Photo Gallery
 |
 |
Haystax for Insider Threat Mitigation


Additional Info
| Company | Haystax |
| Company size | 50 - 99 employees |
| Website | http://www.haystax.com |
NOMINATION HIGHLIGHTS
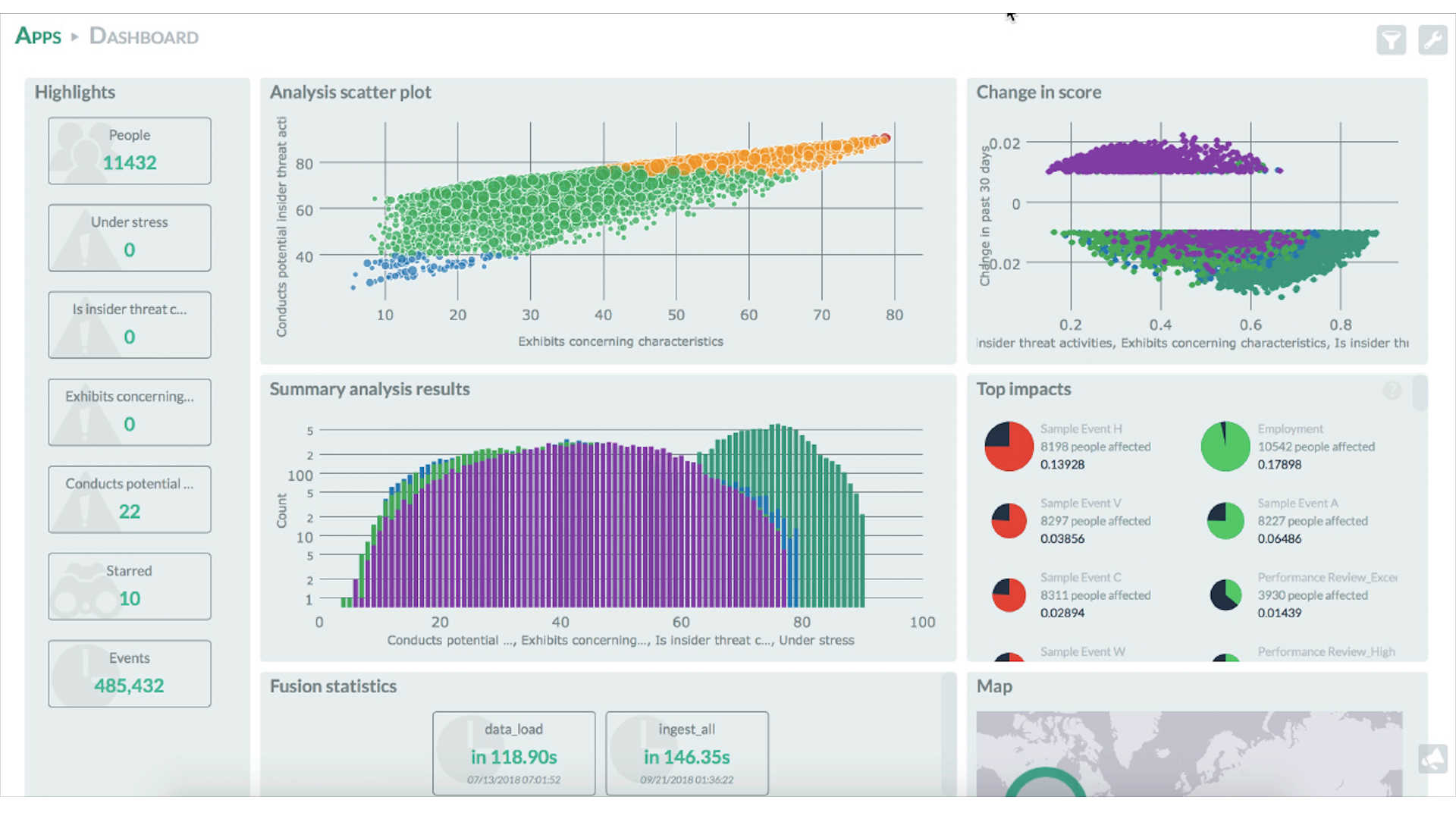
Haystax for Insider Threat Mitigation continuously measures the trustworthiness of personnel in an organization, pinpointing early indications of risk from IP theft, espionage, fraud and other harmful events. Our software ‘reasons’ like a team of expert analysts, but at a volume and velocity that no human could sustain. It performs true all-source analysis by ingesting data from a wide variety of sources and then applying probabilistic models, machine learning and other AI techniques to connect the dots.
Conventional analytics solutions typically find insider threats only after an adverse incident has occurred. The Haystax solution proactively identifies key personnel risk indicators, even in weak signals or subpar data sets, while filtering out 97 percent of the false positives. As a result, SOC analysts have a clear picture of their highest-priority threats and can respond immediately as a threat is emerging — before any harm has been done.
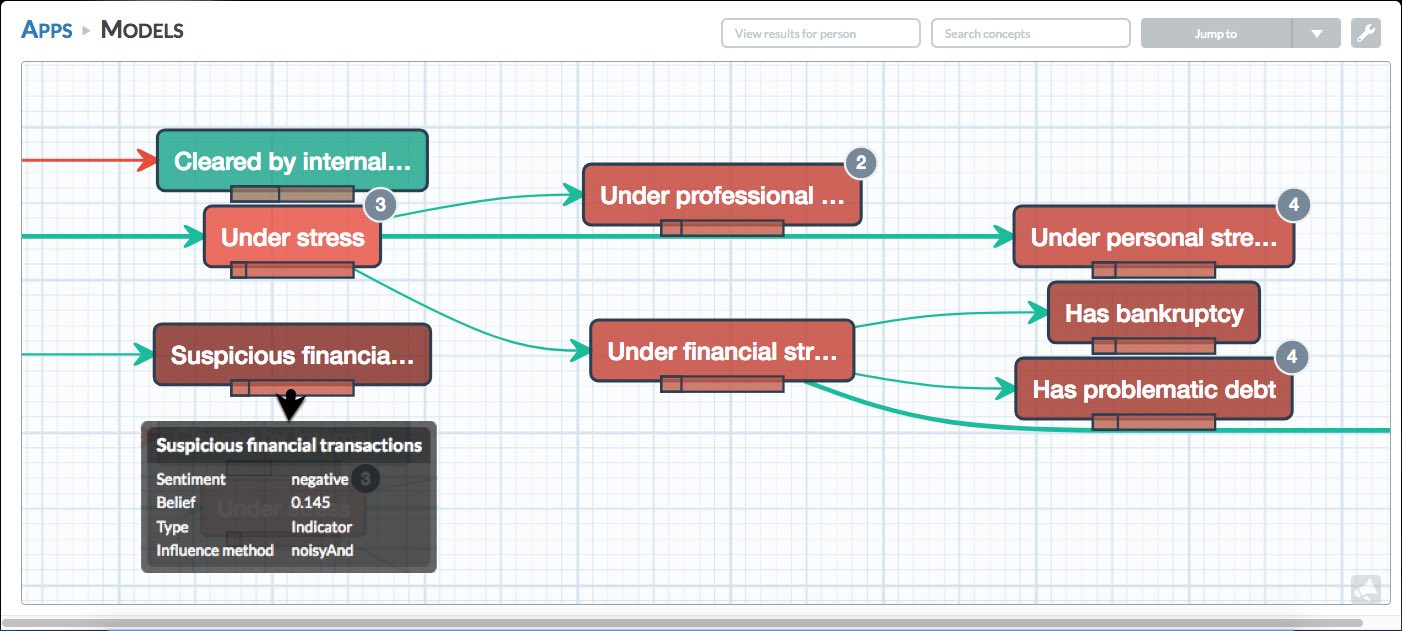
Haystax data scientists have encoded the judgments of diverse insider threat experts into a ‘whole-person’ Bayesian model representing hundreds of behavioral indicators of trustworthiness. Data fed into the model can come from internal repositories such as HR records, printer and access control logs and network monitoring devices, and from public sources like digital media feeds and criminal and financial records. The Haystax platform continuously analyzes new information to quickly detect evidence that an individual has started trending in a negative direction.
The Haystax platform supports collaborative workflows and adheres to existing organizational standards and best practices. With our easy-to-use interface, an analyst can discern trends or receive automated alerts to quickly identify the riskiest outliers – investigating their histories and records, conducting assessments, identifying related incidents and recommending responses. And because the Haystax platform runs at machine scale and can be reconfigured on the fly, organizations don’t have to hire more analysts as their threats evolve.
How we are different
Haystax for Insider Threat Mitigation is:
1) The first insider threat software platform to combine probabilistic modeling and other artificial intelligence techniques with a wide array of ingested data sources to provide a 'whole-person' view of insider risk in organizations of any size.
2) The best solution for maximizing a SOC team’s productivity, accomplished by automating substantial portions of triage, investigations and response operations, and by providing flexible and intuitive data visualization capabilities. Haystax does the heavy lifting so the SOC team can focus on its highest-priority insider threats.
3) The only analytics approach that focuses on individuals rather than on devices or networks, and that can identify negligent and unwitting insiders in addition to those with malicious intent.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



