Photo Gallery
 |
|
|
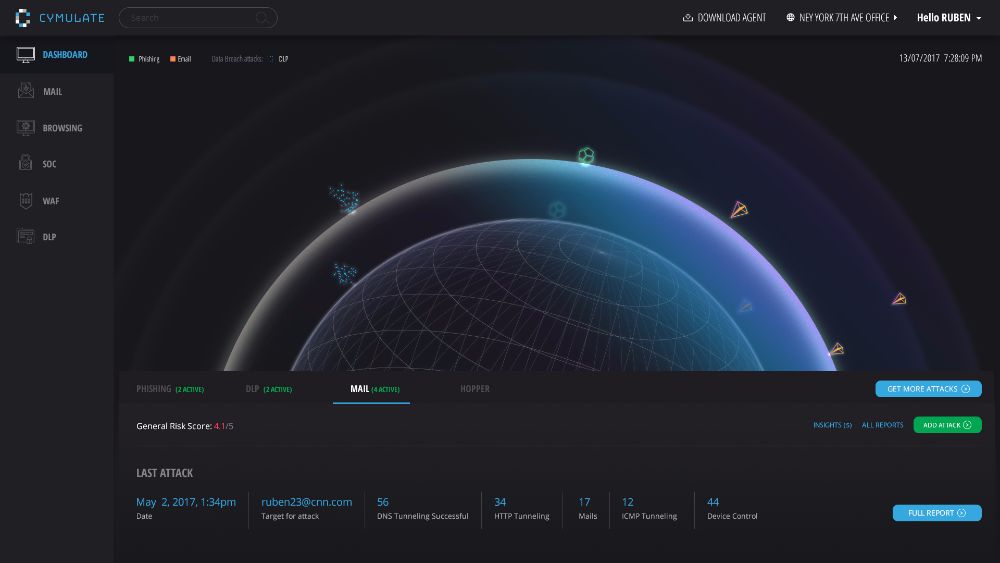
Cymulate - Email Assessment


Additional Info
| Company | Cymulate - Breach & Attack Simulation |
| Company size | 10 - 49 employees |
| Website | http://www.cymulate.com |
NOMINATION HIGHLIGHTS
Cymulate’s advanced technology allows organizations to launch simulations of cyber-attacks against themselves, immediately providing vulnerabilities and mitigation procedures to close each gap. The centralized platform allows security testing through multiple attack vectors.
The number of targeted attacks through an organization’s email system has dramatically increased in recent years. Major companies, government agencies, and political organizations have reported being the target of attacks. The more sensitive the information and/or operations an organization handles, the higher the possibility of becoming a target. Some of the pain is self-inflicted: poor configuration or implementation. But despite greater use of mail filters and content disarming solutions, an alarming percentage of attacks still succeed to penetrate through this vector. The last two wide-reaching cyber-attack campaigns (WannaCry & NotPetya) originated from malicious email.
Following its launch in June of 2016, Cymulate was able to address this problem specifically by broadening its “breach and attack” platform. It introduced the first and only product with the capabilities to test email security on-demand, receive detailed and actionable reports immediately and allow continuous improvement.
Cymulate’s unique email solution enables organization to challenge this main attack vector, by the remote, on-demand testing of the entire email infrastructure. By continuously verifying or disproving assumptions, you are improving an organization’s email posture with each simulated attack. In addition, if there is spreading virus campaign or other attack, Cymulate immediately gets and shares samples of it allowing users to test its effect on a network immediately and mitigate attacks before they happen. All in the form of a plug-and-play, SaaS-based solution—no hardware required.
How we are different
o This is the only product able to provide an organization with a current security posture specific for the email vector
o It is a fully automated and diversified assessment; quickly generating reports on vulnerabilities and the mitigation process according to the level of the risk.
o The solution is “plug & play:” easy to use and takes only 5 minutes to implement and run your assessment

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



