Photo Gallery
|
DTEX InTERCEPT™

Additional Info
| Company | DTEX Systems |
| Company size | 100 - 499 employees |
| World Region | North America |
| Website | https://www.dtexsystems.com |
NOMINATION HIGHLIGHTS
More than 200 of the world’s largest enterprises, governments and forward-thinking organizations leverage DTEX InTERCEPT™ to better understand their workforce, protect their data, and make human-centric operational investments by bringing together the capabilities of next-generation behavioral Data Loss Prevention, User Behavior Analytics, and User Activity Monitoring in a single, light-weight platform that ensures privacy and scalability by design. This doesn’t include the users leveraging the InTERCEPT platform through its strategic partnerships with CrowdStrike, Carahsoft, Splunk, GuidePoint Security, Insider Threat Defense Group, Optiv, Consortium Networks, and more.
Key Capabilities / Features
Increased visibility into user behavior and actions is critical to thwarting insider threats and mitigating preventable risks, especially as modern enterprises grapple with increased threat activity from nation-states exploiting corporate negligence and AI to socially engineer their way into organizations.
The biggest problem with legacy UEBA solutions is that they rely solely on interpreting log files and Windows® events, which are flawed data sources for capturing user behavior. Log files are difficult to implement and manage, requiring a significant amount of manpower to configure, collect, maintain, and interpret. Plus, they don’t provide the level of visibility required to mitigate common user attacks before damage has occurred.
DTEX InTERCEPT™ is helping hundreds of organizations worldwide better understand their workforce, protect their data, and make human-centric operational investments by bringing together the capabilities of next-generation behavioral Data Loss Prevention, User Behavior Analytics, and User Activity Monitoring in a single, light-weight platform that ensures privacy and scalability by design.
Unlike legacy UEBA solutions, DTEX InTERCEPT doesn’t rely on any Operating System or external logs. Instead, user visibility is achieved by monitoring user actions directly on the endpoint. This is accomplished by creating user-based metadata that includes detailed information that isn’t available from external log sources, providing real-time detection capabilities to identify actionable risks – regardless of whether the user is on a corporate network. DTEX then enriches these datasets to augment, corroborate, or potentially replace the requirement for additional log collection, delivering the behavioral context and intelligence needed to escalate and remediate an event before malicious insiders attack or data exfiltration occurs.
Recent enhancements to InTERCEPT include the launch of the DTEX Ai³ Risk Assistant, a new generative assistant that leverages DTEX’s unique approach to data collection and behavioral enrichment to fast-track effective insider investigations and decision-making without infringing on employee privacy.
How we are different
DTEX InTERCEPT™ for UEBA extends beyond the capabilities of legacy solutions in the following key areas:
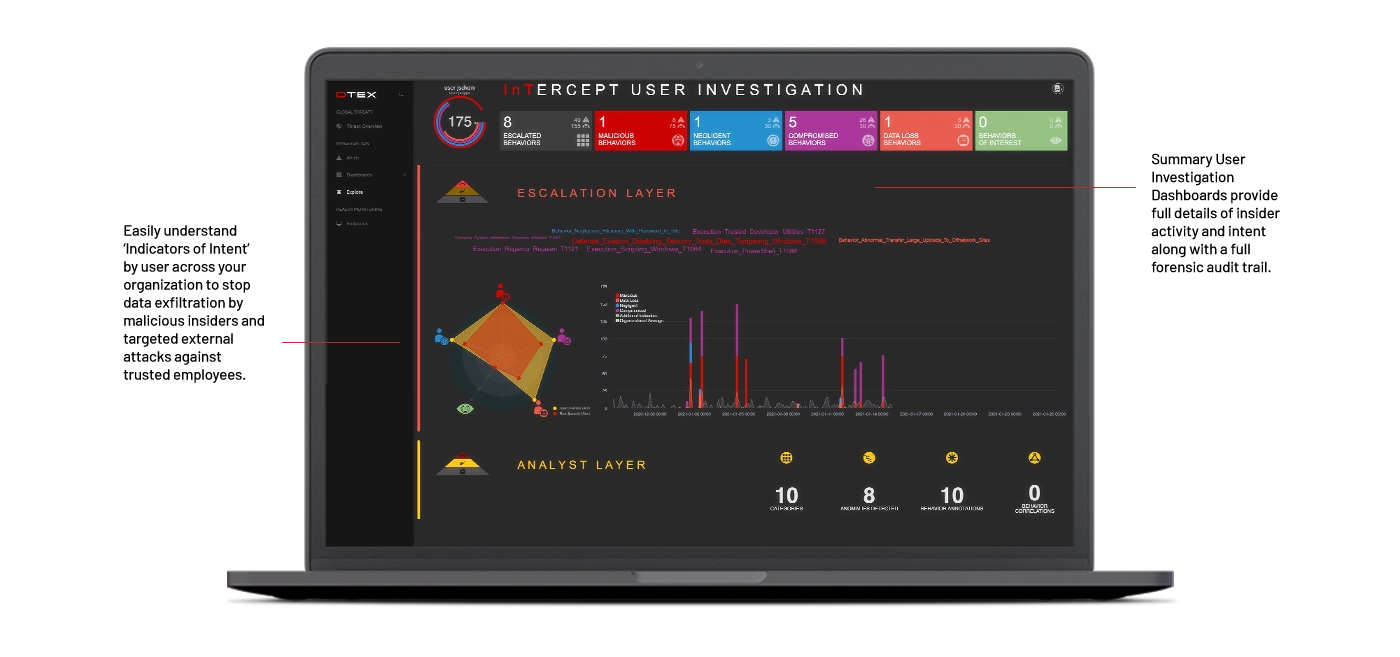
-- File Lineage Forensics & Auditing: Most malicious actions look like legitimate business activities—downloading files, copying and pasting data, using screenshots, compressing files, and sharing sensitive information. DTEX InTERCEPT delivers a full audit history detailing file activity to enable a real-time, contextual understanding of the severity of ‘indicators of intent’ that precede a data loss event. It delivers a full audit trail of who is involved and when each file is created, modified, aggregated, obfuscated, archived, encrypted, or deleted. These added attributes provide a clear distinction between normal activity and true data loss scenarios, eliminating confusion caused by noisy alerts.
-- Risk-Adaptive Data Protection: DTEX InTERCEP protects sensitive data and IP from leaving an organization with multiple, highly accurate and dynamic enforcement capabilities. Data loss is prevented intelligently when a user’s behavioral risk score exceeds an organization’s threshold by blocking specific application processes and network connections that are not part of normal or approved workflows. This includes blocking FTP, large files in email, and access to certain cloud services. Additionally, SOC teams and analysts can remotely remove a user’s credentials and lock them out of their device. These risk-based blocking features best meet the requirements of today’s distributed workforce, reduce operational overhead, and eliminate false positives.
-- Cloud Native Architecture & Interoperability: DTEX InTERCEPT’s cloud-native platform is delivering more value at a lower cost with proven near-zero impact to endpoints and the network, ensuring that the organization can focus on the actionable outputs rather than the scalability issues, configuration and maintenance overhead, and spiraling deployment and services costs commonly associated with tradition endpoint DLP, NGAV, IAM, and UEBA solutions



