Photo Gallery
 |
Ericom Application Isolator

Additional Info
| Company | Ericom Software |
| Company size | 100 - 499 employees |
| Website | http://www.ericom.com |
NOMINATION HIGHLIGHTS
Ericom extended its innovative Zero Trust security portfolio earlier in 2020 when it introduced Ericom Application Isolator, a simple, cost-effective way to add powerful identity-based micro-segmentation/ZTNA (Zero Trust Network Access) security controls to existing VPNs and networks. It bolsters a company’s defenses by limiting remote (North-South) application and resource access to only what is truly required for users to be productive. This eliminates the issue of over-privileged access, which is a significant vulnerability most organizations face. Its granular micro-segmentation controls also completely cloak applications from unauthorized users, isolating them from both external and internal attacks. By eliminating lateral movement within the network, it stops the spread of pervasive threats like ransomware.
In response to COVID-19 office closures in 2020, most organizations doubled down on the use of VPNs to quickly enable home-based work environments for their new remote workers. Unfortunately, this increase in remote workers, and their reliance on vulnerable VPNs, increased their organization’s exposure to the surge in cybercrime that the market has experienced. As a result, organizations depending on VPNs to stay connected and productive needed a way to “retrofit” their VPNs with additional security controls.
Ericom took a unique approach with Ericom Application Isolator, designing it to be a lightweight, simple to deploy and use, complement to VPNs, as opposed to a replacement to VPNs. This approach makes the security solution much more cost-effective for organizations. More importantly, Ericom offered the Standard Edition of the solution free for IT teams to download, deploy, and use. The software’s Standard Edition is free and can be downloaded from Ericom’s website, here: https://www.ericom.com/ericom-application-isolator/
By giving their VPNs a “Zero Trust Security Boost” with Ericom Application Isolator’s identity-based micro-segmentation capabilities, organizations can confidently rely on their remote access infrastructure to keep their users connected, productive, and secure
How we are different
Based on Zero Trust principles of “trust nothing, verify everything” and least-privilege access, Ericom Application Isolators delivers Zero Trust Network Access (ZTNA) controls and microsegmented access to existing VPNs and corporate networks. A free Standard Edition is available from Ericom’s website.
Key differentiations include:
· Application/Resource Cloaking - makes corporate applications and resources invisible to users who don’t have proper permissions by “cloaking” their DNS and IP port information. Users connect to the network as usual, either while at the office or remotely using their VPN client, and Ericom Application Isolator enforces least-privilege access policies. Authenticated users with valid permissions have no change in their user experience. Additionally, IT professionals have visibility into application and resource access and use.
· Integrations with Leading VPNs and NGFWs - leverages an organization's existing investments in VPNs and NGFWs to accelerate their move to microsegmentation-based Zero Trust Security. The unique approach of leveraging VPNs and firewalls allows the solution to be deployed very quickly. It does not require new agents to be installed and operates by leveraging the logs and clients of exiting VPN gateways of leading vendors, including Check Point, Forcepoint, Cisco, Fortinet, OpenVPN, and more.
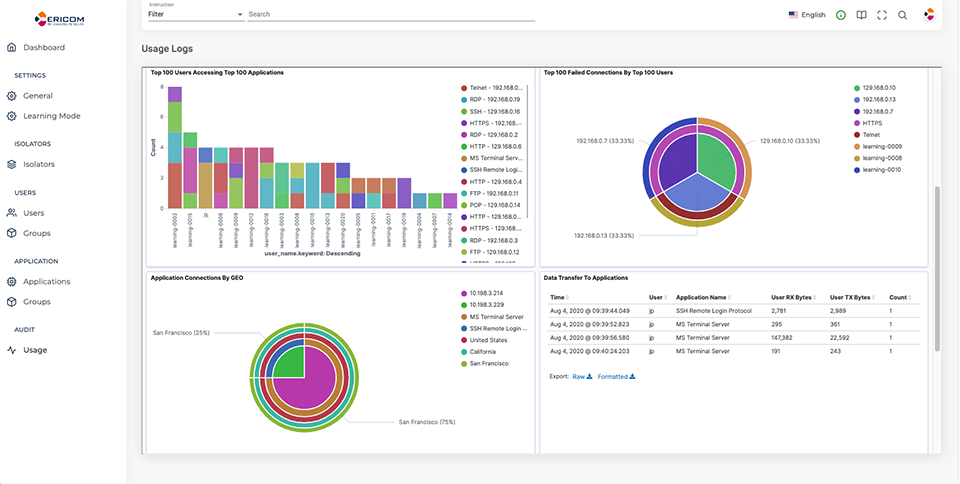
· Detailed Network Traffic Analysis - simplifies the process of monitoring and auditing remote access to all network connected resources. Log data is automatically turned into a set of rich charts and graphs that can be customized to deliver the level of detail that T decision-makers, SOC analysts, or external auditors need to understand remote access activity. If needed, the solution’s data can be exported to a customer’s SIEM solution for additional analysis and reporting.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



