Photo Gallery

|
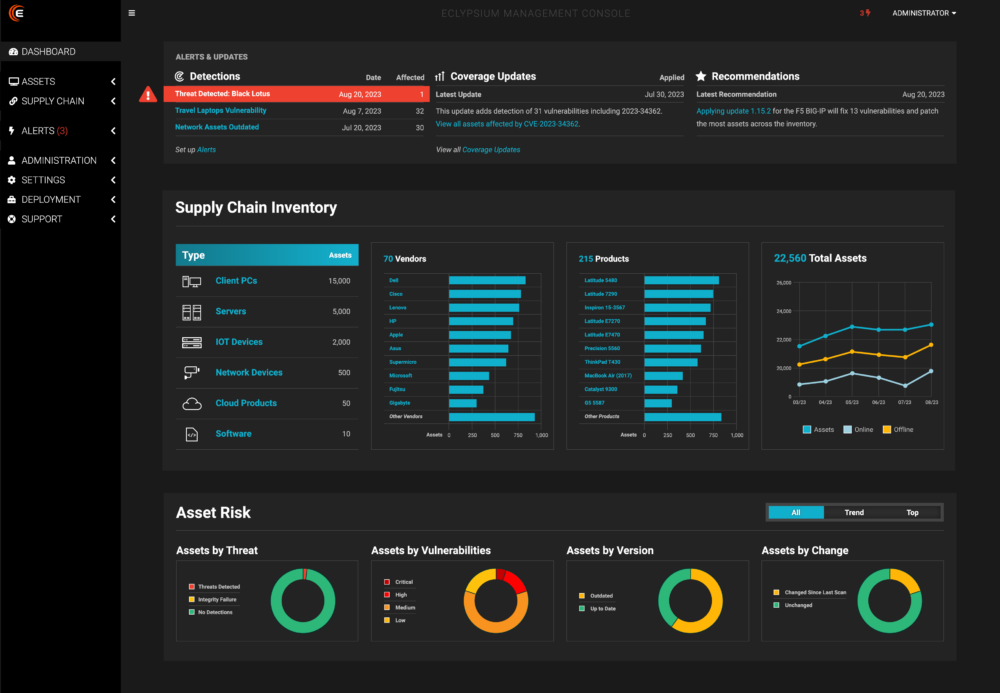
Eclypsium Supply Chain Security Platform
Additional Info
| Company | Eclypsium |
| Company size | 50 - 99 employees |
| World Region | North America |
| Website | https://eclypsium.com/ |
NOMINATION HIGHLIGHTS
Eclypsium Supply Chain Security Platform – an industry-leading, cloud-based and on-premises platform – provides digital supply chain security for critical software, firmware, and hardware in enterprise infrastructure. Eclypsium helps enterprises and government agencies mitigate risks to their infrastructure from complex technology supply chains.
Providing end-to-end, continuous protection for the underlying components of enterprise infrastructure and devices, Eclypsium’s platform equips organizations with the tools and insights needed to secure their digital supply chains against third-party compromise and vulnerabilities. Consider that a typical server includes 30-plus components with updatable microcode or firmware from a variety of manufacturers—one major OEM has 65 direct suppliers and 200-plus second-tier suppliers. This complexity makes it difficult to defend against the threats below the OS and can have devastating consequences.
Eclypsium solves this problem simply with a single solution. The Eclypsium Platform provides the tools and insights needed to secure digital supply chains against disruptions, data loss, and other costly cyberattack repercussions. Eclypsium is unique in that unlike:
–endpoint detection and response companies (EDR), Eclypsium focuses on the firmware and micro-code running underneath the operating system, detecting implants and backdoors that are designed to evade EDR detection
–vulnerability scanners, which simply check advertised firmware versions against known vulnerabilities, the Platform extracts and analyzes the binaries
–firmware analysis services, which help OEM vendors eliminate firmware vulnerabilities in the CI/CD process, Eclypsium focuses on production assets for end-user organizations
–IoT/OT security products, Eclypsium focuses on IT infrastructure devices—client PCs, servers, routers/switches, firewalls, VPN concentrators, load balancers, and virtualization hosts
–software supply chain solutions, Eclypsium focuses on supply chain security for IT infrastructure devices
Key Capabilities / Features
Over the past year, Eclypium introduced several solutions and capabilities that further strengthen the power of the Supply Chain Security Platformn namely:
–Automata, an AI-assisted, automated binary analysis system that replicates the tools and techniques of human security researchers. The system reverse-engineers binaries to uncover zero-day vulnerabilities (which are reported to the respective vendors responsibly) and previously unknown threats
–New GenAI assessment capabilities for the Platform that help to secure the fundamental layers of the generative AI (GenAI) tech stack through support for NVIDIA hardware and popular GenAI foundation models
–More features that offer quick value (e.g., reports for regulatory compliance and automatic firmware updates on more platforms)
–Continued work on its supply chain intelligence offering that lets organizations evaluate an IT product’s risk before purchase. For example, Eclypsium added GenAI models to its catalog so developers can weigh relative risk and assess the characteristics of these models
–Expanded coverage of new types of hardware and firmware, such as NVIDIA systems used in GenAI applications and network devices recently under mass exploitation (Sophos, Ivanti, Cisco, F5, Fortinet, NetScaler, and other network appliances)
–New Threat Detections focusing on highly targeted network infrastructure. Eclypsium now detects numerous vulnerabilities and indicators of compromise in the products listed above, which have been heavily targeted by major threat actors, including Velvet Ant, Pacific Rim, Flax Typhoon, Volt Typhoon, Salt Typhoon. A subset of CVEs related to these threat actors that are detected by Eclypsium can be found here. https://eclypsium.com/blog/salt-typhoon/
–Simplified Configuration and Deployment - Eclypsium has radically simplified configuration and deployment of monitoring and security at the component level across network devices and IT infrastructure
–Surface meaningful risks faster - Eclypsium has redesigned the interface to surface the most urgent risks most quickly, both at the aggregate level, and when investigating individual devices
How we are different
1. While some vendors address the software supply chain security problem, very few address supply chain security for IT infrastructure. Software applications are important, and organizations that are building those applications or use third-party software applications should have supply chain security controls in place. Unfortunately there is little to no visibility into the IT infrastructure running those application workloads and delivering them to users. Eclypsium is the only solution provider to offer visibility into all the hardware and firmware components inside an IT device, verifying their integrity, providing insight into which components are vulnerable to attack, and assisting operational teams with patching and hardening security configurations.
2. Working with manufacturers, Eclypsium maintains the industry’s largest reputation database of firmware binaries. The Eclypsium database includes 12-plus million elements from over 200,000 update packages, covering over 95,000 distinct devices that include a vast range of vendors, device types, and models. Eclypsium is constantly expanding and maintaining this database as vendors roll out new firmware.
3. The complex IT infrastructure supply chain is fundamental to U.S. and private-sector security, and it’s being targeted by criminal groups and nation states. Eclypsium is unique in that it helps organizations establish a “trust but verify” approach to their IT devices instead of having to entirely trust their OEM vendors. Eclypsium is a member of the Cybersecurity and Infrastructure Security Agency's (CISA) Joint Cyber Defense Collaborative (JCDC), an operational collaboration that brings together network defenders from organizations globally to address cybersecurity issues. It recently partnered with Everfox to deliver enhanced security for the U.S. government’s technology supply chain, and Second Front to enhance the Dept. of Defense’s digital supply chain. Eclypsium is the only supply chain security solution for enterprise hardware and firmware listed on CISA’s Continuous Diagnostics and Mitigation Approved Products List.


