Enzoic: Better Strong Authentication with Minimal User Friction
Photo Gallery
 |

 |
Enzoic: Better Strong Authentication with Minimal User Friction


Additional Info
| Website | http://www.enzoic.com |
| Company size (employees) | 10 to 49 |
| Headquarters Region | North America |
Overview
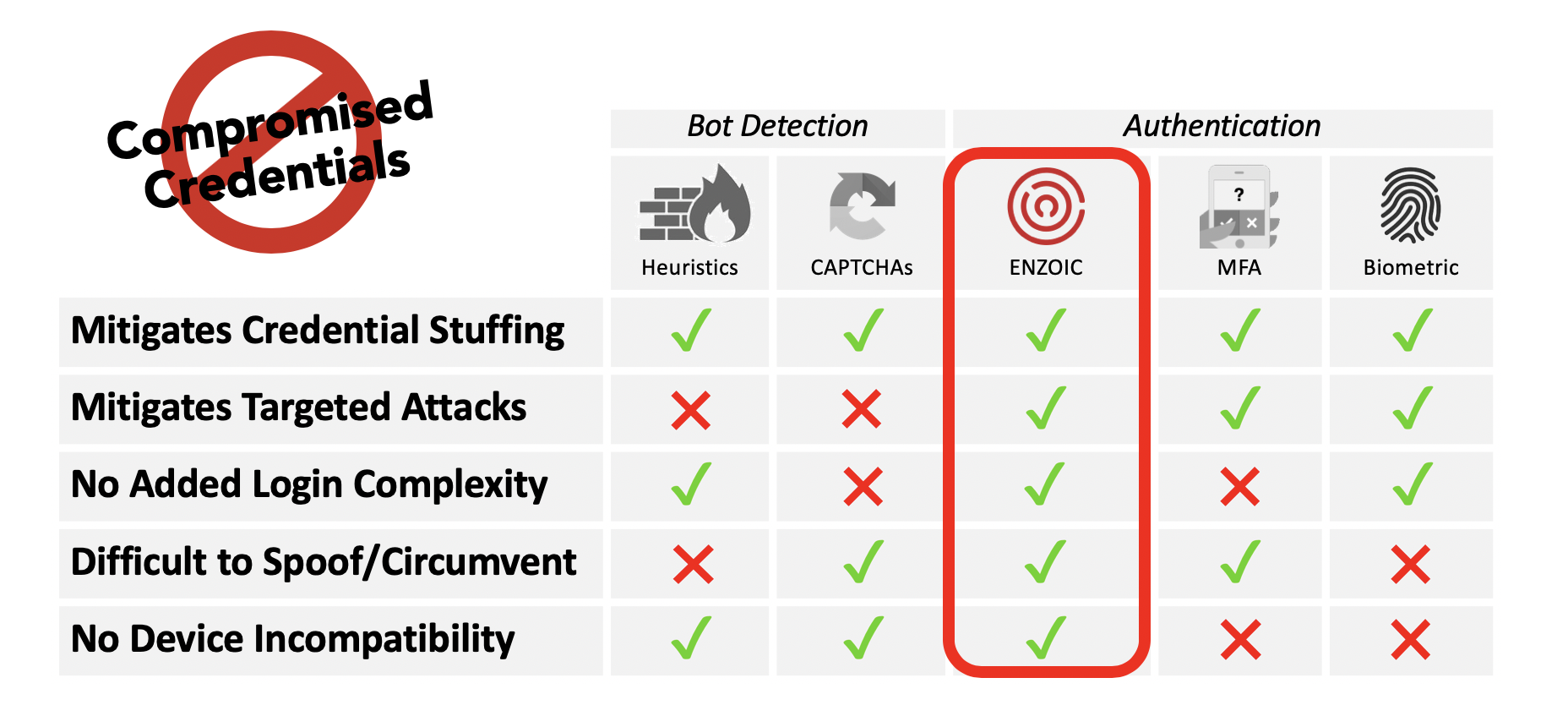
Passwords are the most common layer of security; however, billions of compromised users’ credentials are circulated on the public Internet and Dark Web. And due to the common practice of password reuse, attackers can take credentials exposure in the numerous data breaches and use them to login to other sites that haven’t been compromised.
Enzoic’s security solutions help organizations detect when a login is using credentials that are known to be exposed to prevent unauthorized access. It’s that simple.
The key to our business is the automated and the manual research we do to collect all the compromised credentials available from the public internet and dark web sources. We have billions and update them every day so our customers are able to 1) stop account takeover attacks with online accounts and 2) prevent employees from using compromised passwords through our Active Directory plugin.
Enzoic for Active Directory is a plugin that screens user accounts continuously against a billion-record dark web database to see if that user’s password has been exposed. If user’s password is exposed, the Active Directory administrator can adjust password policies based on the needs of the organization. Enzoic for Active Directory can be installed in as little as an hour, depending on the number of domain controllers and it is a low cost solution to protect sensitive organization accounts. It is also the only solution on the market to fully comply with the NIST 800-63b password guidelines.
For online accounts, other authentication hardening solutions (e.g. multi-factor authentication) add steps to the login process and require devices that frustrate consumers, which affects adoption. And in environments where security isn’t negotiable, Enzoic is a complementary solution to ensure the password layer remains secure.
How we are different
In just over 36 months, we have:
1) addressed a clearly defined security threat with a novel solution
2) demonstrated market acceptance through direct sales and major industry partnerships
3) achieving substantial business growth without taking VC funding



