Photo Gallery
 |
 |
Gurucul Insider Threat Solution

Additional Info
| Company | Gurucul |
| Company size | 100 - 499 employees |
| Website | https://gurucul.com/ |
NOMINATION HIGHLIGHTS
Malicious insiders motivated by sabotage, espionage, fraud, or competitive advantage typically carry out attacks by abusing their account access and/or physical devices. These individuals (or groups) can be employees, contractors, third parties, and visitors who are given access to accomplish their work. They can also be outsiders who are impersonating an insider. These factors make it extremely difficult for enterprises to identify and prevent insider threats. In fact, the 2020 Insider Threat Report conducted by Cybersecurity Insiders revealed that only 5% of organizations reported they are “not at all vulnerable” to insider threats, while 68% said they are moderately to extremely vulnerable.
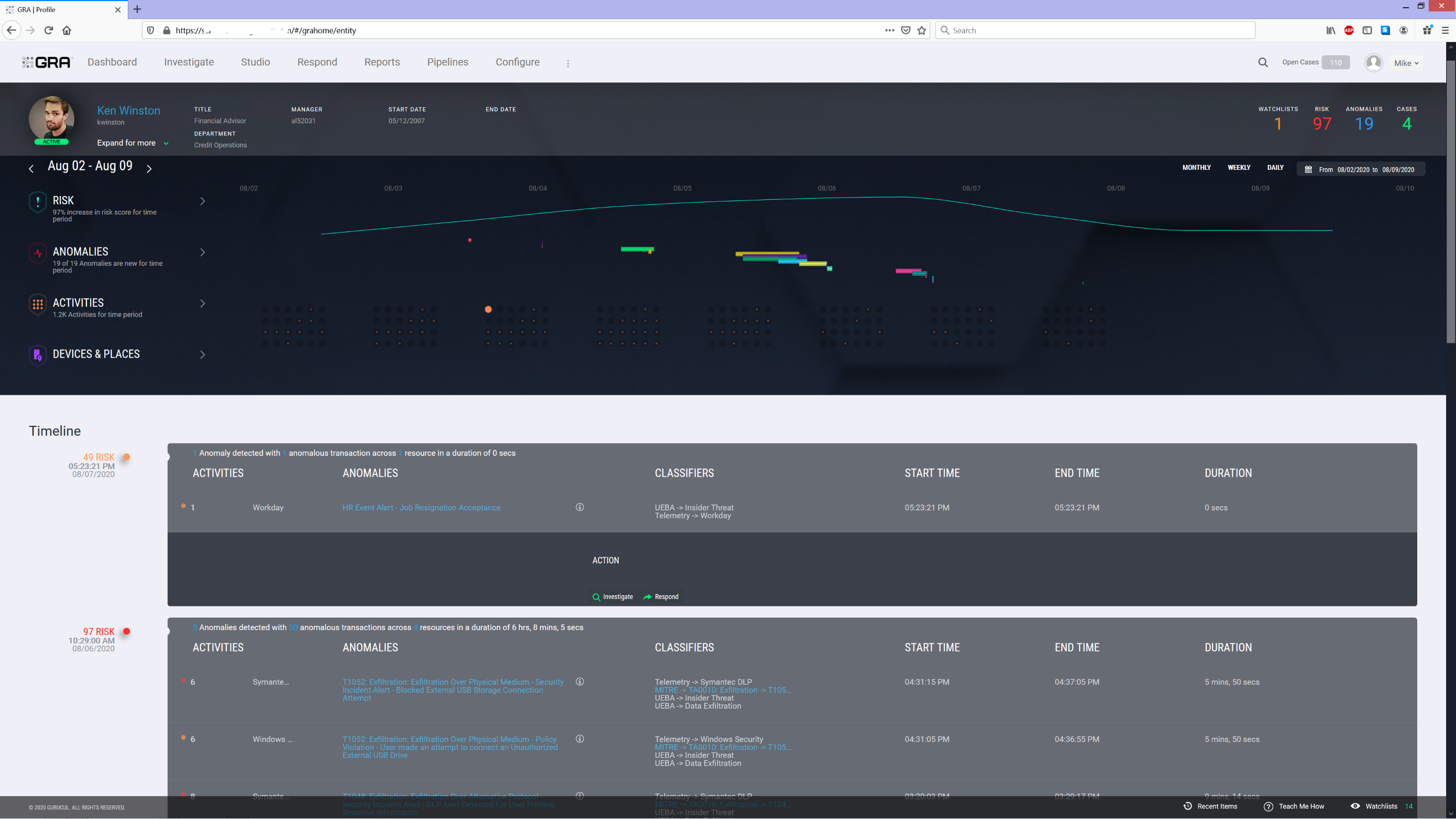
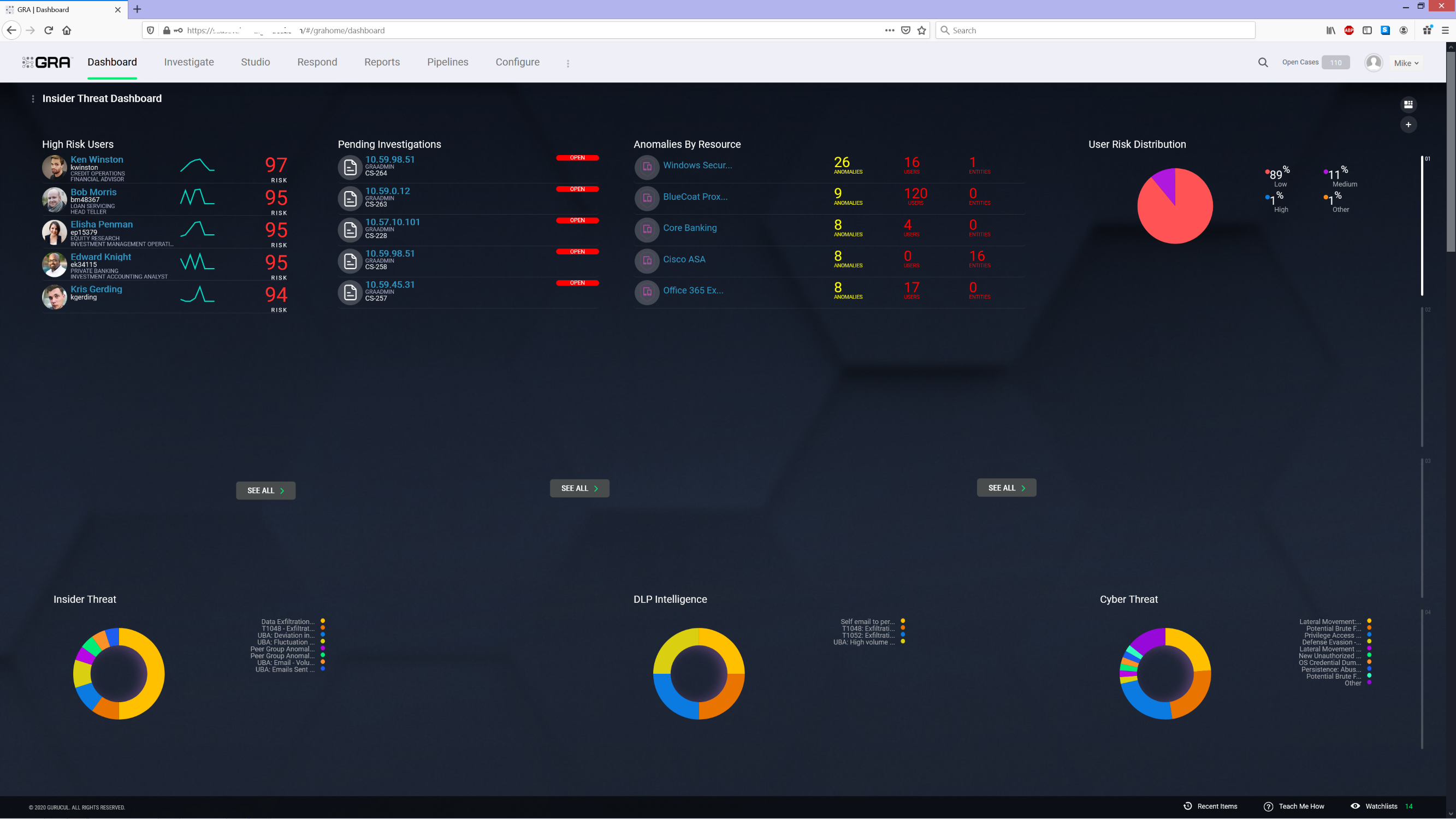
Gurucul Unified Security and Risk Analytics is a data science driven platform that unifies Cyber Defense Center functions to provide contextual, risk-prioritized decisions for threat detection and automation of security controls. Gurucul ingests and analyzes massive amounts of data from virtually any source, including network, IT systems, cloud platforms, applications, IoT, identity management solutions, and more. With the industry’s largest (2000+) advanced machine learning model library, identity-centric data science, anomaly detection and predictive risk-scoring algorithms, Gurucul zeros in on abnormal behaviors and activities that are indicative of security threats. Through real-time contextual, risk-prioritized alerts, Gurucul provides automated detection and mitigation.
Gurucul has innovated the most effective technology for detecting insider threats without generating high volumes of false positives. Gurucul creates time-based behavioral baselines and continuously learns what is acceptable behavior in order to detect anomalies and zero in on actual threats. By unifying the entire security stack and applying AI/ML driven security analytics to collected data, Gurucul provides unprecedented context, behavioral indicators and timeline views for automating threat assessment, mitigation and response. Gurucul not only detects and prevents malicious insider activities, but also fraud, account compromise, data exfiltration, ransomware, APT/stealth attacks and social engineering exploits.
How we are different
- For the last decade, Gurucul has helped organizations worldwide deter, predict, detect, and remediate insider threats. Often organizations are unaware of the extent they’ve been at risk. Sometimes they’ve already been compromised by malicious insiders. For instance, within a week of being deployed by a customer, Gurucul identified a group of users who were downloading and exfiltrating intellectual property from their employer. Armed with this information, the company was able to quickly shut down the insider operation that Gurucul revealed had been occurring for weeks without their knowledge. In another example, a manufacturing company deployed Gurucul in a proof of concept. Gurucul revealed that their product’s bill of materials had been accessed by a foreign nation and had been compromised for more than 18 months without their knowledge. This company became a Gurucul customer, and since then Gurucul has discovered and prevented malicious insider activities including fraud in their call centers and shut down credit card theft rings.
- Gurucul aggregates and links identity, access, and activity data. The solution analyzes who or what is on the network, what they are doing, what they have access to, and what they are doing with that access. It identifies abnormal behaviors and activities associated with potential sabotage, data theft, misuse, etc. Gurucul is highly accurate and prescient and has predicted the departure of disgruntled employees, while preventing them from exfiltrating data, committing fraud and sabotaging systems.
- Gurucul’s unique Self-Audit mechanism provides reports for employees to proactively monitor for suspicious access, fraud and activity on their accounts. One employee at a financial services firm notified their security team that they had not been online that day but the report showed suspicious activity. An investigation confirmed an intruder had gained access to the high-privilege account and activity was stopped before damage could

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



