Photo Gallery
 |
 |
HYAS Protect

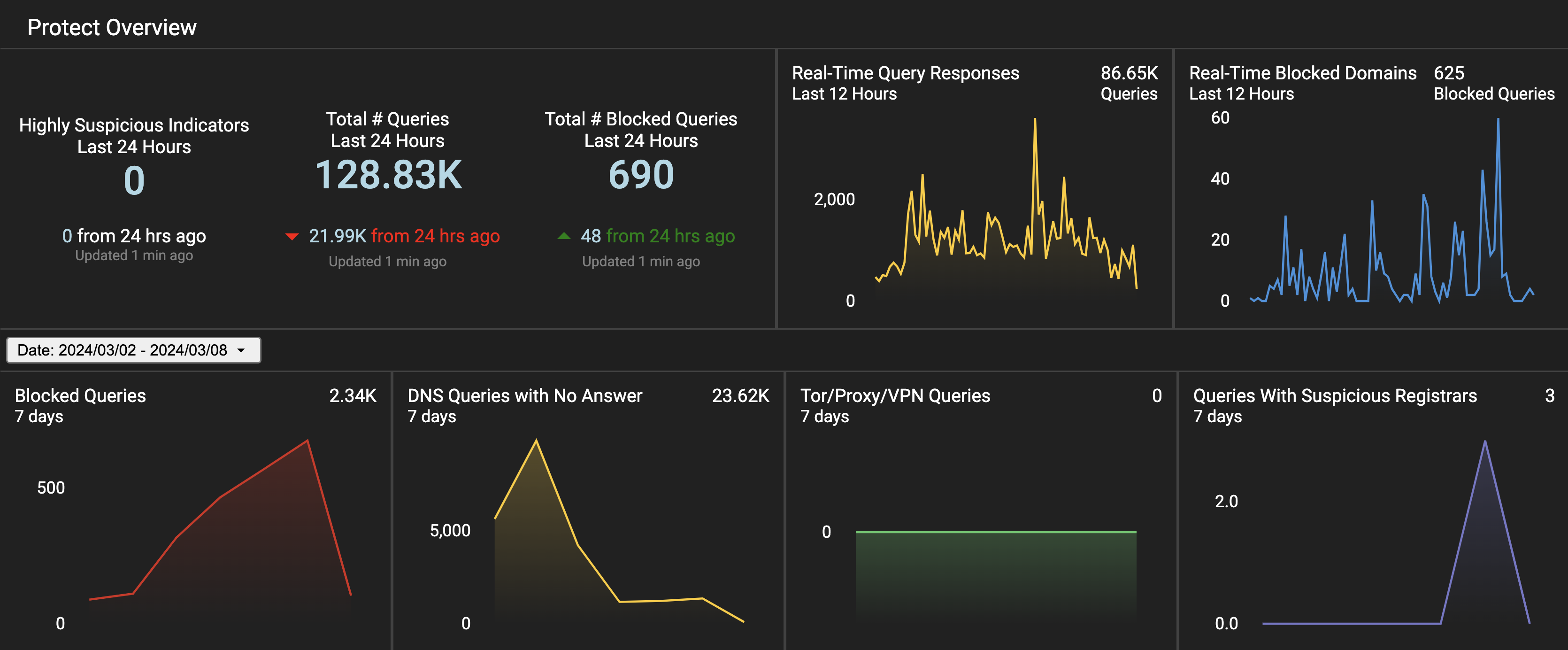
Additional Info
| Company | HYAS |
| Company size | 10 - 49 employees |
| World Region | North America |
| Website | https://www.hyas.com |
NOMINATION HIGHLIGHTS
HYAS Protect protective DNS safeguards against cyber threats in today’s interconnected landscape. In a world where bad actors continually seek access, our solution offers a transformative approach to defense. Traditional cybersecurity measures focus on keeping threats at bay, yet detecting malicious activities once a breach occurs remains a significant challenge. Enter HYAS Protect: a cutting-edge Protective DNS technology that revolutionizes network defense.
Our solution intercepts malware’s initial communication attempts, effectively halting attacks before they can unfold. By preventing the beaconing out for instructions that malware typically initiates, we render it inert, safeguarding against data breaches, ransomware outbreaks, and other malicious activities. This capability aligns with the directives set forth by CISA and the NSA, positioning Protective DNS as the last line of defense in today’s cyber battleground.
What sets HYAS Protect apart is its unparalleled visibility into DNS activity. By providing insights into the intricate network of communication between entities, our technology enables organizations to detect and mitigate threats with precision. This depth of insight not only enhances the efficacy of existing cybersecurity controls but also equips businesses with a key technical advantage to complement their cybersecurity posture.
With HYAS Protect, organizations gain more than just a defensive shield; they gain a strategic advantage in the ongoing battle against cyber threats. Our solution ensures that breaches are promptly detected and contained, preventing them from escalating into major incidents. Join us in revolutionizing network defense and safeguarding enterprises against the constantly evolving tactics of bad actors.
Key Capabilities / Features
Proactive Defense Against Breaches: Modern attack surfaces are porous and complex, and organizations are increasingly at risk. When attackers gain a foothold within a network, they have one weakness: they must communicate outwardly over the internet to receive instructions and execute malicious activities. This critical juncture is precisely where HYAS Protect takes action.
By swiftly identifying, detecting, and blocking such communication, we provide security teams with a crucial tripwire, alerting them to the intruder and enabling them to take action before damage is done.
Seamless Integration, Swift Deployment: With a focus on adaptability and ease of use, HYAS Protect seamlessly integrates into any IT environment, facilitating rapid deployment without the need for additional agents or sensors. Whether deployed independently or integrated with existing security solutions, its versatility ensures maximum efficiency across diverse network configurations.
Amplifying Security Investments: By complementing existing EDR solutions, HYAS Protect magnifies threat detection capabilities, elevating visibility and bolstering defenses against sophisticated adversaries. Its compatibility with popular security platforms further enhances interoperability, ensuring organizations derive maximum value from their security investments.
Compliance Assurance and Regulatory Alignment: Protective DNS solutions like HYAS Protect are mandated by governments around the world. Aligned with federal mandates and recommendations, including those outlined by CISA and the new European Union’s NIS2 Directive, HYAS Protect not only fortifies defenses but also aligns with an important part of Zero Trust architecture and frameworks like CMMC.
How we are different
+ Most solutions focus solely on preventing initial breaches, but HYAS Protect goes beyond this first step to detect and mitigate threats even when a breach occurs.
+ HYAS’ unique technology intercepts malware's initial outbound C2 communication attempts, effectively neutralizing attacks before they can unfold. HYAS renders malware inert by preventing its ability to beacon out for instructions, thereby thwarting data breaches, ransomware outbreaks, and other malicious activities.
+ By providing insights into the intricate network of communication between entities, our technology empowers organizations to detect and mitigate threats with precision so they can shift from a reactionary security stance to a proactive stance.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



