Photo Gallery
 |
 |
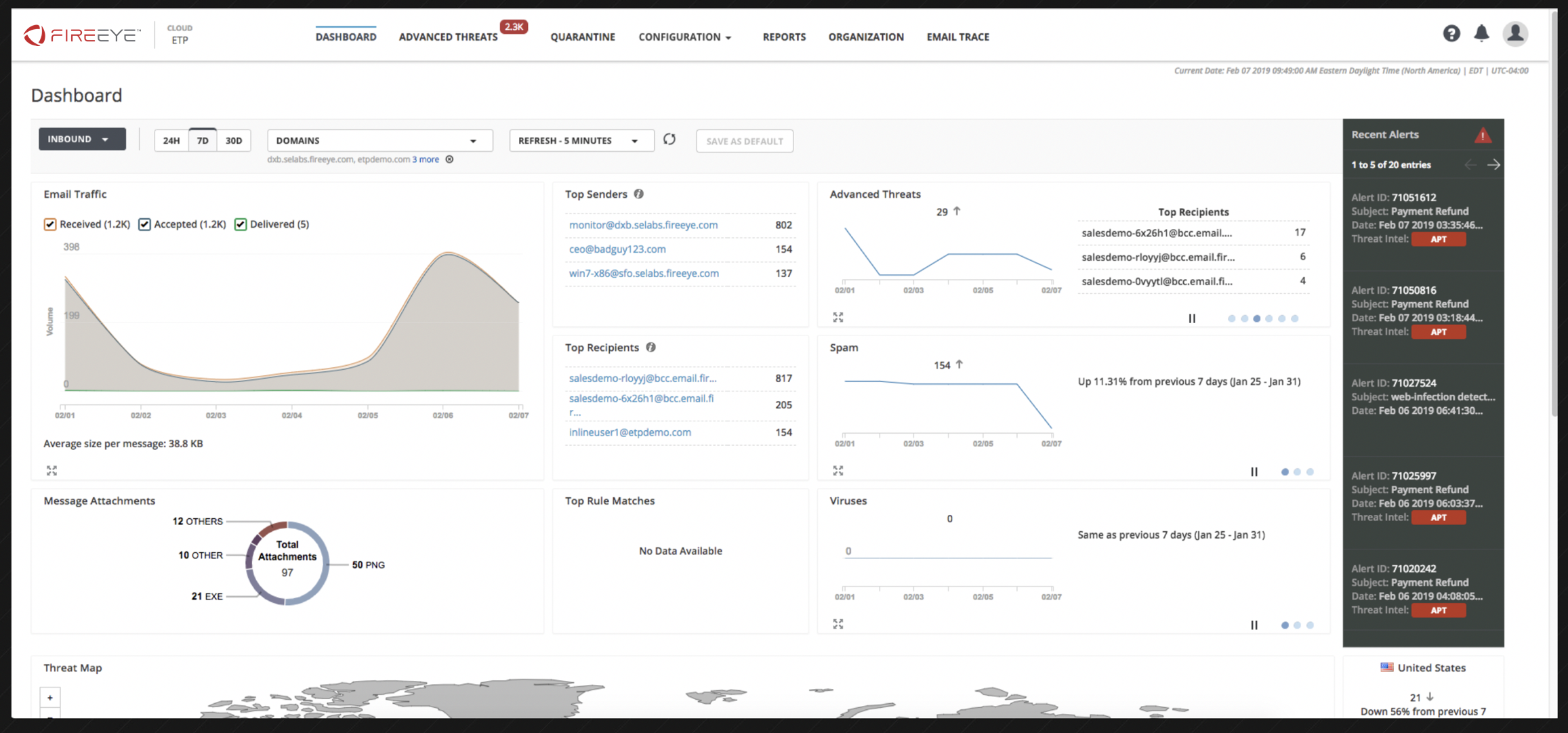
FireEye Email Security


Additional Info
| Company | FireEye |
| Company size | 1,000 - 4,999 employees |
| Website | http://www.fireeye.com |
NOMINATION HIGHLIGHTS
More than 91 percent of cybercrime begins with an email – and employees receive ~200 emails daily. Paired with the increase FireEye is seeing in social engineering attacks – including the use of malicious URLs using HTTPS, phishing attempts, new impersonation techniques, and cloud-based attacks focused on file-sharing services – the growing danger is that threat actors are targeting employees who may not be prepared to identify attacks, and many services that aren’t designed to protect them.
Email is a favorite attack vector for distributing malware. Bad actors are continually adapting their techniques to improve their ROI. In the past year, FireEye has observed a shift from malicious attachments or code to malware-less scams like spear phishing emails wrapped in impersonation packages.
FireEye Email Security counters both breeds of threats. It not only blocks attachments weaponized with malware, but it also seeks and destroys fraudulent wire transfer requests, URL links to credential phishing sites, and other social engineering and impersonation techniques. Whatever the malicious tactic is, FireEye is quick to identify it and block it by leveraging first-hand intel on attacks and adversaries.
Frontline insights help us keep FireEye Email Security in lockstep with attackers, stopping threats with first-hand knowledge of attacks/attackers before they become more serious incidents – blocking not only malware and suspicious URLs, but also phishing and impersonation techniques.
FireEye has built a collection of proprietary URL defense and attachment detonation technologies, as well as threat intelligence, machine learning and deep relationship analysis capabilities, to help our customers identify true positive alerts.
FireEye Email Security’s high detection efficacy and low false positive rate minimizes organization’s operational costs. And with inline deployment, its ability to spot threats early, minimizes potential damage from incidents. This results in annual operating expense savings.
How we are different
• All corporations use email and need to safeguard sensitive company data. FireEye Email Security has helped customers by detecting threats other solutions in front of it miss, reducing risk and saving the security team’s time. Over-taxed security teams aren’t wasting time investigating spurious alerts. Thinly stretched teams can’t chase false positives. FireEye Email Security identifies true positive alerts in just four minutes. Investing in FireEye Email Security far outweighs the business impact of an email-borne breach. In fact, independent leading insurers have designated FireEye Email Security and FireEye Endpoint Security as solutions that can have a meaningful impact on reducing major cyber risks like data breaches, business interruption, data theft or corruption, and cyber extortion.
• FireEye collects extensive threat intelligence on the frontlines and draws on this evidence and context to drive forward detection capabilities within our products. FireEye sees more evil than anyone else as we integrate the frontline knowledge of our incident response and managed defense teams to ensure our products do what matters most – protect against the latest breaches – whether in the cloud or on-prem. As a recent, real example, FireEye Email Security detected thousands of impersonation tactics per day that the incumbent AVAS solution missed. This resulted in the Fortune 100 customer deciding to rip out the incumbent and replace it with our single email security solution.
Attackers are constantly adapting their tactics to get past email security defenses. FireEye Email Security continues to address these landscape changes to detect the malicious emails that get past other services. The full Secure Email Gateway results in advanced threat protection for outbound and inbound messages. It delivers award-winning phishing URL detection and can detect malware-less credential phishing pages previously unknown or targeting specific brands. It also provides custom YARA rules for inbound and outbound messages.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



