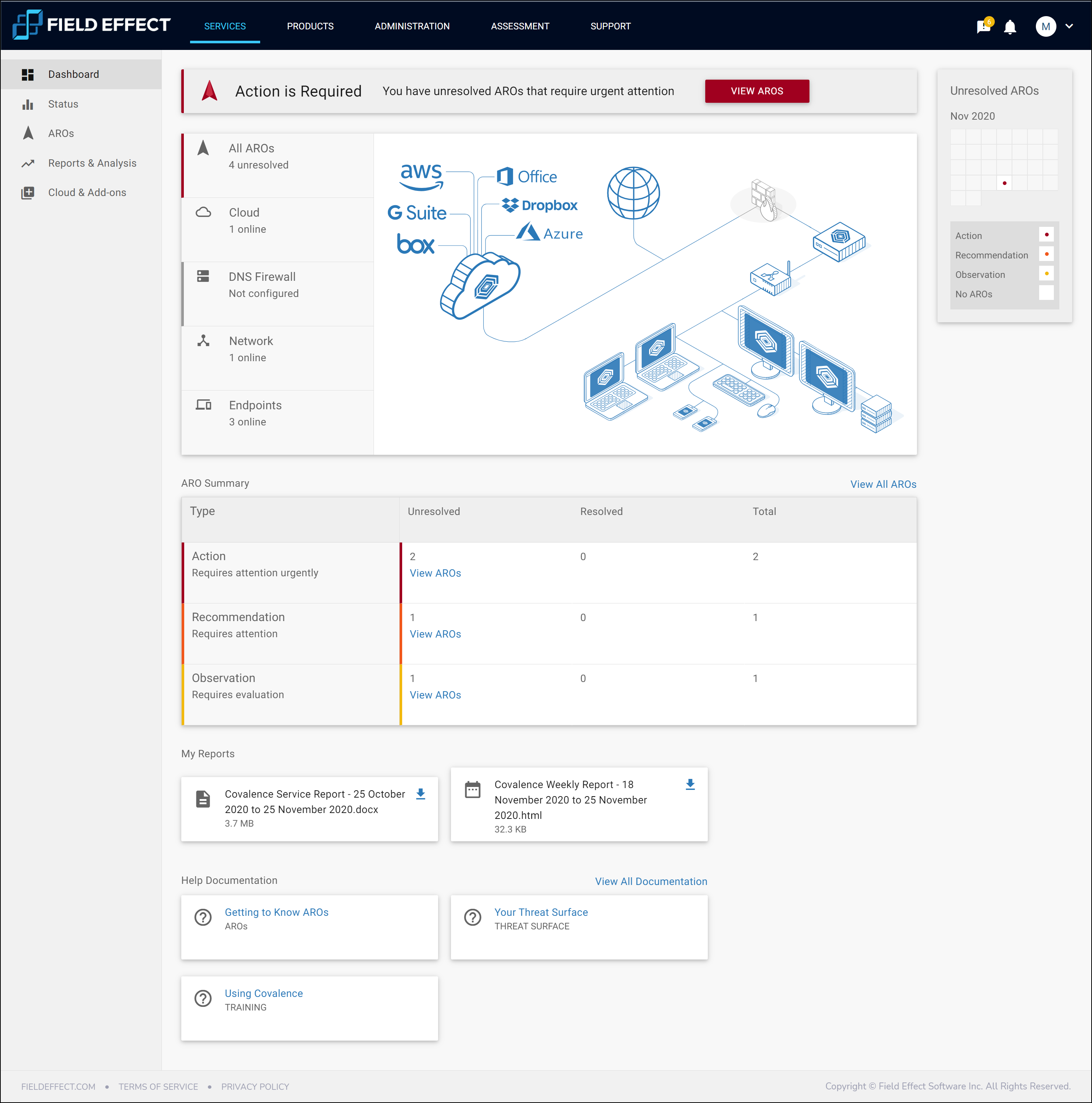
Field Effect’s Covalence threat monitoring, detection, and response platform
Recognized in the Category:
Photo Gallery
 |

 |
Field Effect's Covalence threat monitoring, detection, and response platform

Additional Info
| Company | Field Effect Software, Inc. |
| Company size | 100 - 499 employees |
| Website | https://fieldeffect.com/ |
NOMINATION HIGHLIGHTS
Field Effect helps small and mid-size businesses (SMBs) solve the challenge of how to keep their operations and data safe from cyber threats. Our Covalence threat monitoring, detection, and response solution is the result of years of research and development by the brightest talents in the cyber security industry.
Purpose-built for SMBs, Covalence is incredibly easy to set up and use. Its sophisticated analytics and proprietary, intelligence-grade monitoring technologies provide a holistic view across IT environments to identify vulnerabilities, risks, and cyber threats.
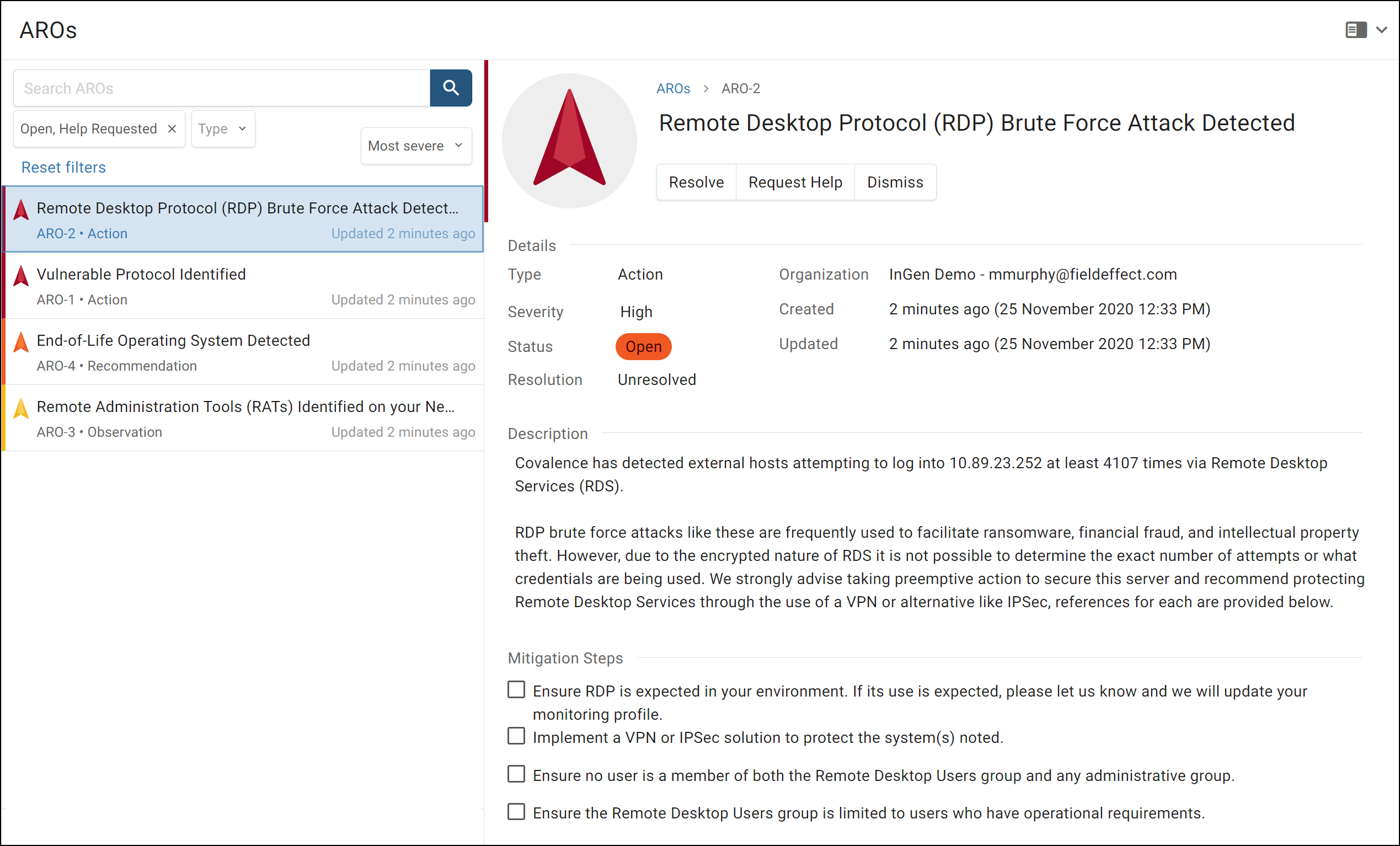
First to deliver an end-to-end ‘cross domain’ monitoring solution, Covalence enables businesses to monitor their entire IT environment — networks, endpoints, and cloud infrastructure —and access the threat data and reporting from one platform. Through its AROs alerting, businesses receive actionable insights to understand the response needed to secure their operations.
Here are a few Covalence features:
–24/7 Network Monitoring: Identify threats and potential vulnerabilities to your network traffic through sophisticated monitoring, alerting, analysis, and insights.
–24/7 Cloud Monitoring: Use our cloud-native monitoring sensor to protect your company domain and cloud-based services.
–24/7 Endpoint Monitoring: Protect your endpoints with practical insights into the configuration, operation, behaviour, vulnerabilities, and threats facing your Windows, Linux, and Mac platforms.
–AROs Reporting: Receive threat data as informative, actionable reporting with Actions, Recommendations, and Observations (AROs) to guide remediation and improve security.
–Malicious Activity Protection: Protect your endpoints with real-time, automated blocking and notification of attacker activity — such as attempts to run malicious executables on endpoints to launch ransomware or other malware — as well as proactive protection alerts for software updates, patching, and more.
–DNS Firewall: Use our DNS firewall to ensure safe web browsing and Internet access by blocking connections to malicious websites.
–Cyber Concierge: Access our dedicated team of experienced cyber analysts for technical support, advice on security strategy, and more.
For more information, visit https://fieldeffect.com/
How we are different
Covalence was built to support two simple beliefs. First, that every company, from the very large to the very small, should have access to excellent cyber security. Second, you shouldn’t need deep expertise in cyber security to understand what you are buying, how it is protecting you, and how to use it.
Covalence provides sophisticated intelligence-grade threat monitoring, combining powerful cyber protection with simplicity. As a turnkey managed security service, it provides comprehensive monitoring, detection, and response across endpoints, networks, and cloud services — with the data and analysis accessible through a single, user-friendly portal. It makes it easy to understand, prioritize, and act on cyber threats to business operations. The result is an end-to-end, full feature threat monitoring, detection, and response solution. Here are a few benefits and features:
-No security expertise required.
-No more alerting fatigue.
-Easy to deploy and manage.
-Flexible pricing.
-24 x 7 cloud, endpoint, and network monitoring.
-AROs alerting and reporting.
-Malicious activity protection.
-Analyst-led active response support.
-Incident Response service packages.
-Flexible reporting.
In contrast to other monitoring solutions, Covalence not only sees into every aspect of a company’s threat surface — networks, endpoints, and cloud services — it aggregates the data from multiple security events into simple, actionable steps. Covalence delivers cyber analyst-verified threat data as clear and prioritized reporting that helps businesses understand their threats as Actions, Recommendations, and Observations (AROs). This proprietary approach removes noise to show the threat alerts that matter with the context needed to resolve them. Each AROs alert includes a straightforward description of the issue and detailed steps for resolution. This eliminates hours investigating a volume of threat alerts that may not take priority, the risk of missing critical threats in that noise, and the need to manage and gather data across multiple sources.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



