors, processes, and more. Furthermore, since each Cybereason customer has their own graph database, query results are instantaneous.
Automating Successful Hunts
The ability to automate hunting processes is critical to reducing the time needed to identify new attacks. Cybereason enables analysts to create custom detection rules and define new logic for triggering Malops™ based on lessons learned from successful hunts. This eliminates the need to always run queries in order to identify malicious activity.
Managed Threat Hunting
Cybereason’s Active Hunting service delivers ongoing threat hunting to customers. Our team of experts develop hunting queries that are informed from threat intelligence data and research, then run them in customer environments to find emerging threats.
How we are different
Unlike competitive solutions in the market, Cybereason was built to empower companies to defend against advanced attacks and find unknown threats in their environment quickly and efficiently. The Cybereason end-to-end threat hunting platform empowers defenders with three unique capabilities in the marketplace:
1) Immediate Visibility Across the Enterprise
The Cybereason platform is built on a Cross-Machine Correlation Engine. This engine performs real-time structuring of all activities and behaviors across machines to build relationships prior to executing queries. Other threat hunting solutions do not automatically correlate activity across all machines, resulting in more manual, time-intensive work.
2) Ease of Launching Investigations & Hunting Campaigns
Hunts based on indicators of an attack, such as specific attacks or behaviors observed on machines are automated with Malops™. Malops™ are actionable alerts that detail all affected machines in a given attack, and while investigating, analysts can launch an investigation to dive deeper into any specific activities and behaviors.
For manual hunts that are based on hypotheses, teams comprised of all skill sets can use Cybereason’s query builder to hunt. Query builder eliminates the need for analysts with advanced syntax skills. Instead, query builder is an interactive hunting tool that lets you hunt easily based on IOCs, threat intelligence, observed behaviors, processes, and more. Furthermore, since each Cybereason customer has their own graph database, query results are instantaneous.
3) The Ability to Respond Quickly
Cybereason allows teams to automate remediation actions by providing several in-platform options. Remediation actions can be executed once across all affected endpoints from a single investigation and remediation console. These include:
Quarantining malware and image files
Killing processes
Isolating machines
Removing registry keys
Running secure PowerShell commands directly to endpoints


