Photo Gallery
 |
EclecticIQ Platform

Additional Info
| Company | EclecticIQ |
| Company size | 100 - 499 employees |
| Website | http://www.eclecticiq.com |
NOMINATION HIGHLIGHTS
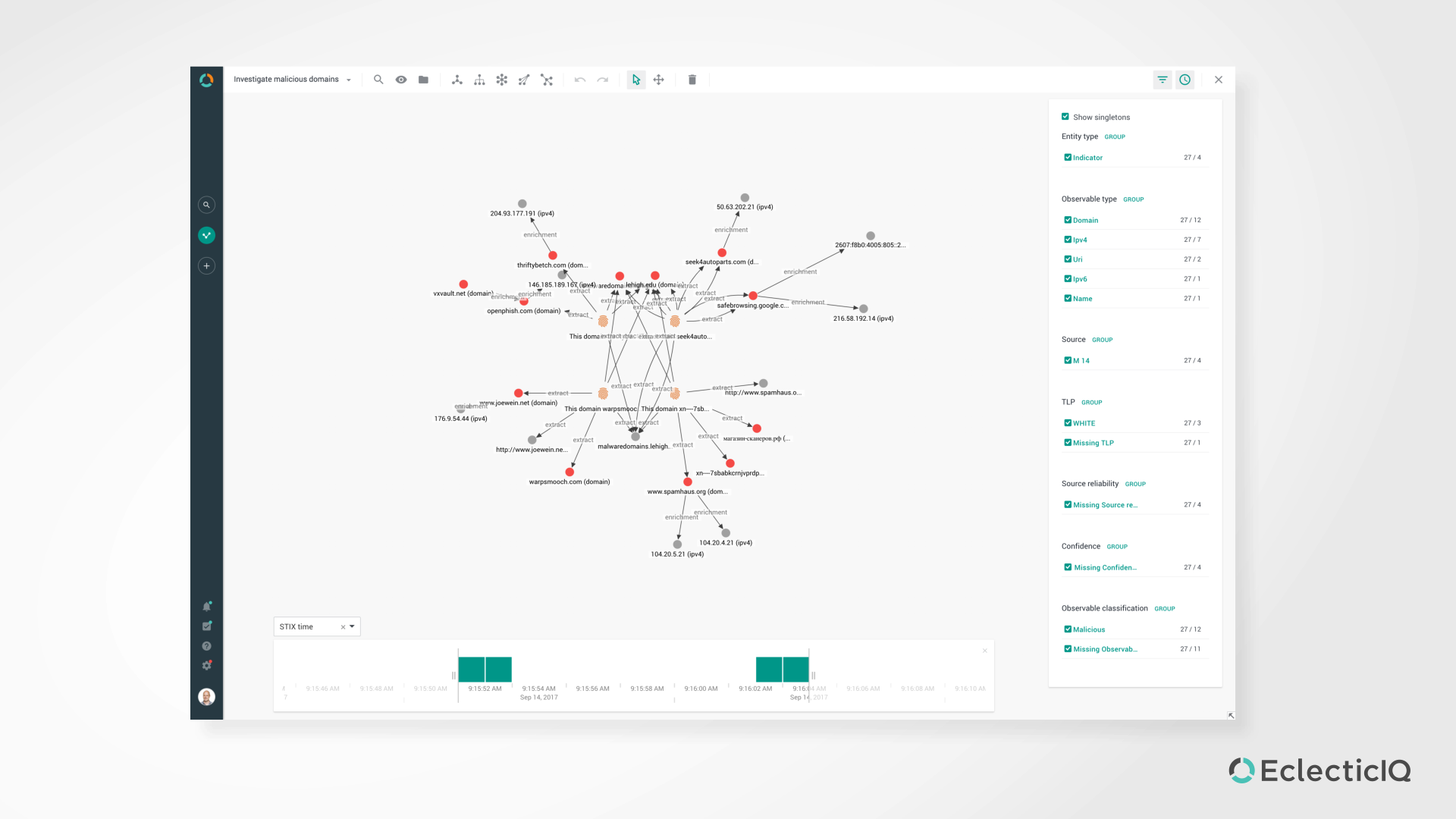
EclecticIQ Platform is a Threat Intelligence Platform (TIP), enabling organizations to align their defense tactics and strategies with the actual and future threat landscape.
It creates business value for customers not only by processing data (i.e. IOCs/IOAs) thereby improving defenses and responses, but also by creating intelligence (i.e. context and forward-looking understanding) to anticipate threats, inform security investments, and define risk mitigation strategies.
From a high-level feature perspective, EclecticIQ Platform enables customers to:
1. Seamlessly aggregate large volumes of heterogeneous intelligence and data,
2. Process them through enrichment, curation and graph-based investigations,
3. Disseminate the resulting information into security controls (through native integrations) and to humans (through in-platform intelligence report editing).
Point 1 and 3 are somewhat standard to any TIP with little room for differentiation, whereas point 2 is unique to EclecticIQ Platform and reflects its core value of being analyst-centric.
Furthermore, customers leverage EclecticIQ Platform to:
1. Anticipate future threats; inform security tactics and strategies
Our customers’ analysts can now identify threats, actors, and tactics that are active in their sector. Then, they deploy those tactics and their related IOCs to machines, humans and processes to ensure future detections.
2. Detect threats that are already active in their infrastructures
Some cybercrime goes through undetected. Once the intelligence on those campaigns is made available, our platform helps customers hunt for those threats through SIEM and SOAR integrations within a SOC.
3. Remediate incidents rationally through risk-based prioritization
Incident response teams can only investigate a fraction of their daily incidents. Our TIP allows for intelligence-led prioritization of remediation, improving both cost- and security-efficiency.
From a business standpoint, our customers routinely use our TIP to:
1. Prioritize security investments based on actual threat exposure.
2. Enrich existing resources such as SOCs to improve value.
How we are different
Analyst-Centric Approach - Uniquely analyst-centric, EclecticIQ Platform is singular in its capabilities to empower analysts into understanding context and creating intelligence out of data & IOCs. Our best-in-class graph capabilities dramatically accelerate human investigations and allow users to connect seemingly distant dots into a bigger picture, hence intuitively transforming data into context and intelligence. In-platform intelligence reports editor allows users to create human-readable intelligence at tactical & strategical levels. It automatically packages these reports with relevant technical data such as IOCs & TTPs. Furthermore, our support of STIX is unparalleled. We don’t stop at mere compatibility: being STIX native, no information is being neglected or lost when processed through our platform.
Elaborate Sharing Capabilities - Sharing is a key element of cyber threat analysis. Release 2.3 focuses on just that, by providing enhanced collaboration within EclecticIQ Platform and delegated administrative responsibilities for groups. The updated capabilities for workspaces give analysts more control over the visibility of the workspace and its contents. This lets them work together with others in a private setting. Analysts can control who they collaborate with by adding groups as collaborators next to single users. This functionality not only boosts cooperation among analysts, but the organization is assured that confidentiality is more easily protected at a granular level
Enhanced Data Retention Management Capabilities - EclecticIQ Platform provides enhanced data retention management capabilities. With the new release system, administrators can automatically purge threat intelligence by creating retention policies, in accordance with their organizational policies. The automated deletion of threat intelligence makes it simpler to remove irrelevant information and only retain the intelligence you need. This capability adds more granularity and flexibility to organizations' GDPR strategies.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



