Photo Gallery
 |
 |
Edgescan ASM & PTaaS


Additional Info
| Company | edgescan |
| Company size | 50 - 99 employees |
| World Region | Europe |
| Website | http://www.edgescan.com |
NOMINATION HIGHLIGHTS
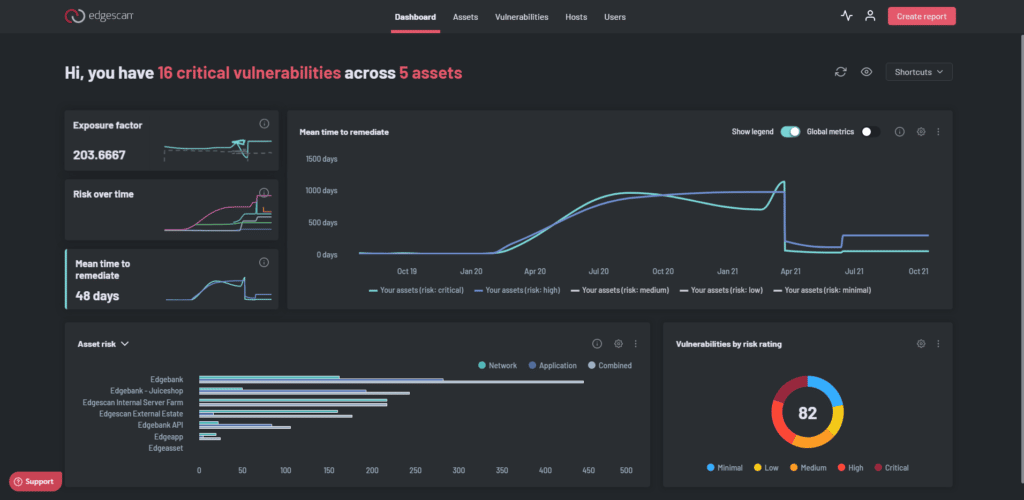
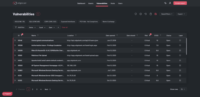
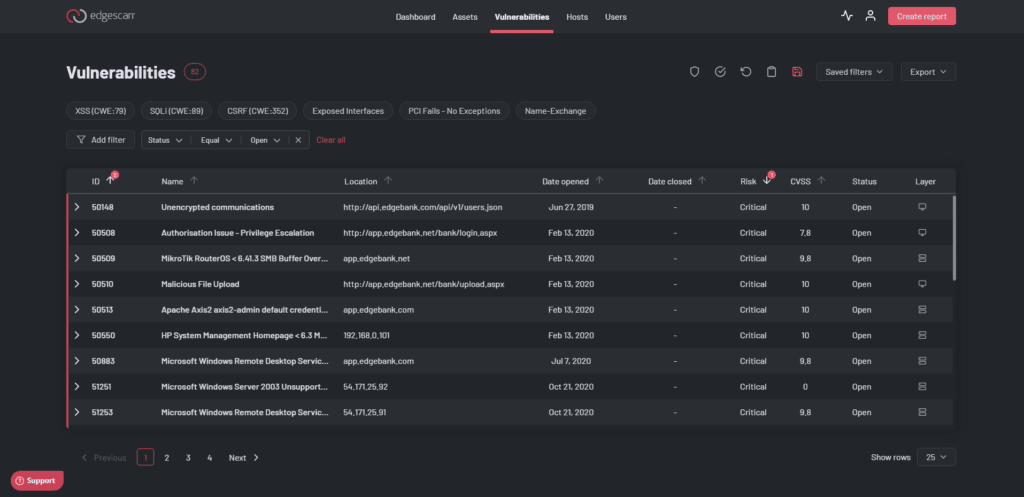
Edgescan provides validated false postitive free fullstack vulnerability management, Attack Surface Management (ASM) and Penetration Testing as a Service (PTaaS) via a cloud based SaaS.
https://www.edgescan.com/platform/features-services/penetration-testing-as-a-service-ptaas/
Delivering continuous assessment and on-demand penetration testing of web applications, API’s and network envrionments.
Edgescan combines Attack Surface Management (ASM) and vulnerability detection to provide continuous triaged vulnerability intel to our clients. Edgescan’s ASM is real-time and natively integrates with cloud providers to keep pace with change as it happens. This results in automatic assessment of systems as they are deployed in the cloud.
https://www.edgescan.com/platform/features-services/attack-surface-management/
Validation of all vulnerabilities is a combination of data analytics and expert know-how resulting in super accurate vulnerability Intel.
Penetration Testing as a Service is on-demand and a hybrid of clever automation and OSCP/CREST certified penetration testers. We use human experts to detect vulnerabilities automation cant detect such as business logic or contextual vulnerabilities.
Edgescan maps discovered vulnerabilities to threat intel such as the “CISA Kev” to prioritize vulnerabilities as they’re discovered.
https://www.edgescan.com/platform/features-services/threat-intelligence-risk-based-prioritization/
Edgescan can integrate with virtually any other solution.
https://www.edgescan.com/technology-integrations/
How we are different
ASM, Vulnerability Management and PTaaS combined: Get visibility and vulnerability intel in real-time across web applications, cloud, hosts, endpoints.
Full stack coverage - A unified view of risk across the full stack.
Validated results - No false Positives. A combination of analytics based on a "data lake" of thousands of vulnerabilities and human expertise results in accurate reliable vulnerability Intel.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



