Photo Gallery
 |
 |
Defendpoint


Additional Info
| Company | Avecto |
| Company size | 200 employees |
| Website | http://www.avecto.com |
NOMINATION HIGHLIGHTS
Avecto’s Defendpoint software offers a world first in endpoint security for both Windows and Macs. A multi-layered prevention engine, Defendpoint is the only security solution to combine three proactive technologies to stop cyber attacks.
• Privilege management: allows you to achieve least privilege by removing admin rights, immediately mitigating 85% of critical vulnerabilities reported by Microsoft without restricting user productivity.
• Application control: the days of complex whitelists based on thousands of hash rules are gone, making whitelisting finally achievable. Intelligent yet simple rules and tight integration with privilege management makes it possible to stop malware from ever executing on the endpoint.
• Content isolation: all untrusted web content, internet downloads and email attachments are automatically isolated in a secure container. Even trusted documents such as Word or PowerPoint are protected – ensuring malware can never reach your data.
Unlike other products on the market, Defendpoint takes a proactive approach to minimize risk without relying on detection. This approach provides solid security foundations and does not diminish in effectiveness.
Security never comes at the expense of the end user experience. Comprehensive messages to replace native Windows UAC prompts and customizable options such as challenge & response codes to allow users to request access to apps they need ensures businesses can strike a balance between security and usability.
The product’s adaptable architecture makes it simpler and smarter to implement – it can be managed via Microsoft Active Directory Group Policy or McAfee ePO or via Avecto’s own cloud-based platform (iC3), making it scalable and manageable across the largest enterprises with no additional investment in infrastructure required.
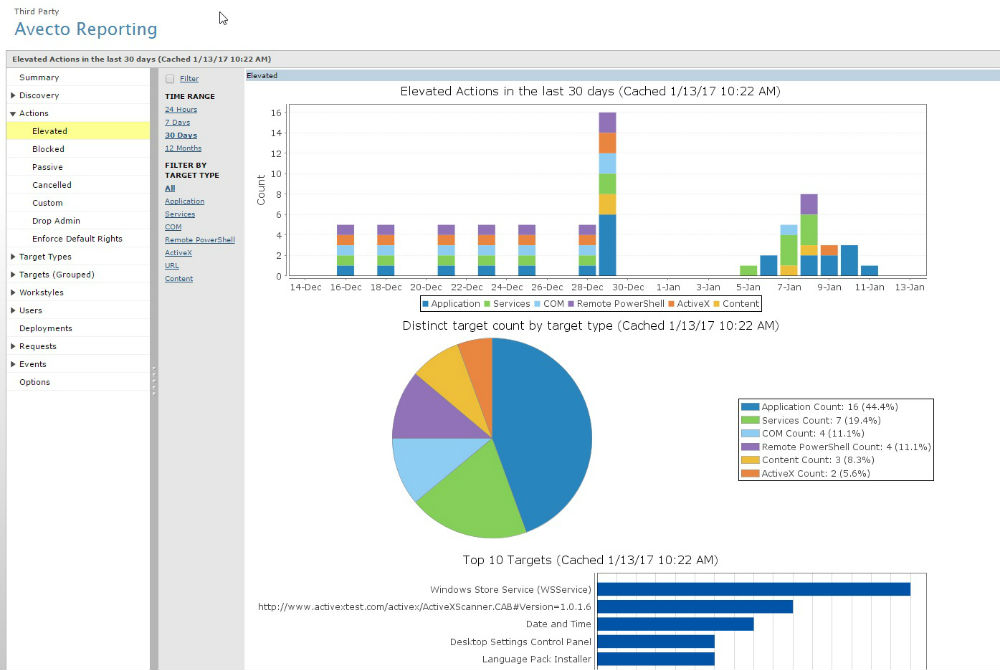
Defendpoint’s integrated enterprise reporting capability enables visibility and control for those managing the solution, with trend reporting to demonstrate compliance as well as detailed dashboards providing intelligence to make informed decisions.
How we are different
• A ground-breaking 3-step approach to endpoint security to stop external and internal attacks
• Seamless user experience with no productivity impact
• Over 8 million endpoints protected across some of the world’s biggest companies spanning finance, manufacturing, retail, aerospace and defense and many more.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



