Photo Gallery

|
|
Exabeam User Behavior Intelligence Platform

Additional Info
| Company | Exabeam |
| Company size | 75 employees |
| Website | http://www.exabeam.com |
NOMINATION HIGHLIGHTS
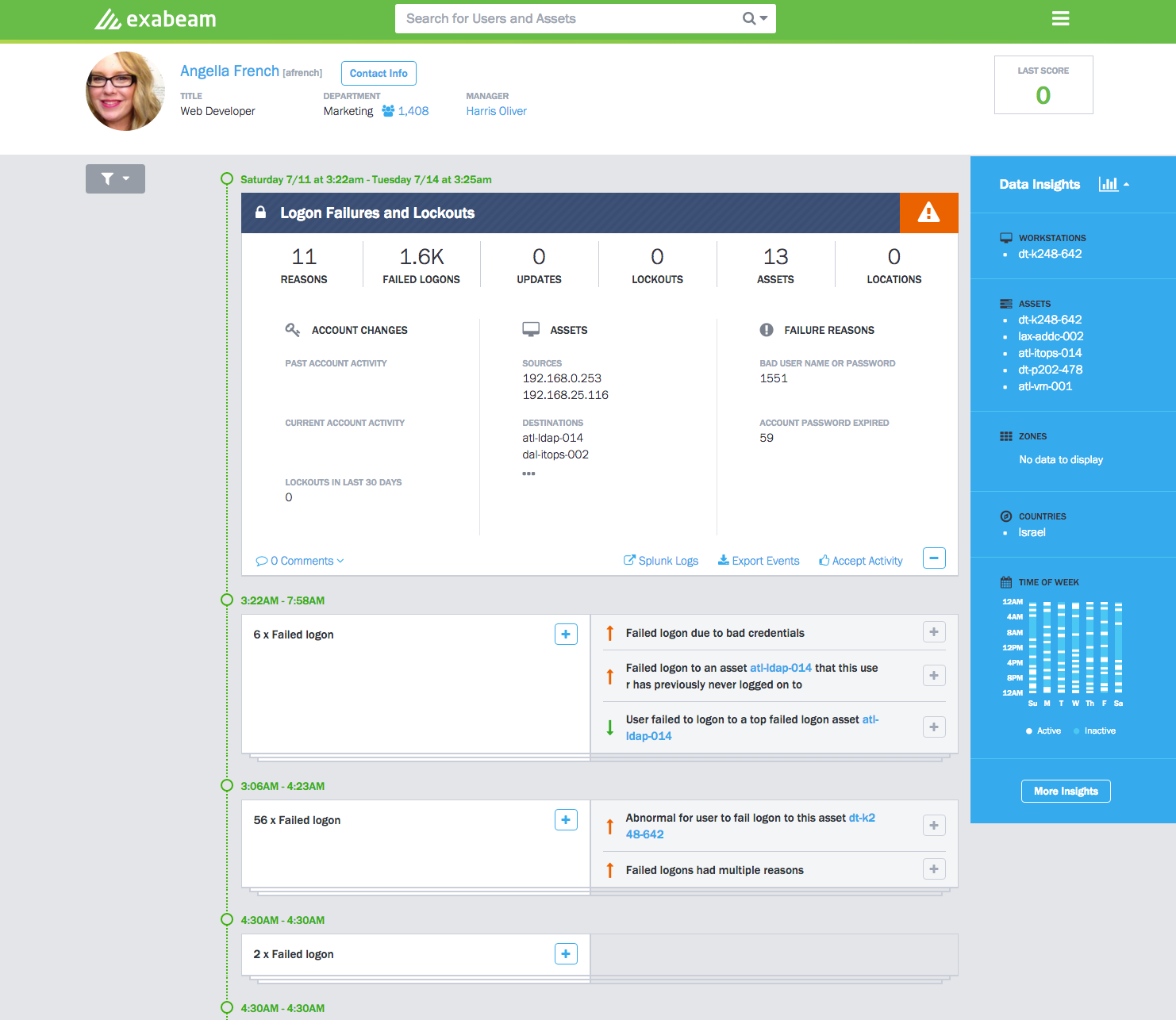
Like humans, machines with credentials can be a source of threats but they also generate a lot of traffic, making it difficult to analyze their behavior. Machines can fall prey to threats such as DNS tunneling, attaching to Tor networks, or rogue authentication requests to directory services. Using these methods, a hacker could compromise a machine to allow them to bypass proxy servers, firewalls, and security scanning systems, or get more info on servers on the network such as names, users, and passwords. None of these machine or “entity” threats has a user attached to it. To find them, you need to analyze the network traffic.
In its latest version of the Exabeam User Behavior Intelligence Platform (3.0) the company introduced a new elastic architecture for analyzing human and non-human behavioral risk. The number of internet-connected devices and cloud services in today’s large enterprises is increasing rapidly, adding more and more non-human devices and accounts to the network environment. This includes applications, workstations, and servers, any of which may have admin-level credentials that allow access to other systems or cloud services, creating the potential for a large data security risk if taken over by a hacker.
With Exabeam 3.0, enterprises can now perform the same level of behavioral analysis on the entities within their networks as they do with human behavior, including the ability to detect when the accounts (service accounts, system accounts, etc.) of those devices are being hijacked and used for malicious purposes.
How we are different
• Exabeam 3.0 is designed to ingest, store, and analyze exponentially larger volumes of behavioral data generated by humans and machines. The platform has been updated with a new scale-out or "elastic" architecture that allows additional Exabeam nodes to be added to a cluster, growing it to any size needed. The new architecture gracefully handles the massive amounts of data obtained from machines and processes, as well as their associated credentials. With this update, Exabeam is the only UEBA vendor to provide stateful tracking of behavior from any type of machine or person at scale.
• Exabeam 3.0 has already proven itself in the field. At a customer site, Exabeam 3.0 was the only security solution that detected DNS tunneling, attaching to Tor networks, and rogue authentication requests to directory services even though the customer already had machine and network oriented security products installed. Exabeam behavioral analytics, combined with an architecture that can capture massive amounts of machine and network data, enabled detection of multiple threats that were invisible to all other products.
• Exabeam 3.0 also allows companies to more easily leverage user behavior analytics in a cloud environment. Enterprises can deploy Exabeam into any cloud environment and scale-out as needed to support the growing amount of data and data sources businesses wish to analyze. Exabeam software can be deployed in clouds such as Amazon Web Services (AWS), Google Cloud Platform, and Microsoft Azure, in managed security services providers (MSSPs), and in on-premise data centers.


