Photo Gallery
|
Eclypsium Supply Chain Security Platform

Additional Info
| Company | Eclypsium |
| Company size | 50 - 99 employees |
| World Region | North America |
| Website | https://eclypsium.com/ |
NOMINATION HIGHLIGHTS
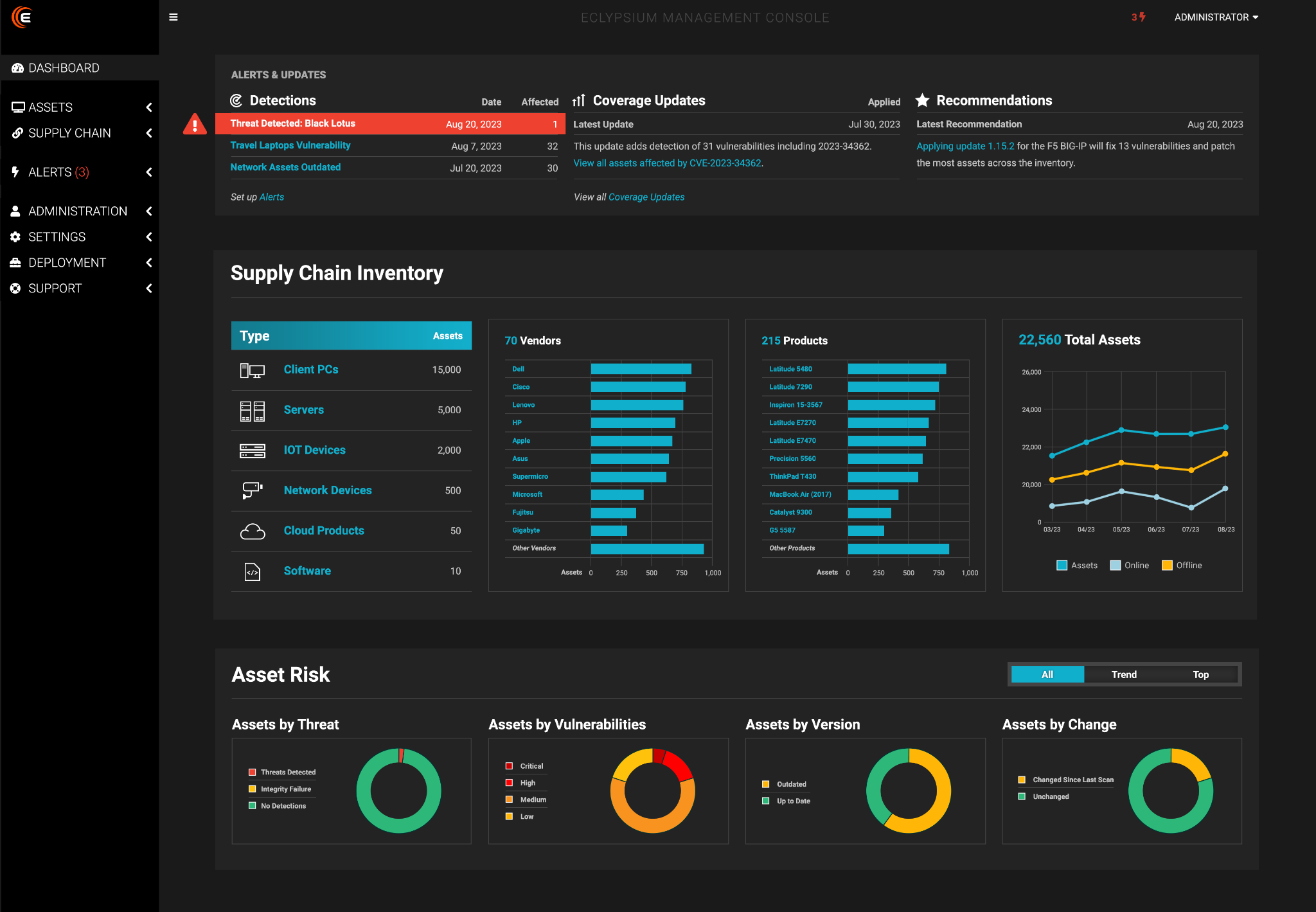
Eclypsium Supply Chain Security Platform –an industry-leading, cloud-based and on-premises platform – provides digital supply chain security for critical software, firmware, and hardware in enterprise infrastructure. Eclypsium helps enterprises and government agencies mitigate risks to their infrastructure from complex technology supply chains.
Providing end-to-end and continuous protection for the underlying components of enterprise infrastructure and devices, Eclypsium’s platform equips organizations with the tools and insights needed to secure their digital supply chains against third-party compromise and vulnerabilities.
Key Capabilities / Features
The Eclypsium Supply Chain Security Platform protects hardware, firmware, and software within enterprise infrastructure and devices. With a simple scan, it verifies their integrity and provides detailed insight to hold suppliers accountable. The Platform enables an organization’s IT security and operations teams to continuously identify and monitor the bill of materials, integrity, and vulnerability of the components and system code in each device, giving insight into the overall infrastructure supply-chain risk to the organization. It audits a company's prospective devices—endpoints, servers, and network appliances—to verify exactly what’s inside and identify potential security issues, authenticating suppliers and sub-suppliers and ensuring authenticity, security, and compliance. Providing end-to-end protection for the underlying components of enterprise infrastructure and devices, Eclypsium’s platform equips businesses with the tools and insights needed to secure supply chains against disruptions, data loss, and other costly risks of cyberattack.
Earlier this year, the company announced supply chain integrity and threat detection capabilities for network infrastructure. The new capabilities detect ongoing compromise of network appliances, including those from Cisco, F5 Networks, Fortinet, and NetScaler, with appliances from more vendors being added. Specifically, the detections look for indicators of compromise on physical and cloud (virtual) versions of network appliances, such as changes to firmware and OS binaries, modified configuration and backup files, reverse shells, and persistence modules. These threat detection capabilities augment Eclypsium’s existing vulnerability and security posture assessment capabilities for these devices.
How we are different
-The Supply Chain Security Platform is the only solution to offer visibility into all the components and dependencies comprising a device’s technology, verifying its integrity, providing insight into which components are vulnerable to attack, and enabling security teams to identify devices requiring an update or patch.
-The Platform goes beyond traditional endpoint security, automatically and objectively monitoring each connected product and device—from computers and servers to networking devices to cloud and virtual machines—for complete visibility and continuous vulnerability assessment. It eradicates the latest and most potent device and supply chain integrity problems, verifying the integrity and supply chain risk of software and firmware inside infrastructure devices, and confirming that it’s authentic and hasn’t been tampered with at any point in the supply chain and operations, down to the components level.
-The Platform features a unique capability—the Software Bill of Materials (SBOM) generated for each component and system code in enterprise devices. It allows companies to discover and monitor their firmware's SBOM, and then proactively identify known threats such as implants, backdoors, and malware. It can establish baselines to detect unauthorized changes and unknown threats. Moreover, it automatically screens every update before it's applied and remotely patches or updates out-of-date or compromised device infrastructure code, giving devices a longer, more reliable lifespan. OEMs and technology vendors can use the solution to build detailed firmware SBOMs, including systems and subsystems of downstream suppliers. Enterprises can utilize the platform to quickly scan firmware to verify that all newly-acquired devices match the vendor’s SBOM and have not been tampered with or include counterfeit components. It also provides capabilities to quickly respond to supply chain vulnerabilities and incidents or establish compensating controls.


