Photo Gallery

|

|
CyberX Platform

Additional Info
| Company | CyberX |
| Company size | 50 - 99 employees |
| Website | https://cyberx-labs.com/ |
NOMINATION HIGHLIGHTS
Purpose-built for ICS/SCADA cybersecurity, the CyberX platform incorporates a deep embedded understanding of ICS/SCADA protocols, vulnerabilities, devices, and behaviors that works to detect dangerous malware before it strikes and causes devastating effects to our public and private infrastructure. The platform uses patented, ICS-aware behavioral anomaly detection algorithms to immediately identify ICS-specific assets and network topologies, network and endpoint vulnerabilities, and threats such as malware and zeroday attacks (WannaCry, NotPetya, TRITON, CrashOverride, etc.) — in less than an hour — without relying on rules or signatures, specialized skills, or prior knowledge of the environment.
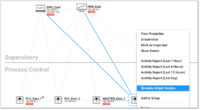
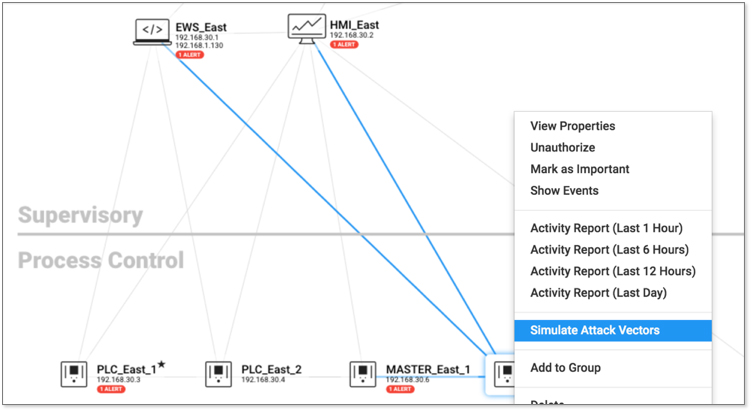
The CyberX platform also enables a unified IT/OT security governance strategy and leverages scarce resources across both IT and OT by natively integrating with existing security operations center (SOC) workflows, security stacks, and over 22 different SCADA/ICS protocols. The platform enables security analysts to perform investigations via a visual interface and workflow, making it easy to see how relationships connect across data sources and throughout complex attack chains. The CyberX platform also allows for real-time alerting and anomaly detection, along with detailed contextual information to aid in investigations and forensics.
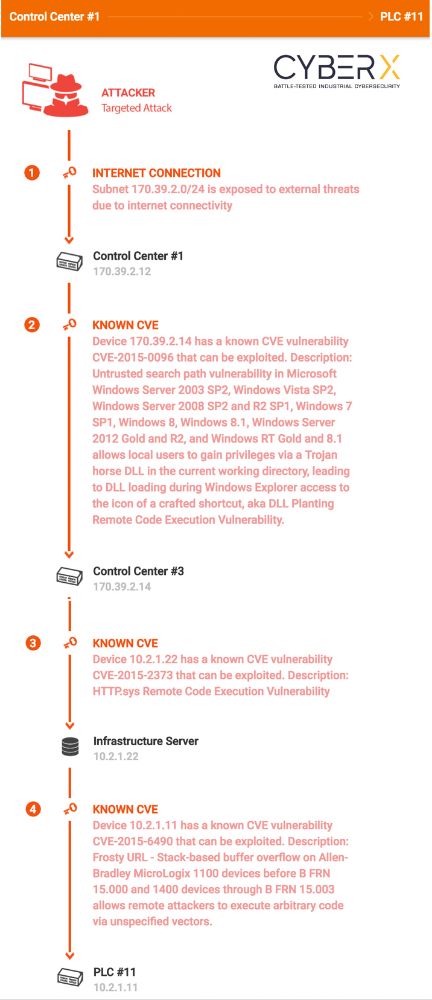
Additionally, CyberX’s automated ICS threat modeling technology predicts the most likely paths of attacks on ICS/SCADA networks, enabling network defenders to prioritize mitigations for their most valuable “crown jewel” assets.
How we are different
-It’s a comprehensive solution incorporating end-to-end capabilities including continuous asset discovery and network topology mapping; risk and vulnerability management; and threat monitoring and response.
-It’s the industry’s most open and interoperable ICS/SCADA cybersecurity platform, integrating with leading products including IBM QRadar, Splunk, ArcSight, LogRhythm, Palo Alto Networks, Checkpoint, ServiceNow, IBM Resilient, and CyberArk. This unified approach to IT/OT security monitoring and governance enables CISOs to effectively address advanced threats across both IT and OT, leverage scarce resources, and remove silos between IT and OT.
-Unique in the industry, CyberX’s integration with Palo Alto Networks and other firewalls automatically creates new firewall policies to block sources of malicious traffic identified by the CyberX platform.


