Photo Gallery
|
|
ExtraHop Reveal(x)

Additional Info
| Company | ExtraHop |
| Company size | 100 - 499 employees |
| Website | http://www.extrahop.com |
NOMINATION HIGHLIGHTS
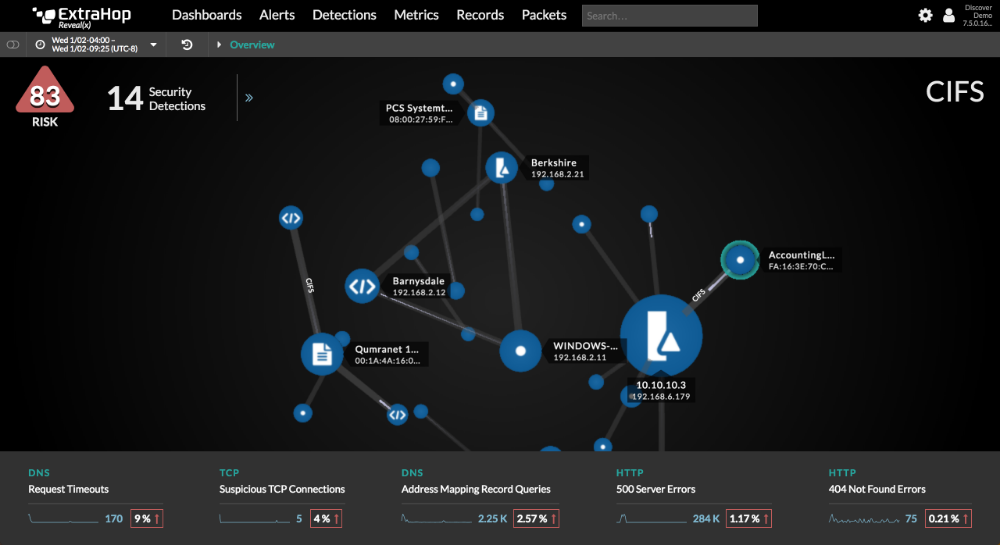
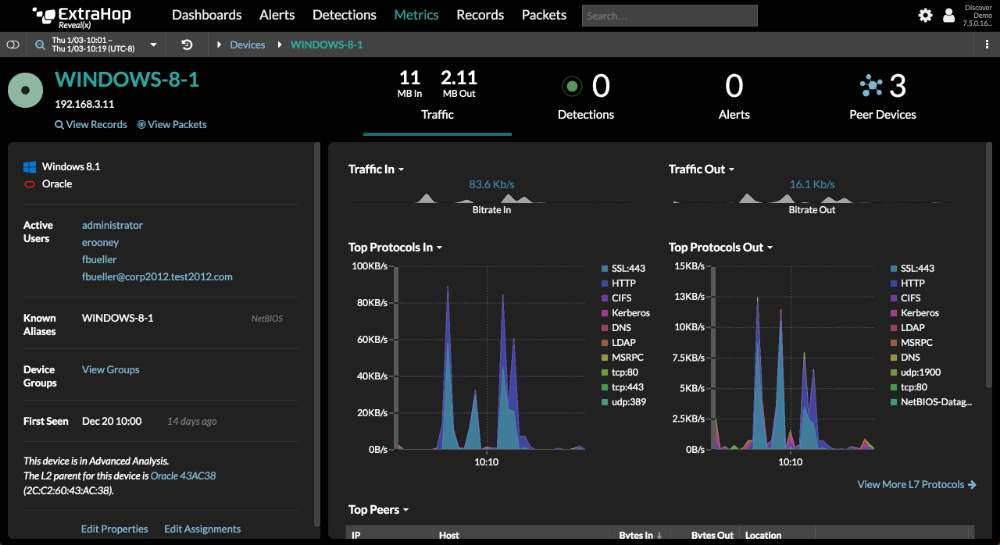
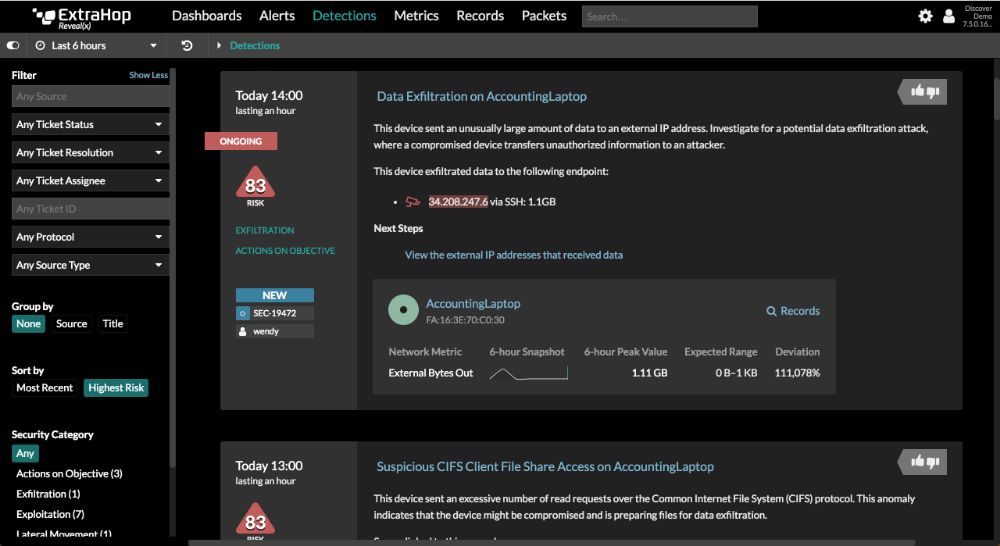
ExtraHop Reveal(x) enables organizations rapidly detect, investigate, and remediate risks and threats. The network traffic analysis product applies machine learning to communications between devices to detect malicious behavior that would otherwise go unnoticed. Analysts cannot only detect and validate alerts in Reveal(x), but also rapidly pursue investigations to the forensic details needed to remediate the issue. Reveal(x) automatically identifies and prioritizes analysis for critical assets in dynamic environments, enabling analysts to efficiently spend their time investigating alerts that matter. The core technology behind Reveal(x) is a real-time stream processor that reassembles packets into full transactions and extracts 4,600+ points of metadata, which are used as machine learning features. The product offers sophisticated visualizations of network communications through live activity maps and dashboards, as well as the ability to search and query transaction records. Analysts can also download the actual packets for a particular stream if they need forensic evidence.
How we are different
1. Improved signal-to-noise - ExtraHop Reveal(x) offers sophisticated behavioral detection of threats in real time using unsupervised machine learning. What differentiates our machine learning from competitors' is the richness of our dataset, which includes Layer 7 (application-layer) details from 40+ enterprise protocols. With a richer dataset, our training models can more accurately detect actual malicious behavior and radically reduce the number of false alerts that the SOC needs to deal with.
2. More than just threat detection - Besides detecting real-time threats, Reveal(x) records a wealth of information about the environment so that organizations can improve their security hygiene. They can reduce and harden their attack surface with an up-to-date catalog of assets and understanding of whether their controls are working. Security teams can easily identify risks--such as weak ciphers, insecure protocols, and sensitive data sent over plain text--that would otherwise require a time-intensive manual audit of servers to find.
3. Decryption at scale - Unlike other network traffic analysis products that cannot inspect the payload of encrypted traffic, Reveal(x) can decrypt traffic at speeds up to 100 Gbps. Hackers increasingly hide their activities in encrypted traffic and using other techniques that rely on telemetry data results in less accuracy and confidence in the detections. Reveal(x) also has a novel method of decrypting traffic protected by perfect forward secrecy (PFS) ciphers, which is required in the new TLS 1.3 standard.


