Photo Gallery
 |
 |
Hybrid Cloud Threat Intel

Additional Info
| Company | Infoblox |
| Company size | 500 - 999 employees |
| Website | https://www.infoblox.com/ |
NOMINATION HIGHLIGHTS
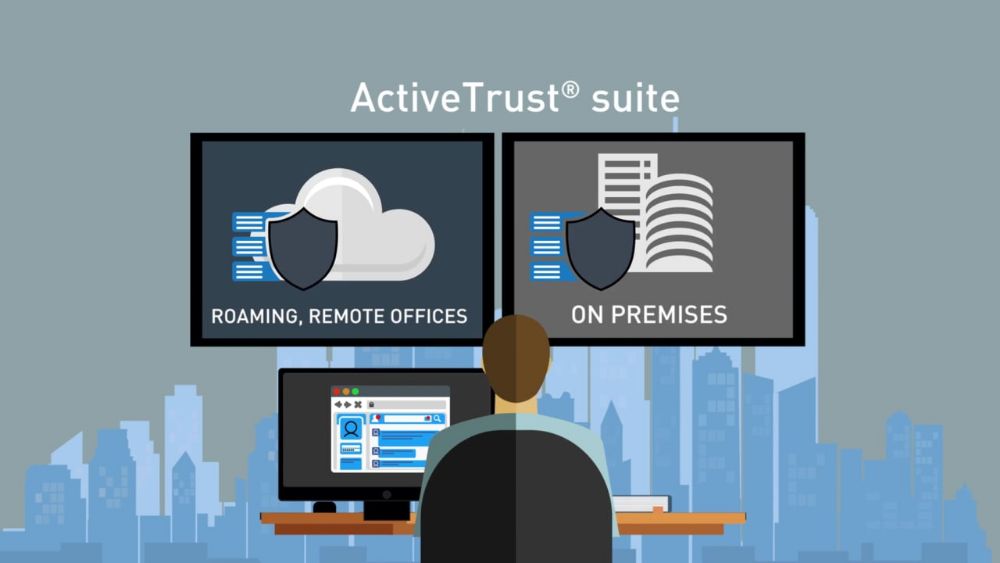
Infoblox ActiveTrust Cloud is the first and only hybrid approach to DNS security provided by a DDI vendor. It is a solution that blocks DNS-based data exfiltration, stops malware communications with command-and-control (C&C) servers, automatically prevents access to content not in compliance with policy, and shares intelligence with existing security infrastructure for orchestration and faster remediation. It is delivered as a service, therefore is easy to use, deploy, and maintain without dedicated IT resources.
How we are different
- Infoblox is the industry’s first and only DDI vendor to provide a hybrid approach to DNS security. This means its ActiveTrust Suite is able to protect devices anywhere – whether located on-premises or in the cloud. ActiveTrust Cloud is the first and only network security solution to block DNS-based data exfiltration through advanced analytics, and shares threat intelligence with enterprises’ existing security infrastructure and resources to help prioritize threat remediation. Infoblox protects more than 8,000 customers worldwide, including major brands such as Samsung, Adobe, Ford, Deloitte and Walmart
- ActiveTrust’s threat intelligence is aggregated by multiple internal and external sources, and filtered by Infoblox’s Cyber Intelligence Unit to minimize false positives of threats. From there, ActiveTrust gives IT teams the ability to share DNS indicators of compromise with security ecosystem vendors to take necessary action. Infoblox is the only DNS security vendor that provides a hybrid SaaS and on-prem model for delivering security to protect users everywhere with unified reporting and management.
-ActiveTrust Cloud was completely updated in 2018 to include new features like:
- Enabling security administrators to restrict access to certain types of content for policy enforcement
- Review non-compliant activity in the organization
- The capability to aggregate, curate and distribute threat intelligence across the entire security infrastructure in a customer’s environment
- The opportunity to seamlessly manage policy, provide unified visibility into devices on premise or while roaming and network context required to prioritize action.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



