Photo Gallery
 |

 |
Fudo PAM

Additional Info
| Company | Fudo Security |
| Company size | 50 - 99 employees |
| Website | http://www.fudosecurity.com |
NOMINATION HIGHLIGHTS
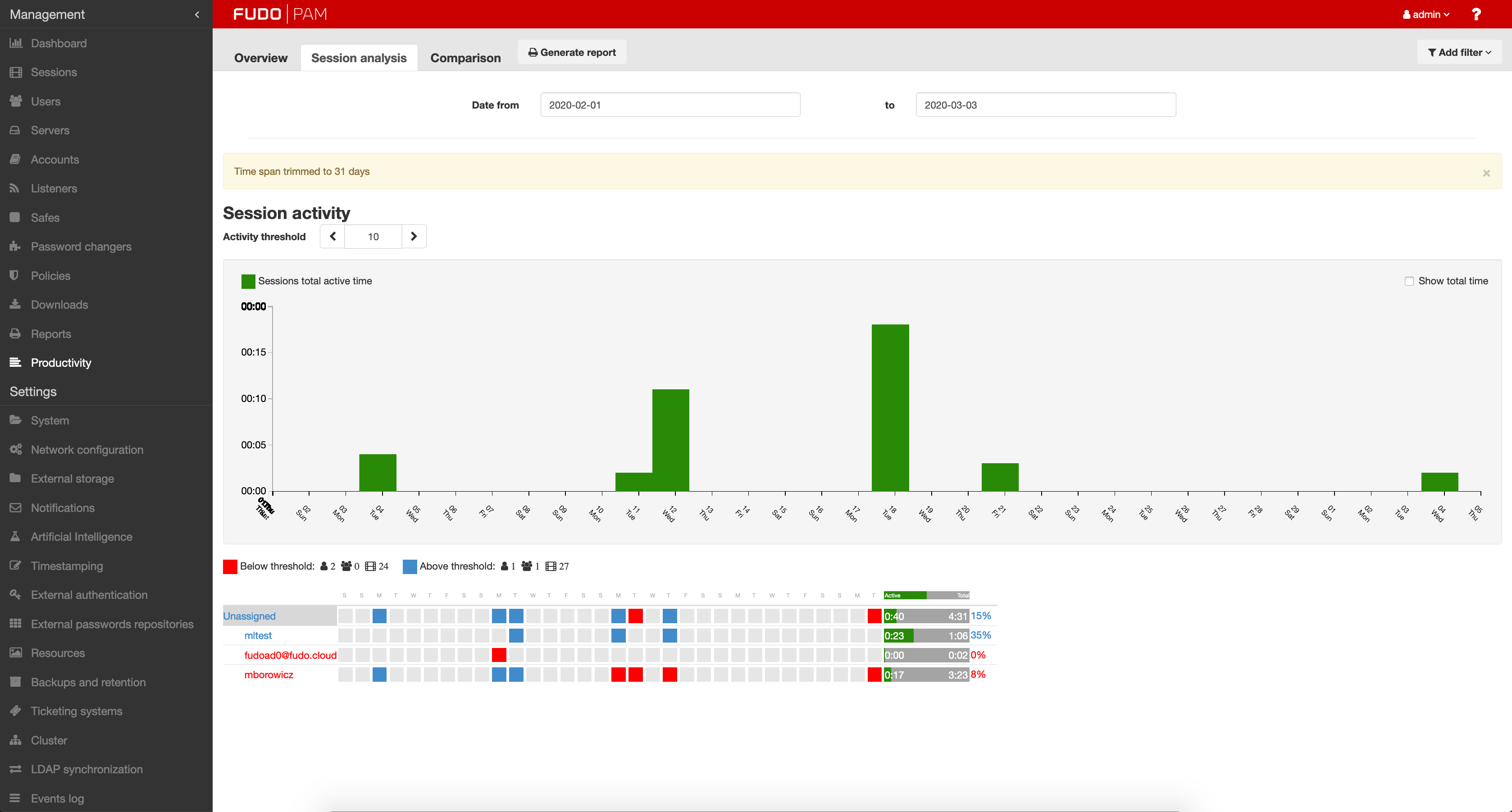
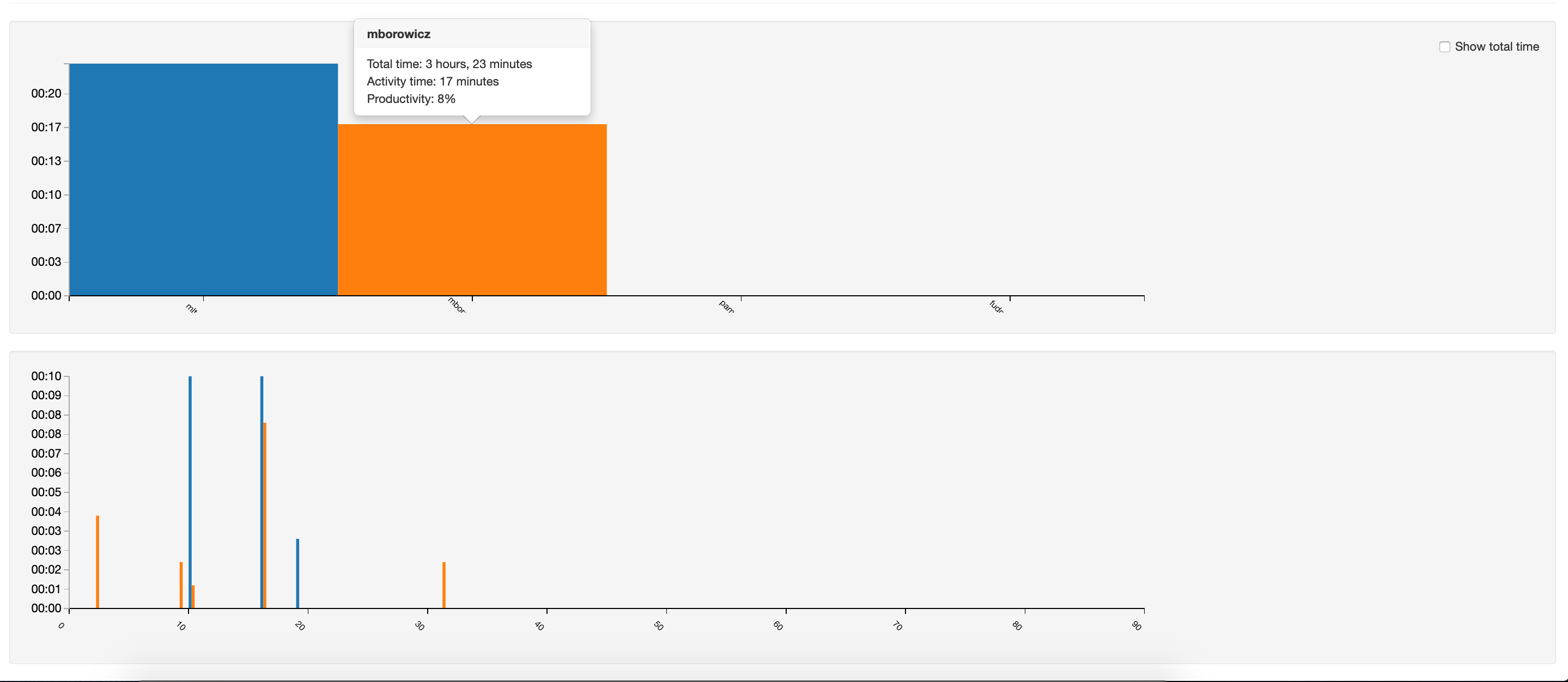
Fudo enables secure remote access to the company’s IT resources. It covers all possible scenarios: from 3rd party contractors accessing your critical infrastructure to thousands of employees accessing their office workstations from home. Remote users can access monitored systems through a proxy or by using a convenient Web Access Gateway, which can be published over the Internet for a VPN-less experience and still maintain a high level of encryption and infrastructure separation backed by Fudo’s built-in SSH and RDP protocol web clients and use of multi-factor authentication schemes.
With Fudo’s ability to separate user credentials from IT infrastructure credentials and just-in-time session setup, Security Officers can deploy a ZTNA-backed access scenario in a matter of hours. Third parties can access your infrastructure without knowing the password to connect to servers, and users can work remotely regardless of the state of their endpoints – using User Access Gateway’s built-in RDP and SSH web clients virtually all trojans and rootkits cannot cross-over. And with a token/one-time-password authentication required for a login, even keyloggers are out of the picture hunting login data for malicious third parties.
How we are different
*Based on AI-backed mouse moves, Fudo PAM’s biometric analysis knows in seconds
that the session was taken over by an unauthorized user.
*All the ongoing sessions are being monitored, and, whenever something suspicious is
taking place, Fudo PAM sends alerts to the designated security personnel.
*Fudo’s award-winning technology has been recognized by clients, Gartner, and
KuppingerCole analysts in their recent studies.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



