ERAM- Enterprise Resource Authorization Manager
Nominated in the Category:
Photo Gallery
 |
 |
ERAM- Enterprise Resource Authorization Manager

Additional Info
| Company | Tools4ever |
| Company size | 150 employees |
| Website | http://www.tools4ever.com |
NOMINATION HIGHLIGHTS
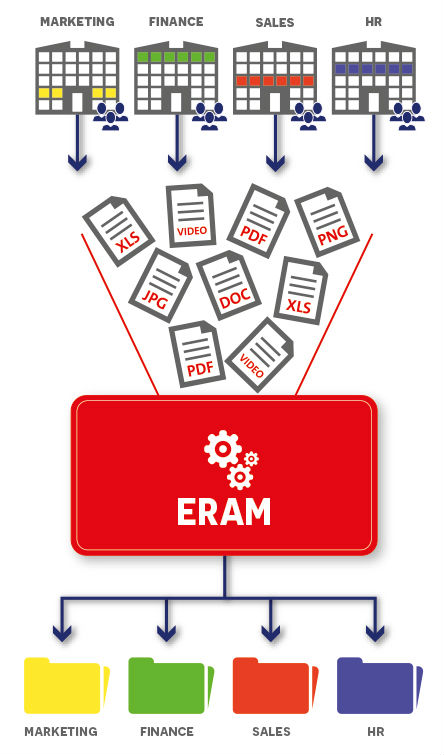
ERAM enables organizations to streamline and optimize access control for unstructured data. It shows who has access, who should have access, who owns the data, who has tried to access certain data and where sensitive information has been stored. This will allow you to define what the access should look like, so that ERAM can ensure it is set up correctly.
Collection – The Collection module uses ERAM agents to collect all access rights from the various sources and saves these in a centralized database. It collects all data in one go, but is also capable of continuously monitoring which changes occur and register these.
Reporting – This module offers reports including:
• The access to a file/directory through more than one group membership
• User accounts that no longer exist in Active Directory
• Duplicate access privileges for the file/folder of a user or group
• Recommendations with regards to the set of rights that can be reduced based on the actual activities performed by an employee.
Interactive – This module makes it possible to browse all access privileges through a single tree view. It provides direct insight into the resources to which employees have access (People to Files), who has access to a particular resource (Files to People) and which actions have been performed on the resources by whom.
Monitoring – ERAM is able to keep track of each action performed on unstructured data and intervene where necessary. Through proactive monitoring, triggers can be set for data and persons that require an action when a particular event takes place. Reactive monitoring offers the possibility to answer questions based on previous actions.
How we are different
• Better insights – ERAM offers enhanced insight into the actual access privileges for the file system. The ability to provide insight into access privilege pollution in the file system, to clean it up and to prevent future pollution.
• Compliant - The ability to be compliant and meet the audit requirements ensures the organization reduces risks. This safeguards the business operations and prevents sensitive business information ending up in the wrong hands.
• End user - End users know what they can expect. They do not have superfluous access privileges, and any required additional privileges can be requested quickly and easily.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



