Photo Gallery
|


|
HAC-1 Hardware Access Control


Additional Info
| Company | Sepio Systems |
| Company size | 10 - 49 employees |
| Website | http://www.sepio.systems |
NOMINATION HIGHLIGHTS
Hardware attacks are proliferating due to a general lack of security in this realm which diminishes the obstacles in the perpetrator’s way. With enterprises using an abundance of devices, there are more entry points for attackers.
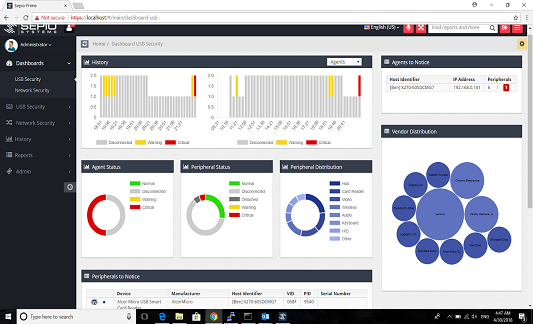
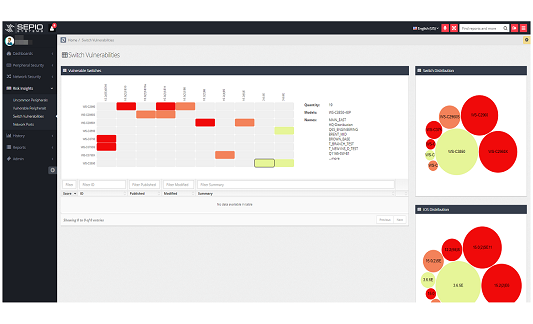
Increasing this risk is that enterprises are often unaware of all the devices operating on their USB and network interfaces, let alone which of those devices are vulnerable. Tackling this challenge requires complete visibility to your Hardware assets, regardless of their characteristics and the interface used for connection, as attackers take advantage of the “blind” spots mainly through USB Human Interface Device (HID) emulating devices or Physical layer network implants. With this complete visibility, including Rogue Devices that are spoofing legitimate devices, Sepio Systems HAC- 1 solution indicates which of the enterprise’s assets are acting abnormally and subsequently triggers an alert for those that are. Sepio’s HAC- 1 solution reassures organizations that all their devices are accounted for and, importantly, that any vulnerabilities are detected. Hardware attacks are often
initiated at third parties which are perceived as less secure, with the intention of the attack tool eventually reaching the end user. Additionally, due to COVID- 19, BYOD and IoT policies are becoming more frequently enforced as WFH is becoming common practice. This presents of myriad of hardware risks since there are more devices being
used, with fewer security measures in place.
How we are different
Physical layer detection of Rogue Devices (Network implants, spoofing devices, USB HID emulators etc.)
Complete visibility for every device connected - managed/unmanaged , visible or transparent.
Policy enforcement for Federal requirements (889 and higher levels of CMMC)


