Cybermindr, Continuous Threat Exposure Discovery Platform
Recognized in the Category:
Photo Gallery
 |
 |
Cybermindr, Continuous Threat Exposure Discovery Platform

Additional Info
| Company | CyberMindr |
| Company size | 10 - 49 employees |
| World Region | North America |
| Website | https://www.cybermindr.com |
NOMINATION HIGHLIGHTS
CyberMindr, a SaaS platform for Automated & Continuous Attack Path and Threat Exposure Discovery helps you to proactively identify & assess your attack surface to mitigate associated threats.
Our platform takes a different approach and shows only the validated-vulnerabilities and confirmed attack-paths. The platform performs 15,000+ live checks on the discovered assets and is continuously updated with new live check playbooks based on the ongoing monitoring of 300+ hacker forums to gather intelligence on attackers’ Tactics, Techniques and Procedures (TTPs). This approach to identify “real vulnerabilities” and “confirmed attack paths” helps you to prioritize remediation efforts with limited resources before they are exploited.
Unlike external assessment tools, CyberMindr’s approach combines passive data collection methods like Open-Source Intelligence (OSINT) with active assessment techniques, ensuring no false positives fatigue and offers an accurate representation of cybersecurity posture, helping organizations make informed decisions to prioritize vulnerabilities.
Key features and capabilities of CyberMindr –
Automated & Continuous Attack Path and Threat Exposure Discovery: Proactively identifies and assesses attack surfaces to mitigate associated threats.
Validation of Vulnerabilities and Confirmed Attack Paths: Shows only validated vulnerabilities and confirmed attack paths, aiding in effective prioritization of remediation efforts.
Live Checks and Continuous Updates: Performs 15,000+ live checks on assets, continuously updated with new playbooks based on ongoing monitoring of hacker forums and latest attack TTPs.
Combination of Passive and Active Assessment Techniques: Combines passive data collection methods with active assessment techniques, ensuring accurate cybersecurity posture representation.
Insights into Publicly Exposed Digital Assets: The platform offers comprehensive insights into publicly exposed digital assets, including –
• Asset Enumeration
• Exposure Assessment
• Vulnerability Detection
• Botnet Infections
• Email Security Assessment
CyberMindr aids in identifying, assessing, and mitigating potential security vulnerabilities across an organization’s systems and networks. By proactively discovering these exposures, CyberMindr strengthens an organization’s overall cyber resilience, reducing the risk of breaches and data compromises.
Key Capabilities / Features
CyberMindr offers a comprehensive suite of capabilities designed to enhance cybersecurity posture and threat mitigation:
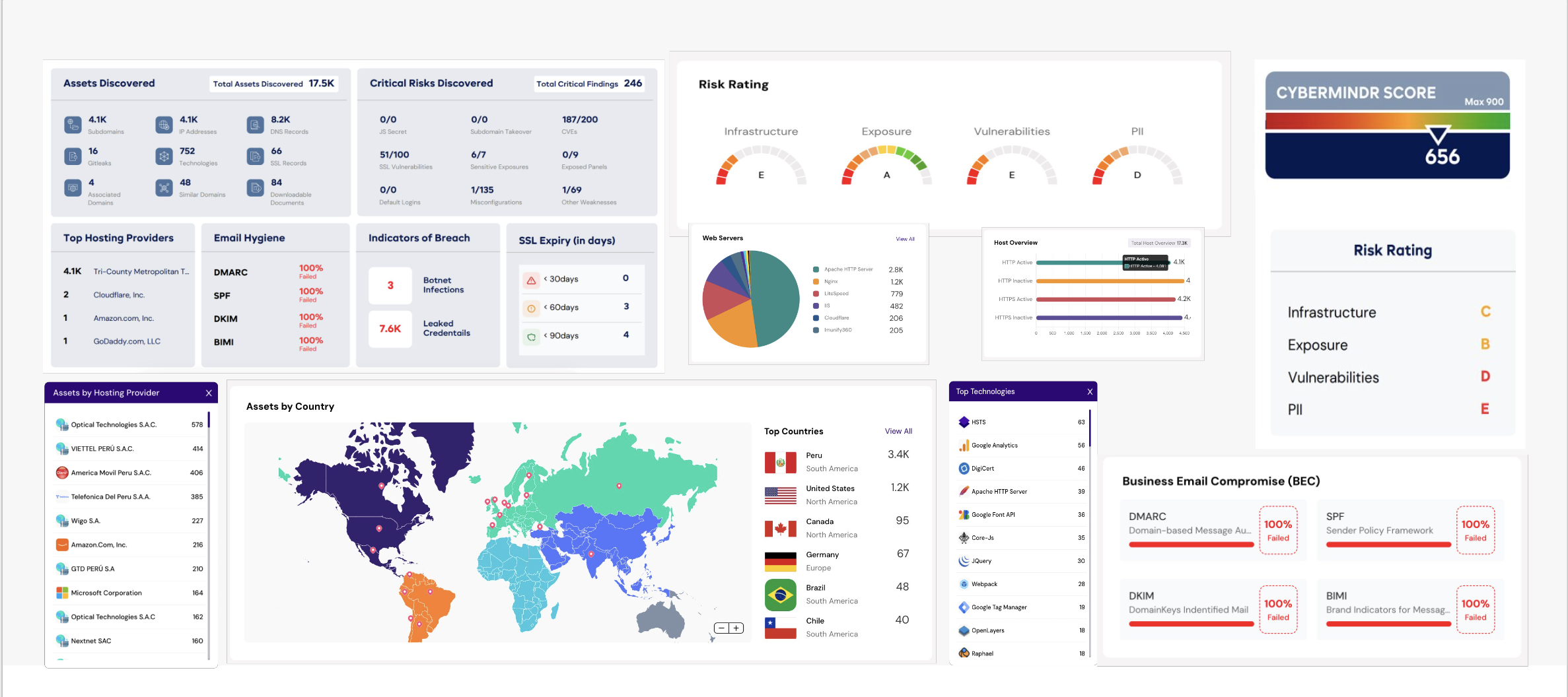
Asset Discovery: Identify and assess various digital assets, including domains, WHOIS registrar details, associated domains, similar domains, subdomains, IP addresses, open ports, risky ports, ASN details, geolocation, technologies used, hosting providers, DNS records, SSL records, and SSL expiry.
Corporate Email Security: Evaluate email security settings, including DMARC, DKIM, SPF, BIMI, and assess risks associated with email gateway service providers.
Concerning Exposures: Detect concerning exposures such as Gitleaks, JavaScript secrets, downloadable documents, and sensitive exposures.
External Detected Vulnerabilities: Identify vulnerabilities such as sub-domain takeovers, CVEs, SSL vulnerabilities, exposed panels, default logins, misconfigurations, and other vulnerabilities. CyberMindr's vulnerability discovery capabilities in this area encompass:
• Subdomain Takeovers Detection: Actively identify subdomains vulnerable to takeover, utilizing active tools to follow DNS pointers and surface vulnerabilities where a host points to an unused service, allowing adversaries to exploit and serve malicious content.
• CVE Identification and Validation: Detect Common Vulnerabilities and Exposures (CVEs) utilizing network-based vulnerability scans, and verify vulnerable software versions while assessing exploitability through safe exploitation attempts.
• SSL Certificate Vulnerability Detection: Flag SSL certificate issues such as weak encryption algorithms or self-signed certificates, impacting the organization's security score when assessed by external parties.
• Exposed Panels and Default Logins Detection: Identify exposed login or management portals, testing for default vendor credentials on discovered portals to enhance security posture by identifying potential unauthorized access points.
• Misconfigurations and Common Weakness Enumeration (CWE) Detection: Identify misconfigurations and deviations from best practices in asset setup, along with detecting Common Weakness Enumerations (CWEs) not tied to any specific vendor, ensuring comprehensive vulnerability detection and mitigation across the organization's infrastructure.
Indicators of Compromise: Identify indicators of compromise such as leaked credentials and botnet leaks.
By leveraging CyberMindr's advanced capabilities, organizations can strengthen their resilience against cyber threats and maintain a secure digital environment.
How we are different
1. Advanced Security Assessment Techniques:
- Performs over 15,000 scripted attacks used by major APT groups worldwide.
- Utilizes logical multistage penetration methods for quick and comprehensive results.
- 100% automated platform leveraging both passive and active scanning techniques for a thorough examination of an organization's digital footprint unlike the traditional attack surface management tools.
2. Predictive Engine and Innovative Scanning Capabilities:
- Predicts assets beyond typical OSINT sources, anticipating additional assets.
- Granular insights into domains, IP addresses, SSL certificates, and external technologies.
- Email security assessment with a focus on critical settings like DMARC, DKIM, SPF, and BIMI.
3. Scoring Matrix and Continuous Evolution:
- Introduces a unique Hacker Score for concise communication of an organization's security posture.
- The score is broken down into security domains, aiding in prioritizing security efforts effectively.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



