Photo Gallery
 |
 |
Eclypsium

Additional Info
| Company size | 50 - 99 employees |
| World Region | North America |
| Website | https://eclypsium.com/ |
NOMINATION HIGHLIGHTS
Eclypsium is the first vendor in the security market to deliver device security that is effective down to the firmware and hardware level. Traditional security technologies focus on securing systems at the operating system, networking, or application layer. But these solutions leave a gaping hole when it comes to addressing hardware and firmware. And once compromised, this blind spot allows attackers to subvert traditional security controls and persist undetected, leaving organizations exposed to device tampering, ransomware, and data breaches.
Eclypsium is unique among security companies in providing a solution that protects the foundation of enterprise infrastructure, working below the operating system level to control risk and stop threats to the hardware and firmware inside of laptops, servers, and network infrastructure.
That’s more important than ever in 2020, with the shift to remote work moving employees beyond the traditional protections of the corporate network and attacks at the firmware level proliferating. In the past year widespread attacks on VPNs exploited firmware vulnerabilities, new UEFI implants were discovered in the wild, and the prolific TrickBot malware team began targeting firmware. Meanwhile, the SolarWinds Orion SUNBURST campaign revealed the danger of stealthy supply chain attacks.
That’s why global financial services firms, critical infrastructure providers, leading manufacturers, and the US federal government have turned to Eclypsium. Our comprehensive cloud-based platform protects laptops, servers, and networking equipment down to the firmware and hardware level with security capabilities ranging from basic device health and patching at scale to protection from the most persistent and stealthiest threats. We provide the most complete defense against firmware attacks available – enabling organizations to see and manage risk across enterprise devices and stop active threats from device-level implants and backdoors in the supply chain and in operations.
How we are different
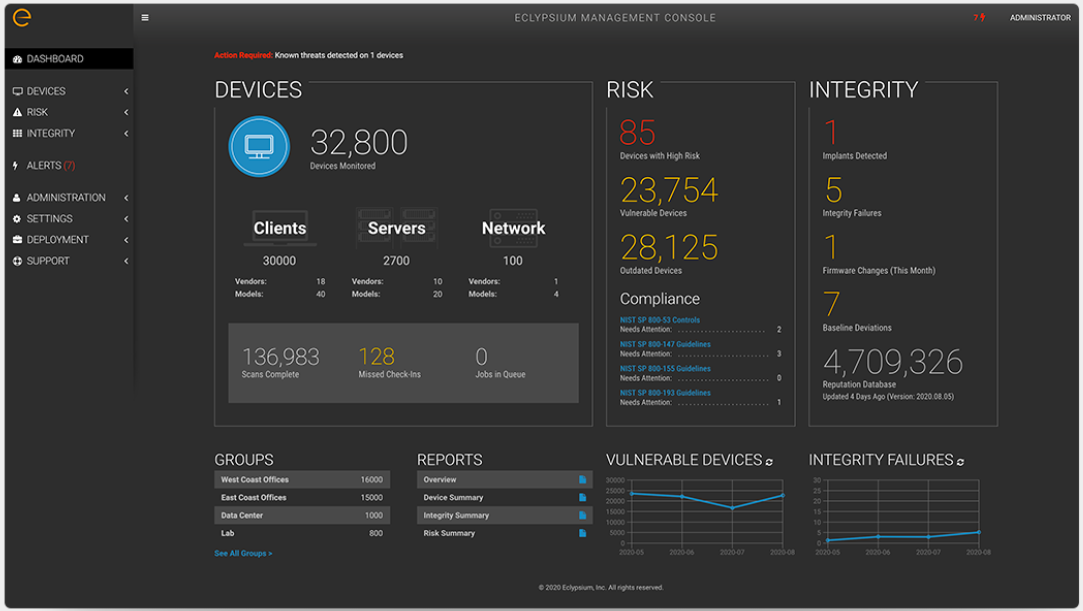
THE MOST COMPREHENSIVE SOLUTION FOR ENTERPRISE DEVICE PROTECTION. Eclypsium provides the most complete solution for protecting your organization from threats down to the firmware level. Our platform provides full visibility into the firmware running on all the key components of your laptops, servers, and network devices. At a glance, you’ll see if there are implants or backdoors in your firmware, if it’s vulnerable to known threats, or if it’s just out of date and in need of patching. You’ll get expert guidance on the severity of vulnerabilities, and links to the latest firmware updates so that you can mitigate threats and protect your assets.
THE INDUSTRY’S LARGEST GLOBAL FIRMWARE REPUTATION DATABASE.
Unlike traditional software, firmware should remain predictable and in “known good” states. The Eclypsium Platform checks firmware against millions of firmware hashes across dozens of enterprise hardware vendors to identify changes to baselines, find outdated firmware, and expose tampering. Eclypsium’s world-class firmware security researcher team leads the industry in identifying threats and vulnerabilities that impact enterprise devices. Their insights power the Eclypsium Platform, putting you ahead of the curve on firmware security.
BROADEST COVERAGE OF FIRMWARE RISKS AND THREATS.
Virtually every component within a modern device has its own firmware that can be compromised in an attack. Eclypsium extends visibility and protection to all the components that make up this internal attack surface including processors, network interface cards, UEFI and EFI firmware, Baseboard Management Controllers (BMCs), Intel Security Management Engine, Trusted Platform Modules, and more. This reach and level of granularity ensure visibility into areas most enterprises cannot see, exposing risk due to vulnerabilities and misconfigurations, unpatched firmware, and compromise from implants and backdoors.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



