Photo Gallery
|


|
Cymulate Breach and Attack Simulation


Additional Info
| Company | Cymulate |
| Company size | 100 - 499 employees |
| World Region | Middle East |
| Website | https://cymulate.com/ |
NOMINATION HIGHLIGHTS
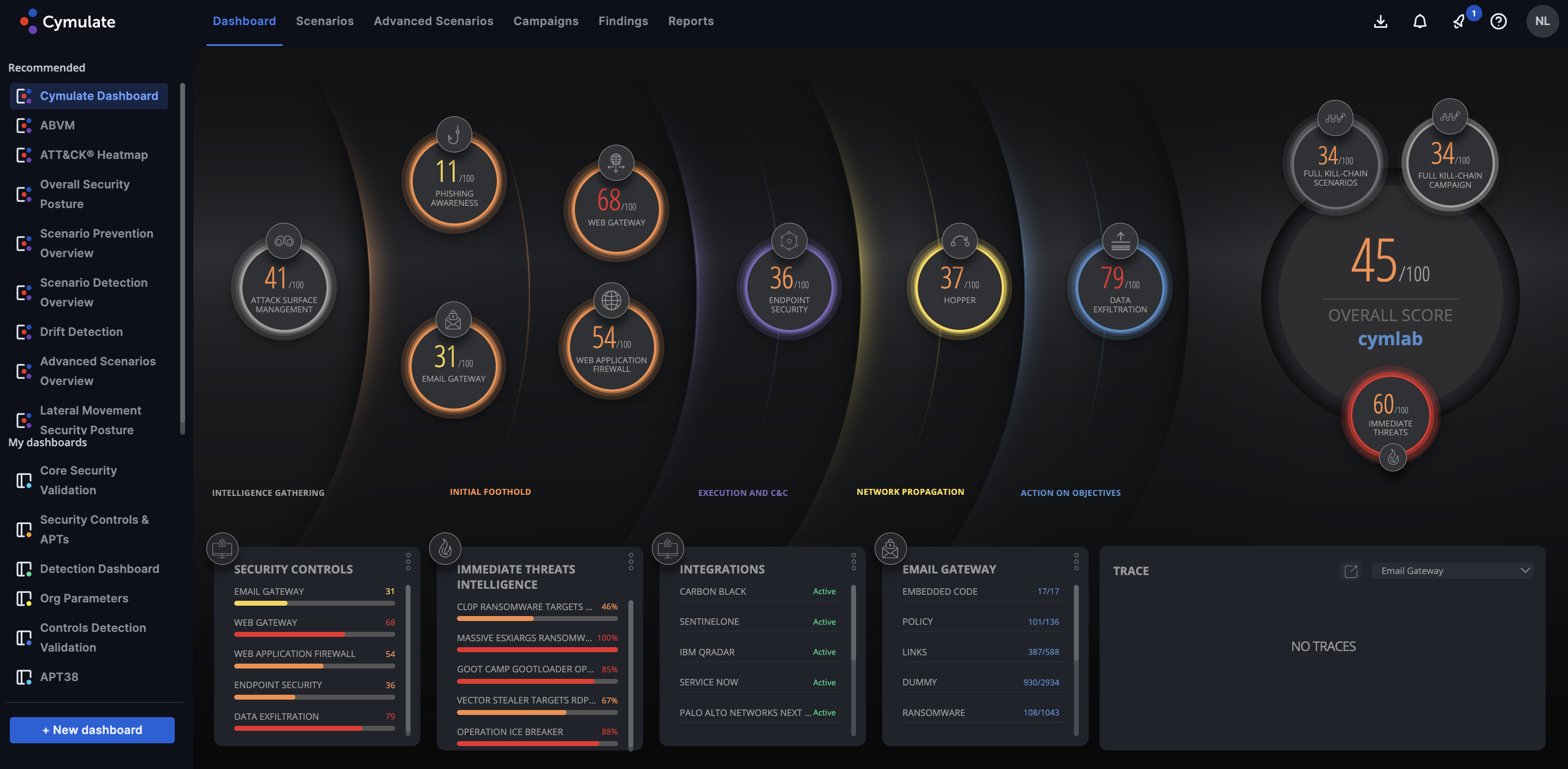
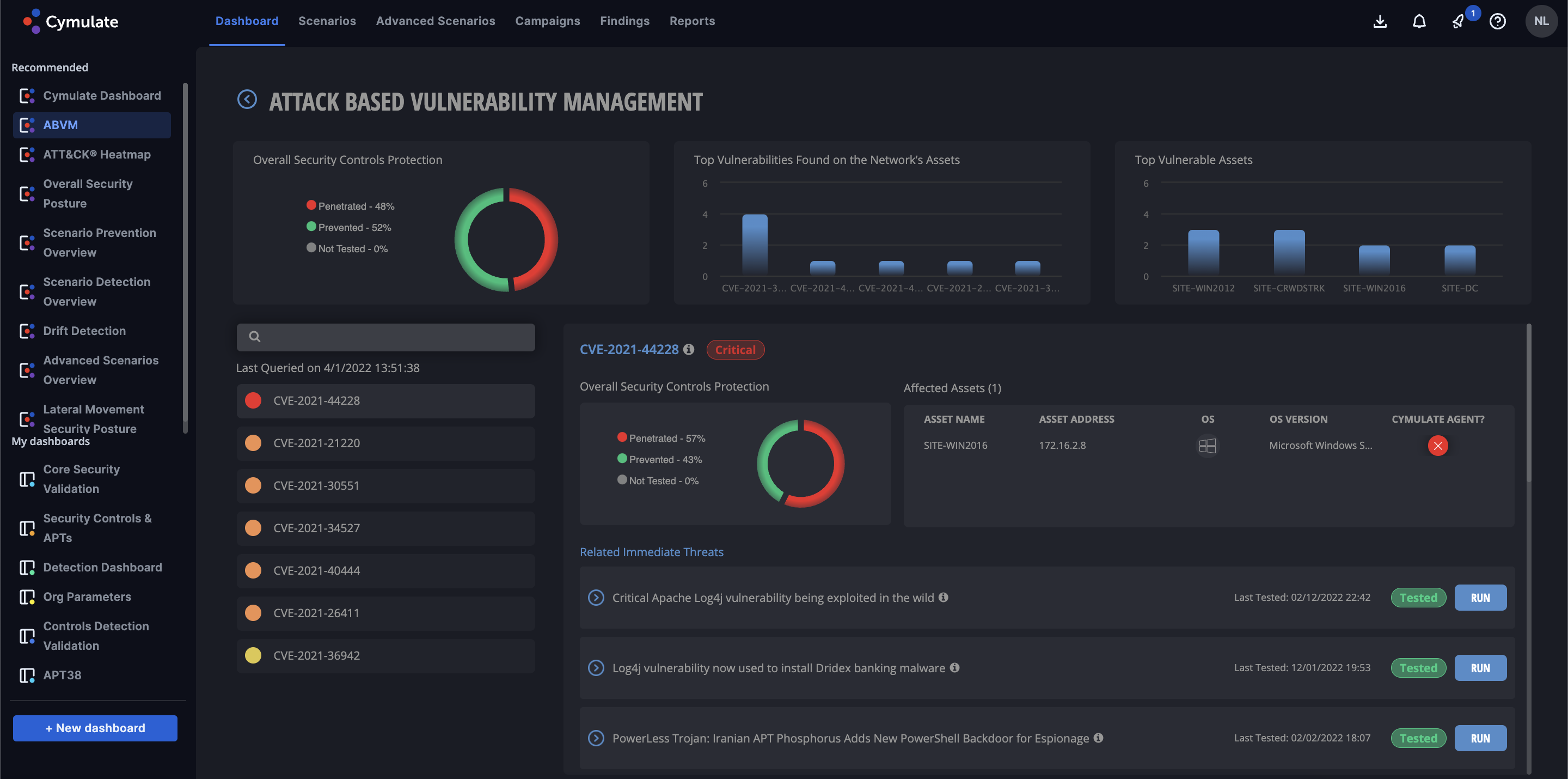
Cymulate provides BAS technologies to perform end-to-end assessment and validation of security controls across the entire kill-chain. By mapping against the MITRE ATT&ACK® framework, in addition to other reference frameworks, Cymulate’s solution allows for organizations of all sizes to challenge, assess, and optimize their cybersecurity resilience in an ever-changing threat landscape. The platform helps security professionals control their environment by delivering out-of-the-box, threat-informed risk assessments with built-in automation and scheduling protocols; while still offering the ability to perform fully custom attacks whenever and wherever necessary. As cybersecurity is an organization-wide concern, Cymulate also provides executive-level reporting automatically; to give business stakeholders the information they require for risk analysis and budgetary justification.
As businesses struggle to manage attack surfaces and validate security controls, these data-driven capabilities significantly improve risk visibility and deliver actionable insights for reducing remediation time. Furthermore, dynamic dashboards provide context by consolidating insights from thousands of attack campaigns and scenarios. The solution empowers security managers to make educated decisions in their cybersecurity strategy, prioritize workloads and reduce risk substantially and quickly.
How we are different
-Cymulate’s platform provides out-of-the-box, expert, and threat intelligence-led risk assessments and is both simple to deploy and use for all maturity levels and constantly updated.
-Cymulate provides an open framework to create and automate red AND purple teaming exercises by generating custom campaigns and advanced attack scenarios tailored to and organization's unique environments and security policies while providing deep technical and higher-level executive reporting.
-Cymulate, deployable within an hour, minimizes resource overhead while enabling security professionals to continuously challenge, validate, and optimize their cyber-security posture end-to-end across the MITRE ATT&CK® framework, ensuring shorter time to remediation.


