Photo Gallery
 |
 |
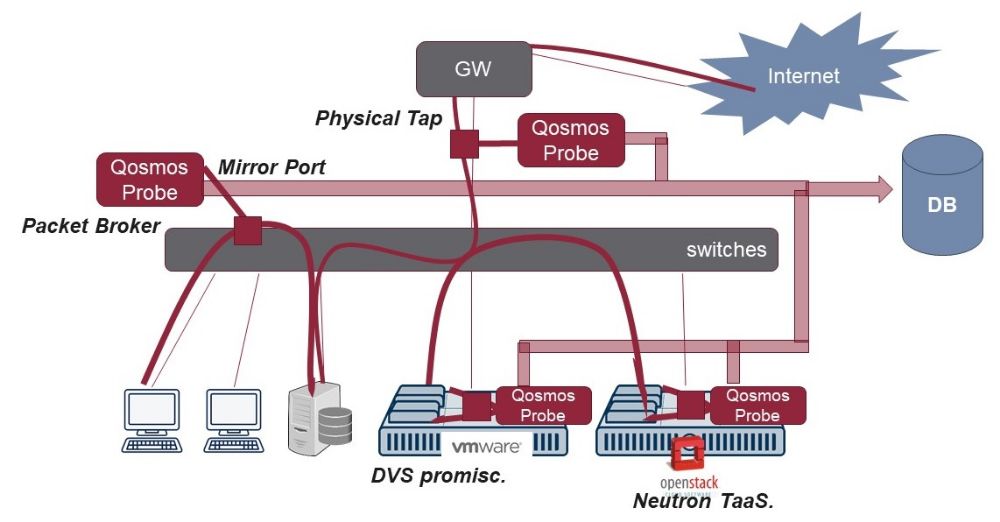
Enea Qosmos Probe as DPI Sensor

Additional Info
| Company | Enea Qosmos Division |
| Company size | 500 - 999 employees |
| Website | http://www.qosmos.com |
NOMINATION HIGHLIGHTS
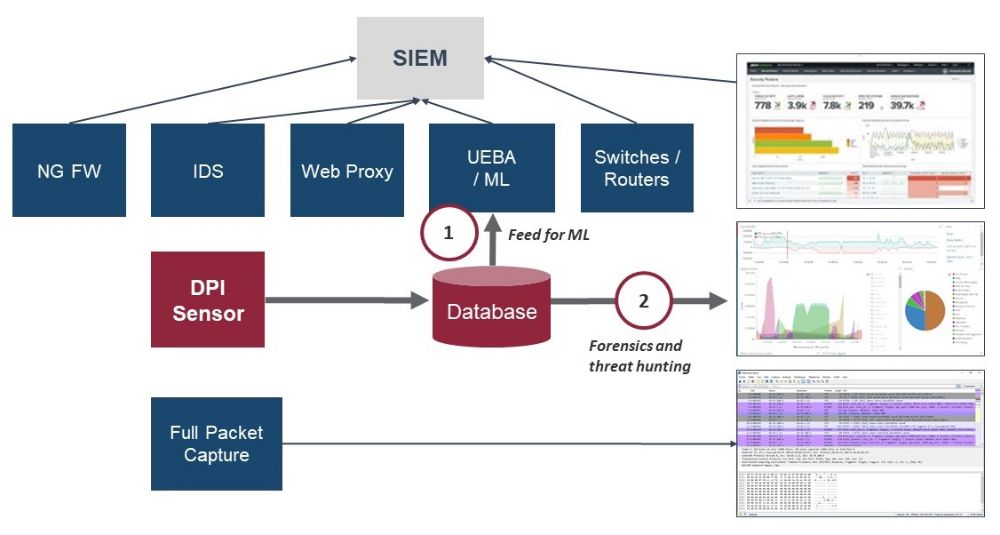
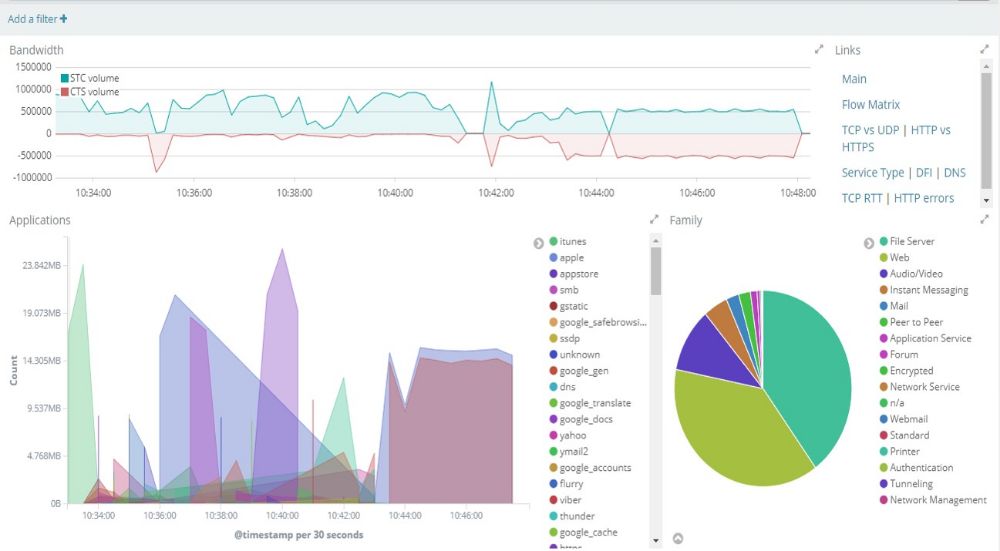
Enea’s Qosmos Probe is a Deep Packet Inspection (DPI) sensor that represents a new form factor, leveraging the granular visibility of DPI to complement existing security tech stacks and significantly strengthen threat hunting capabilities. DPI is a proven technology, widely used in cybersecurity to detect and mitigate threats. It is embedded in NG firewalls, UTM, secure gateways, and different types of threat analysis tools to ensure rapid and reliable detection of malware attempts and security breaches.
Used as a complement to traditional network security solutions, the Qosmos Probe is an expert tool for network forensics and threat hunting. It streamlines investigations and improves time-to-detection by capturing and analyzing 100% of traffic in real-time, including traffic shape (volumes, origin & destination, device type/VM, etc…) and content (attachments, encapsulated traffic, etc…). Through regular signature updates, the Qosmos Probe can recognize an extensive range of protocols, including new and outdated protocols, and identify devices/servers/VMs that they cross. When an anomaly is detected, such as irregular use of a protocol or use of an outdated protocol, an alert is generated. Hunters can then isolate the threat and protect network resources before the virus becomes active.
In addition, the metadata extracted from traffic flows by the Qosmos Probe provides a rich information feed that can be used to boost machine learning for User and Entity Behavior Analytics (UEBA) and Next Gen SIEM, strengthening threat analytics. This translates into more accurate alerts, shorter time-to-detection, and fewer false positives.
The Qosmos Probe stores traffic information it captures in a database, providing rapid and easy query and visualization. The sensor provides high information resolution using a fraction of the storage required for full packet capture because it only requires traffic metadata (sender, receiver, device type, file type, etc.), discarding irrelevant content, such as encrypted data or video content.
How we are different
- More detailed traffic visibility than alternatives:
Full visibility into network traffic up to Layer 7; 3100+ protocols and applications classified; classification of traffic encapsulated into all types of tunnels (VLAN, GRE, VPN, TOR...); ability to create custom application and protocol signatures and ability to visualize detailed traffic between VMs or containers
- Extraction of metadata:
5000 application metadata extracted (more than any in the industry); protocol details: File extensions, content…; unique real-time Deep File Inspection capabilities; precise end point identification (device, IP, user, domain name, etc.)
- Ease of integration:
Scales to n x 10 Gbps of traffic per probe on commodity hardware; cloud-native architecture optimized for virtualized environments (OpenStack, VMware) and cloud-based applications; centralized management using standardized interface (REST, netconf, ...)

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



