Photo Gallery
 |

 |
Hysolate Platform


Additional Info
| Company | Hysolate |
| Company size | 10 - 49 employees |
| Website | http://www.hysolate.com |
NOMINATION HIGHLIGHTS
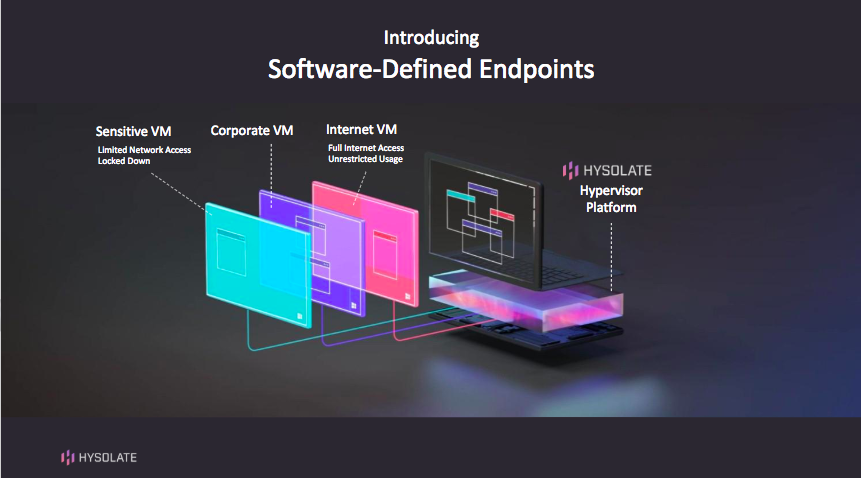
With cyberattacks targeting endpoints, many CISOs/CIOs lock down devices and limit what end-users can access. But as a result, user productivity takes a massive hit. The Hysolate Platform enables a radically different approach. It transforms end-user devices into software-defined endpoints, creating a fully unrestricted, seamless user experience that’s secure by design:
● Secure by Design
With Hysolate, which sits below the device OS, everything end-users do happens in virtualized desktops, running locally, side-by-side with full separation. These virtual environments are isolated using trusted, security-hardened hypervisor technology. Hysolate withstands any OS- or application-based threat, including zero-day.
● Transform Existing Endpoints
Hysolate’s unique ‘forklift’ automatically migrates endpoint fleets into the platform. It’s instant for end-users – just a single reboot. Users can work on sensitive and non-sensitive apps within the same familiar desktop. Hysolate launches apps in the right VM, connects external devices to designated VMs, and seamlessly and securely handles copy/paste between VMs, if enabled.
● Leverage Security Investments
Easily embed DLP, CDR, VPN, etc. on Hysolate.
Benefits:
● Boost User Productivity
Without Hysolate, end-users can’t be fully productive and attackers can infect endpoints. With Hysolate, end-users access, install and work with whatever websites, apps, external devices and cloud services they need, without security constraints or endangering/compromising corporate assets.
● Protect Privileged Users
Without Hysolate, even if networks are segmented, attackers compromising IT laptops can immediately access their command and control server and sensitive assets. And for those using separate privileged/non-privileged workstations, it’s counterproductive and costly. Hysolate eliminates this threat and the need for separate workstations. Malware on internet-exposed VMs cannot reach sensitive resources, which are only accessible via the privileged VM.
● Secure Payment Systems like SWIFT
Gain high-grade security of a physical air gap on a single endpoint. Attackers on internet-exposed VMs cannot use endpoints to reach payment systems as they run in a separate VM.
How we are different
● Hysolate is the only solution that transforms end-user devices into software-defined endpoints, where each endpoint has multiple, isolated VMs. This is secure by design, while enabling completely unrestricted user access and a much higher level of user productivity. Hysolate’s breakthrough, no-compromise approach solves the endpoint security vs. end-user performance problem CISOs have been struggling with by ensuring end-users can access the resources they need without endangering corporate assets.
● Hysolate contrasts with traditional agent-based approaches to endpoint security, where the software runs within the device OS. In those situations, enterprises typically use solutions from multiple vendors to cover a variety of threats (e.g. malware/viruses, phishing attacks, etc.), and even with half-a-dozen agents running they aren't fully protected, especially against zero-day attacks. Plus, all those agents impact device performance and are a pain for IT Operations, who must deploy and manage them. Hysolate’s secure-by-design approach protects from below the OS. It protects against zero-day vulnerabilities by air-gapping Internet-connected virtual desktops that are at risk of infection away from more secure corporate and sensitive environments. This architecture also helps organizations consolidate their agent-based security and even eliminate certain security products. Finally, Hysolate’s client hypervisor approach leverages the power of modern desktops/laptops to provide near-native performance for the vast majority of knowledge workers.
● Some CISOs and security pros use Virtual Desktop Infrastructure (VDI) and other “remote application” solutions as endpoint security barriers, thinking hackers will have difficulty breaching them. But in reality, remote Windows desktops are not really isolated and are still exposed to attack vectors, like email, web, external media and user-installed applications. Plus, hackers who control the physical devices that connect to the remote virtual desktop/app can control the remote resource. Anything short of a full endpoint isolation approach, which Hysolate uniquely delivers, puts corporate assets at risk.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



