Photo Gallery
|


|
GoodAccess Business VPN


Additional Info
| Company | GoodAccess |
| Company size | 10 - 49 employees |
| World Region | Europe |
| Website | http://www.goodaccess.com |
NOMINATION HIGHLIGHTS
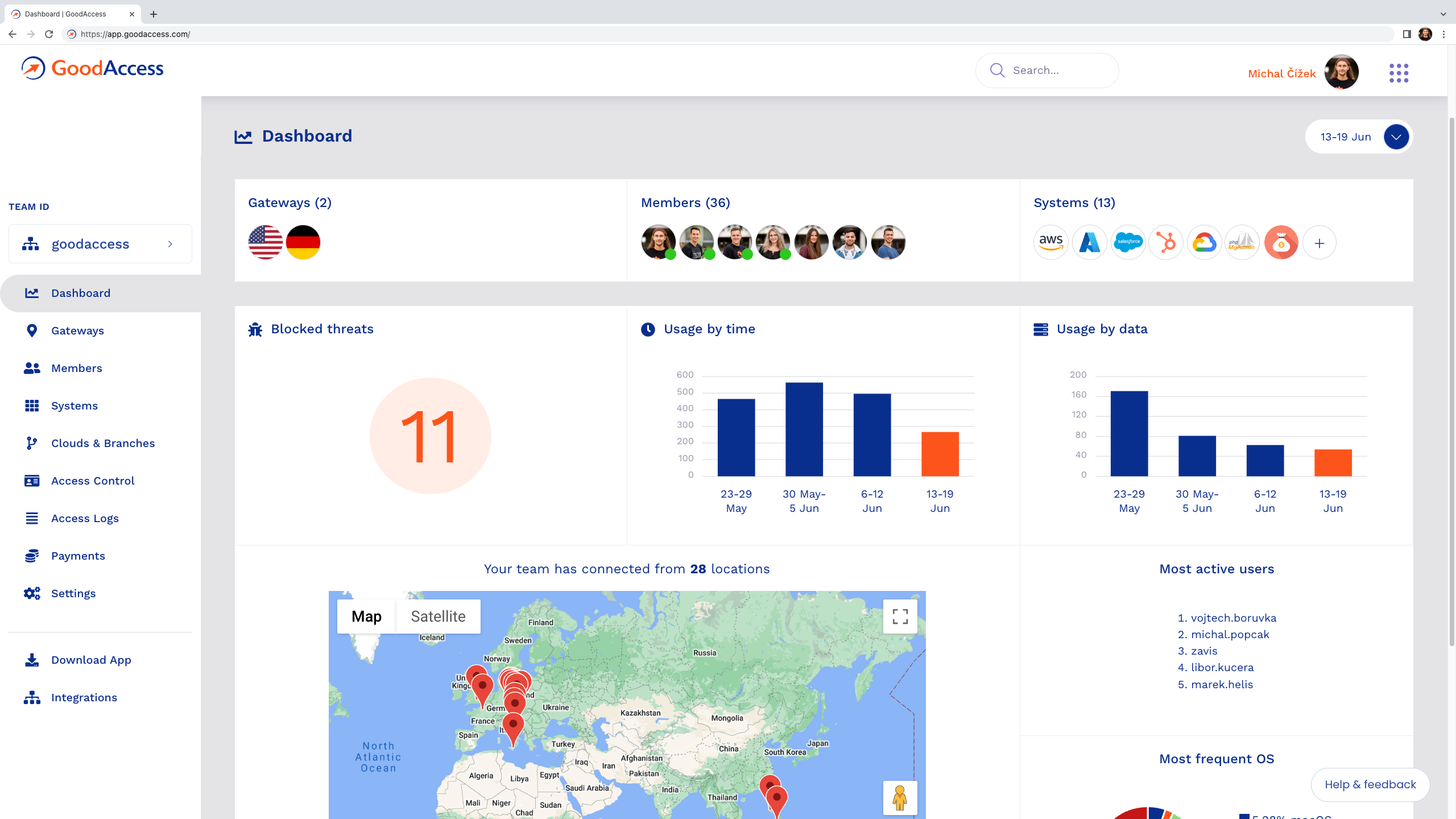
GoodAccess reinvents VPNs for small and medium businesses to meet the dynamics and demands of modern, digital business. GoodAccess is designed for both traditional and distributed companies that may or may not have their own networks. Most newer companies, even those with physical office locations, may not have a network. For those companies, the Internet is their network. GoodAccess embraces this reality by creating a true, protected, deterministic network for each company across the internet. GoodAccess securely connects employees and other users to the company’s cloud-base applications, data storage and other resources. GoodAccess not only encrypts communications and interactions but uses white listing, blacklisting, threat intelligence, fixed IP addresses, advanced authentication, device state security checks, flexible policy-based rules and other technologies to protect users, defeat malware, phishing and ransomware, guard against credential and access theft and protect and manage applications, data and other resources.
GoodAccess knows that today, VPNs must be more than just point to point encryption. GoodAccess is designed as a complete security suite and incorporates Zero Trust Network Access to secure and protect small and medium businesses at price points they can afford while making set up and the capabilities easy to manage. GoodAccess provides a robust VPN for companies with up to 100 users free of charge—GoodAccess Starter—for an unlimited period of time with many but not all security features. It can be upgraded to the full security VPN platform at any time as the company grows or as it wants to add capabilities, such as Zero Trust.
GoodAccess has created a VPN platform for small and medium businesses in today’s world.
How we are different
- GoodAccess provides a unique VPN cloud for each organization, enabling encrypted internet access and online threat protection for remote employees, network-less offices and cloud resources and applications. No hardware or complex set-up is required, as the platform is fully cloud-based and designed to deploy in less than 10 minutes.
- GoodAccess extends secure private browsing and use of cloud applications to each employee, protecting their identity, devices and connections. Encrypting the network layer in browser-based communications provides privacy and protects against phishing and malicious software attacks from compromised websites. GoodAccess provides fixed IP addresses and white and black listing for deterministic, controlled connections. GoodAccess includes advanced authentication, device state security checks, flexible policy-based rules and other technologies to protect users, defeat malware, phishing and ransomware.
- GoodAccess also incorporates zero-trust access controls for further protection. It provides the easiest way for small and medium companies to add zero trust without undue complexity and expense. For many companies this means the ability to add zero trust when it would otherwise be impossible.


