Photo Gallery
 |

 |
Fortra’s Core Impact Penetration Testing

Additional Info
| Company | Fortra™ |
| Company size | 1,000 - 4,999 employees |
| World Region | North America |
| Website | https://www.fortra.com/ |
NOMINATION HIGHLIGHTS
Core Impact is designed to enable security teams to conduct advanced penetration tests with ease, allowing you to safely test your environment using the same techniques as today’s attackers. Organizations can maximize their resources with certified exploits and guided automations, providing valuable insights that will help mitigate risk and protect essential assets. Users can efficiently execute common tasks, saving time while providing a consistent, repeatable process for their testing infrastructure. Additionally, Core Impact allows you to quickly re-test exploited systems to verify that remediation measures or compensating controls are effective and working.
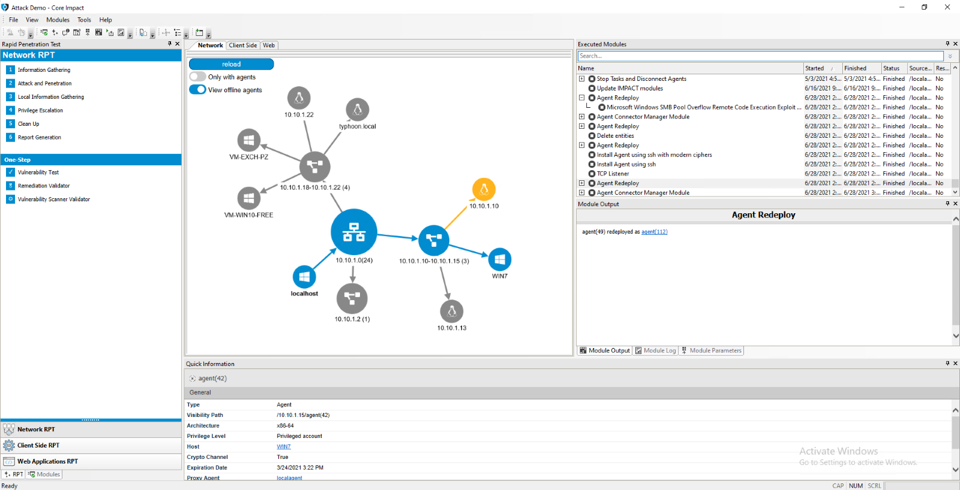
Core Impact can help exploit vulnerabilities in critical networks, systems, hosts, and devices by imitating an attacker’s methods of access and manipulating data, as well as testing defensive technologies’ ability to stop attacks. Users can gain further insights with Core Impact’s attack map, a network graph that illustrates a real-time overview of attack chains, pivoting and any other activities completed during testing. Run web application penetration tests to find weaknesses through detailed web crawling, pivoting attacks to web servers, associated databases, and backend networks to confirm exploitability.
Core Impact can also deploy phishing campaigns for client-side social engineering tests to discover which users are susceptible and what credentials can be harvested. Use the step-by-step process to create emails, select targets, and choose between browser redirects or web page clones. Challenge users with more sophisticated, tailored spear-phishing emails that are harder to identify as fake. Actual emails can be imported from mail clients to increase the authenticity of the attack.
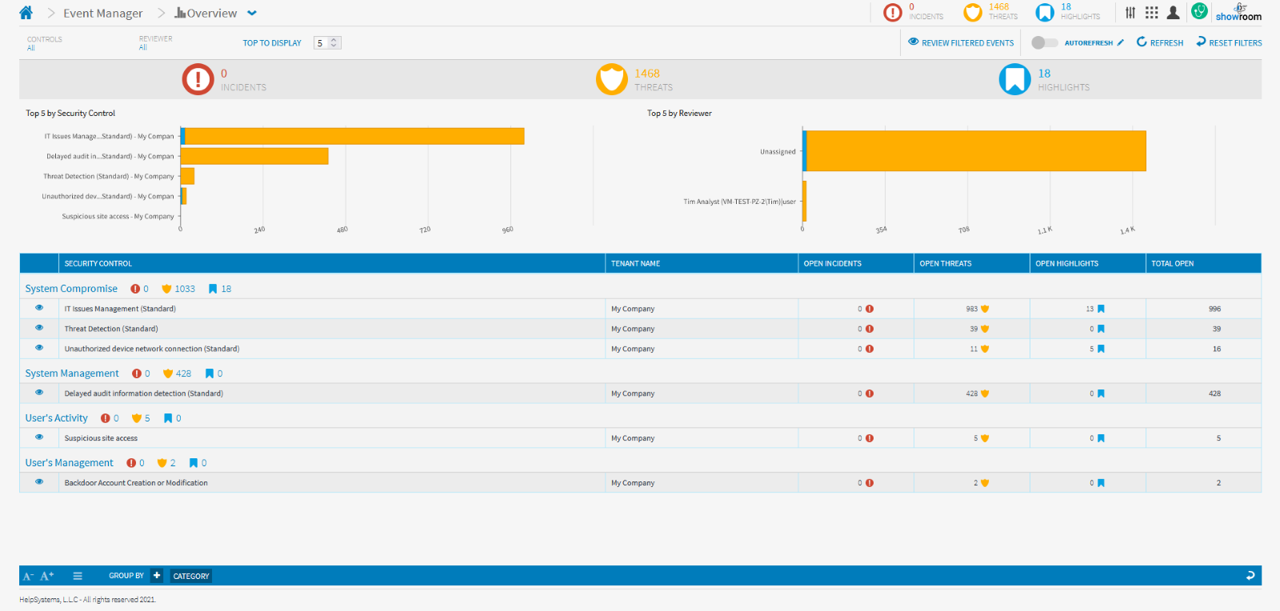
Multiple regulations require that organizations have regular assessments of their security infrastructure to ensure sensitive data is properly protected. Core Impact provides an easy to follow and established automated framework that can support industry requirements and standards, including PCI-DSS, CMMC, GDPR, and NIST.
Key Capabilities / Features
- Rapid Penetration Tests (RPTs) features are easy-to-use automations designed to perform routine, repetitive tasks. Thus, processes are simplified and the efficiency of your security team is maximized, so that your experts can dedicate their time to more complex problems.
- Core Impact uses a stable and continually updated library of commercial certified exploits to test against real threats. New exploits are updated in real time, as soon as they are available.
- Core Impact has the ability to perform multi-vector pen testing to replicate attacks across network infrastructure, endpoints, web, and applications. This help security professionals uncover a wide variety of vulnerabilities and helps security teams remediate risks quickly.
- Core Impact integrates with other security testing tools, such as Cobalt Strike, Metasploit, PowerShell Empire, and Plextrac, to centralize your testing environment and extend your security program.
- Core Impact allows multiple pen testers to interact in the same session, allowing them to securely share data and delegate testing tasks. Shared workspaces give you a joint view of network targets that have been discovered and compromised, making your team work more efficiently.
How we are different
- Automated Rapid Penetration Tests (RPTs) to help optimize the use of your security resources by simplifying processes, maximizing efficiency, and enabling pen testers to focus on more complex issues.
- An up-to-date library of commercial-grade exploits to reveal how chains of exploitable vulnerabilities open paths to mission-critical systems and assets.
- Multi-vector testing capabilities with the ability to replicate attacks across network infrastructure, endpoints, web, and applications.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



