Photo Gallery

|

|
Forescout for OT Security

Additional Info
| Company | Forescout |
| Company size | 1,000 - 4,999 employees |
| World Region | North America |
| Website | https://www.forescout.com/ |
NOMINATION HIGHLIGHTS
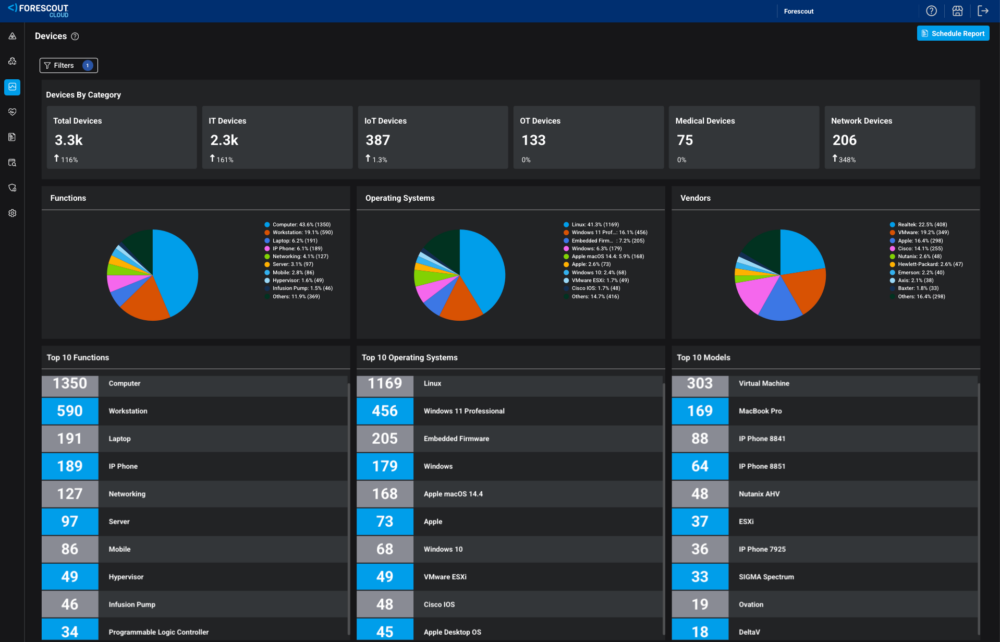
Complete security starts with an accurate inventory of all assets, where they are located and their compliance status. With the rapid digitalization of critical infrastructure and manufacturing environments – often geographically dispersed across large sites – accurately identifying and managing all OT, IoT, and IT assets is increasingly challenging. Moreover, industrial assets use proprietary protocols and are more fragile than most, making them and the processes they support difficult to identify.
Discovery approaches that work for IT and IoT might not work for sensitive OT devices given safety rules, vendor interoperability issues, industrial process requirements, and other considerations. When OT devices control critical infrastructure, there can be no downtime or service disruptions. Therefore, non-intrusive passive monitoring or agentless techniques are required.
Forescout offers continuous discovery of all cyber assets across all networks, providing full visibility into OT/ICS networks that detect cyber threats before they lead to operational or security incidents. In-depth asset management and monitoring of OT networks and device types employs more than 30 passive and active discovery techniques, identifying assets, their location and cyber posture, and to detect anomalies. This includes deep packet inspection (DPI) of 300+ IT, OT, and IoT protocols as well as carefully selected active queries for OT/ICS to query selected endpoints, including industrial controllers and network infrastructure for complete device visibility, well beyond SPAN.
Unlike other vendors that focus on visibility, the Forescout platform goes much further and delivers control capabilities to automate orchestration, remediation, containment, segmentation, and enforcement to ensure security and compliance across managed, unmanaged, and unagentable devices. Whether organizations are transitioning to the cloud, maintaining air-gapped systems, or managing hybrid infrastructures, Forescout for OT Security seamlessly adapts to the specific needs of customers, offering scalable deployment across OT, IoT, IoMT, and IT systems without limitations.
Key Capabilities / Features
Forescout for OT Security provides a single, streamlined solution, minimizing manual errors and helping to reduce the complexity of operational workflows. Key features include:
• More Deployment Options: Whether deploying in the cloud, using Docker containers on custom hardware sensors, or leveraging network equipment, this IT and OT security platform integrates seamlessly across different layers of existing infrastructure, minimizing disruption and avoiding unnecessary changes.
• Extended Discovery Capability: Forescout for OT Security supports 350+ industrial protocols with a blend of active and passive methods to discover and classify IT, OT, and IoT assets. Whether the user is pulling data from APIs, switches, or wireless adapters, the platform handles scenarios where SPAN monitoring isn’t an option or passive methods fall short.
• AI-Enhanced Asset Intelligence: Forescout for OT security gives actionable insights around how assets are configured and how they interact with other systems to effectively manage and optimize change, vulnerability, risk, and compliance processes.
• Proactive Vulnerability Management: With the industry’s largest curated database and actionable vulnerability prioritization metrics, such as CVSS, EPSS, CISA, and Forescout Vedere Labs’ KEV, organizations can better evaluate threats from multiple angles, managing complex patch management processes in industrial settings.
• Intelligence-Driven Detection: Organizations gain comprehensive threat detection tailored to OT, IoT, and IT hybrid environments all powered by Forescout Vedere Labs research. With advanced event classification and case management, organizations can efficiently manage alerts, track incident resolution, and monitor KPIs to ensure faster response times and superior event handling.
• Forescout AI Reporting: Persona based dashboards and customized views ensure that the right data reaches the right people. Custom views can be created for IT and security operations, SOC analysts, and executives. Organizations can then turn the views into customized reports that provide contextual insights into devices, alerts, potential incident causes, and recommended remediation steps.
How we are different
• Forescout for OT Security is the first security solution that allows organizations to secure complex, heterogeneous OT, IoT, IoMT, and IT environments whether they are fully in cloud, completely air-gapped, or hybrid. Forescout offers a comprehensive end-to-end IT and OT security platform that not only supports multiple use cases —such as extending IT security controls to industrial environments or consolidating risk and compliance into a unified strategy—but also enables organizations to act. The platform integrates seamlessly with IT and security ecosystems to proactively create, optimize and automate remediation and operational workflows.
• Forescout offers a continuously expanding Industrial Threat Library and ICS-specific indicator of compromise (IOC) and common vulnerabilities and exposures (CVE) database to passively identify any threat to operational continuity and assess every connected asset’s risk. Updated regularly, it contains thousands of behavioral checks and threat indicators to protect asset owners from advanced cyberattacks, network misconfigurations and operational errors.
• Forescout provides a unique Asset Risk Framework that calculates two risk scores for each asset, evaluating both cybersecurity and operational risk. Based on impact, they are continuously refreshed using detected events associated with the asset, proximity to other potentially infected or misbehaving assets, communication links, known vulnerabilities and other details. These multifactor risk scores enable OT engineers and security teams to make informed decisions and prioritize the right actions.


