Photo Gallery
 |
 |
DocCipher

Additional Info
| Company | CrimsonLogic Pte Ltd |
| Company size | 1,000 - 4,999 employees |
| Website | http://www.crimsonlogic.com |
NOMINATION HIGHLIGHTS
DocCipher is an award-winning security solution that safeguards digital documents against forgery, counterfeiting, and information leakage.
DocCipher encloses your digital documents in a secure, encrypted digital envelope. This places technological protection measures on your documents for you to enforce your own policies and restrictions to control document usage.
All recipient information is securely embedded within the documents. To access the protected document, the intended recipient has to use DocCipher Reader, an application which authenticates, authorizes, decrypts and renders the documents for further use.
DocCipher adopts a comprehensive three-pronged approach of security, protection, and control to ensure the authenticity and integrity of your documents.
The Security features shield digital documents from external threats such as unauthorized modification and access to sensitive information.
• Secret Key Encryption: Documents are encrypted to prevent unauthorized access and modification using AES 256-bit keys and PKI technology.
• Audit Trail: All actions performed are tracked to identify possible data breaches.
The Protection features focus on enhancing digital documents to prevent any possible compromise of information.
• Anti-Forgery Barriers: Documents are protected from forgery using anti-forgery features, including SecureCODE. Using the SecureCODE Verifier mobile app, recipients can scan the code to verify the authenticity of documents.
• Anti-Counterfeit Barriers: A multitude of anti-copy barriers including Optical Watermarks, micro and macro-prints are discreetly embedded. This makes it hard for counterfeiters to illegitimately reproduce your documents.
The Control features ensure that only intended recipients gain access to your documents. Our solution offers a myriad of customizable and granular settings according to your needs.
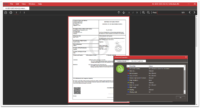
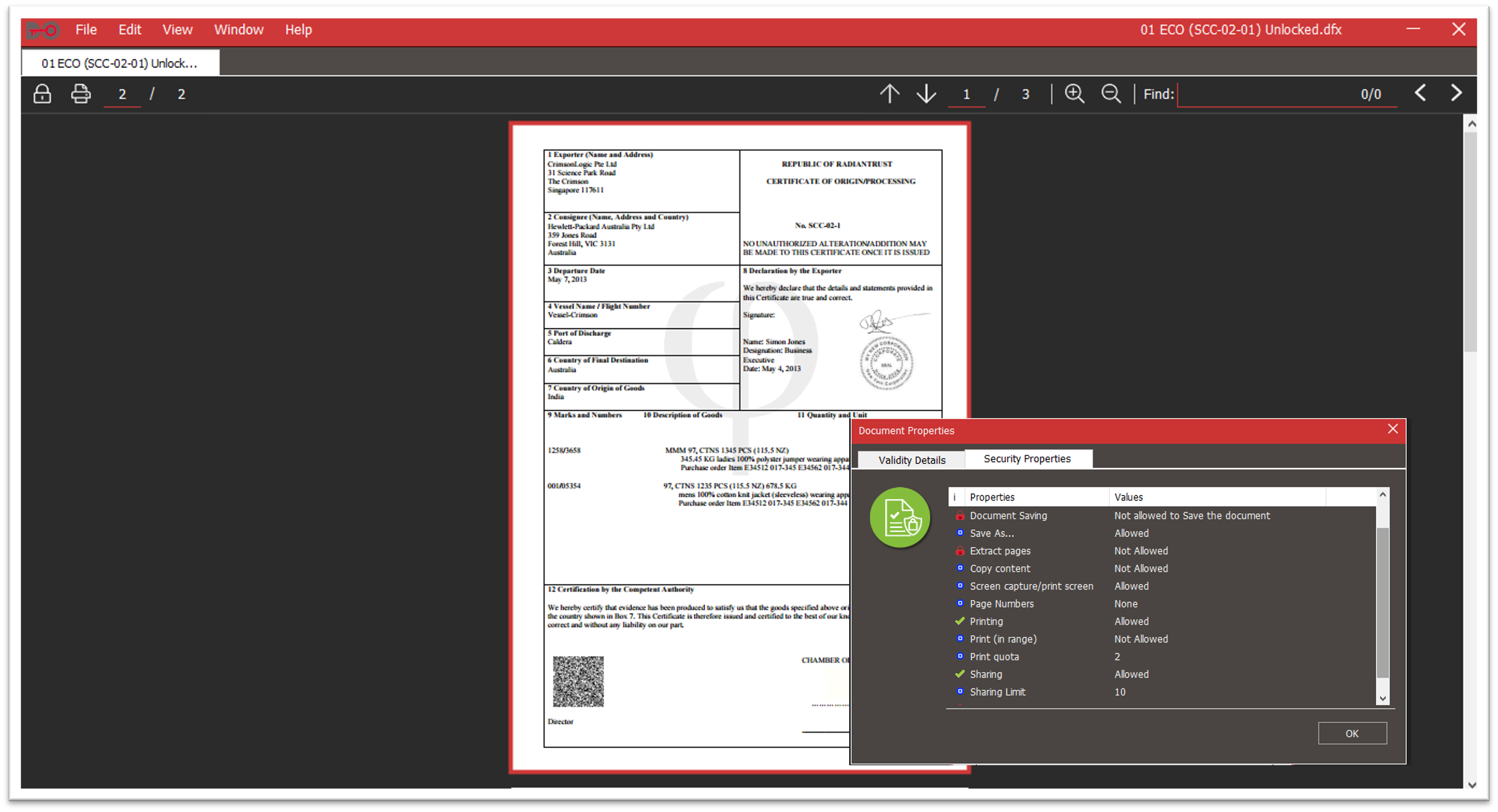
• Document Rights Management: Recipients can be prevented from unauthorized redistribution, content copying, printing or screen capturing documents.
• Document Access and Validity Controls: Documents can be set to expire, remotely revoked, or automatically deleted. The DocCipher Viewer also constantly monitors these files. Once document access has been rendered invalid, they can no longer be accessed.
How we are different
1. Innovative Approach
DocCipher’s unique three-pronged approach of security, protection and control is designed to provide a one-stop digital security solution for organizations. The multiple layers of security and advanced encryption technologies are employed to safeguard document authenticity, regardless of where they are stored (data-at-rest) or how they are delivered (data-in-transit). This allows organizations to seamlessly adapt DocCipher into their digital transformation plans.
2. Effective Security
DocCipher ensures documents are secured to prevent unauthorised access and modification using advanced cryptographic technologies such as AES 256-bit keys and PKI technology. These are the strongest industry-adopted and government-approved algorithms for encrypting data.
DocCipher is also on-demand, and its security features are dynamically generated using document-specific data to prevent unauthorized personnel from forging or counterfeiting your documents.
3. Complements Physical Document Security
DocCipher restricts the printing of a document and can control the number of copies that can be printed. This helps to prevent the proliferation of original documents by mitigating origination attacks.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



