Photo Gallery
 |

 |
E8 Security Fusion Platform 2.2

Additional Info
| Company | E8 Security |
| Company size | 10 - 49 employees |
| Website | http://www.e8security.com |
NOMINATION HIGHLIGHTS
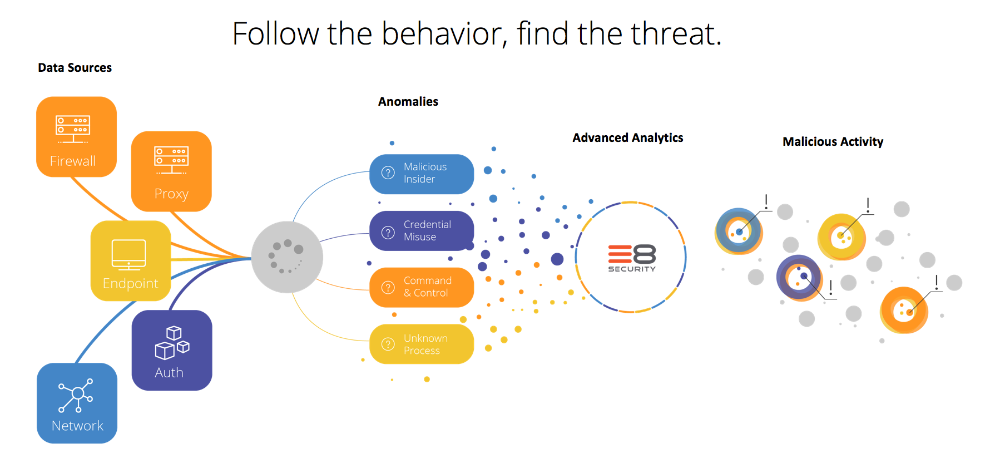
E8 Security’s Fusion Platform addresses a significant void in the Security Operations Center (SOC). The world of rule-based and signature-based threat detection is no longer sufficient to stay ahead of the heavy influx of data breaches. A threat detection machine should think like the human hackers they are meant to track.
The Fusion Platform uses completely unstructured, self-learning detection to better detect the unknown threats lurking within an organization, such as targeted malware, stolen credentials, and insider threats.
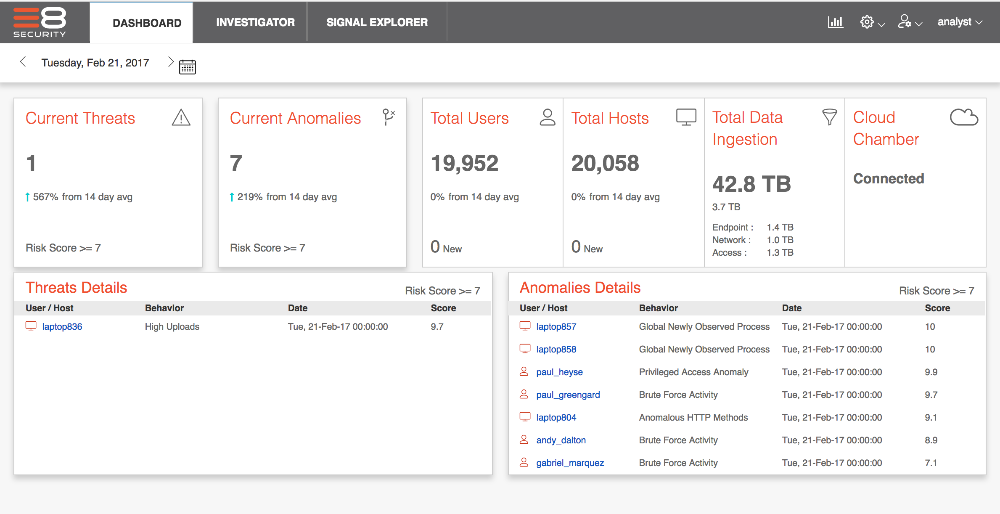
Security analysts can spend on average up to 20 minutes attempting to manually identify the user or device that spawned an alert – with the Fusion Platform, analysts get this time back by more automatically associating IP addresses to the correct device and person using it.
Being able to detect lateral movement has always been a struggle for SOC teams. The Fusion Platform looks actively identifies when credentials are used on machine that isn’t theirs, and tracks the access pattern across multiple hosts so SOC teams know exactly where to focus incident response actions.
Another bottleneck analysts struggle with is prioritizing alerts. The issue is rooted in identifying which alerts are more critical than others and streamlining workflow so that no two analysts duplicate efforts to address the same threat. The Fusion Platform categorizes threats based on connected network, user, and endpoint behaviors inside an organization, so the analyst has the right context to take swift action depending on the severity of the alert.
How we are different
It is difficult to pinpoint the differences in today’s UEBA solutions, as they all claim to have a big data platform, offer flexible deployment, and use some form of machine learning instead of rules and signatures. Here’s what sets E8 Security apart.
• Most UEBA vendors will gloss over the fact that their products can’t stand on their own. They require network sensors, agents, or log decoders deployed within their customer networks to function properly. The E8 Security Fusion Platform doesn’t need any of these. It takes forwarded logs directly from each data source, making it easy to set up and start running, so SOC teams don’t have to re-architect their networks or deploy and maintain yet another agent (read: herd cats).
• Others considered part of the UEBA space primarily focus on user behavior; E8 Security keeps a holistic approach to security by analyzing user, network and endpoint behavior. While user behavior is a critical aspect to unknown threat detection, it must be tied to what endpoints and the network are doing for analysts to truly identify a variety of threats, especially targeted attacks. The Fusion Platform provides that visibility by analyzing and then connecting user, network, and endpoint behavior.
• The E8 Security Fusion Platform doesn’t just ingest and regurgitate data from different sources — it tells you something you don’t know about your data. It’s the only one of its kind that saves precious time by connecting each behavior to a user and host, regardless of changes in IP address. Its differentiator lies in the analytics it runs on all the data it ingests to tie behaviors together for true visibility. The Fusion Platform produces high fidelity information and surfaces to analysts the kill-chain stages in action.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



