Photo Gallery
 |
 |
illusive networks

Additional Info
| Company size | 50 employees |
| Website | http://www.illusivenetworks.com |
NOMINATION HIGHLIGHTS
illusive networks pioneers deception-based attacker post-penetration cybersecurity with its patent pending Deceptions Everywhere™ technology that neutralizes targeted attacks and APTs.
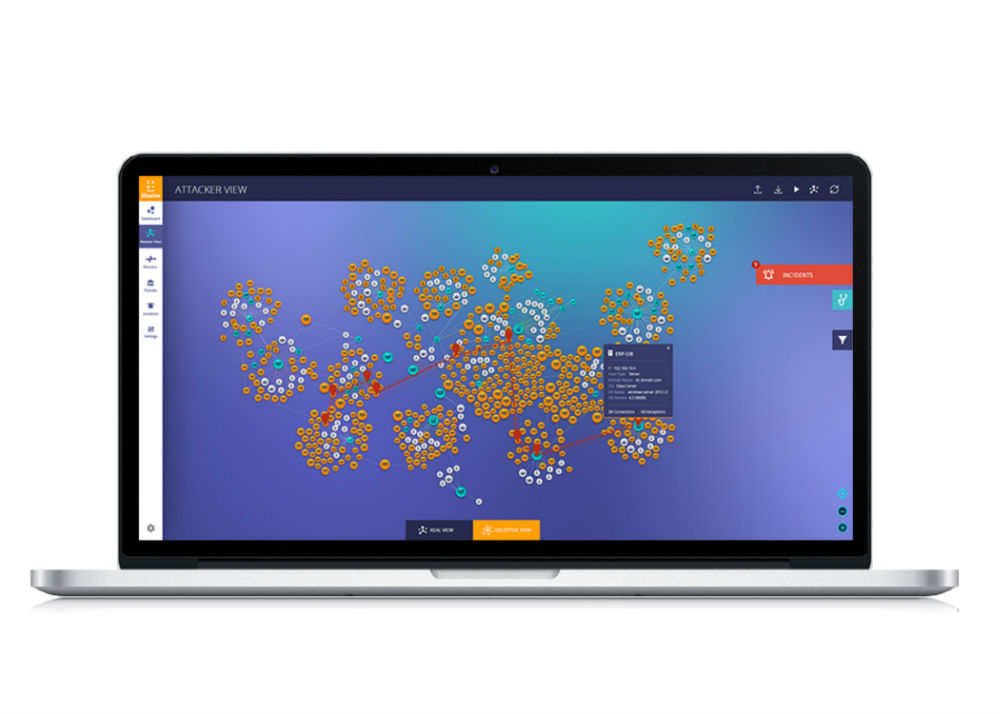
To beat an attacker, think like an attacker and see what an Advanced Attacker sees. illusive networks introduced the world’s first Attacker View™ technology that exposes hidden cyberattack paths. Attackers don’t see the network the way IT sees it. They rely on credentials such as users, servers and shares to conduct lateral movements throughout the network. Attacker View™ enables security professionals to see a complete map of their network from the attacker’s point of view, and:
Map the Network and Access Risk: Get a full map of the information seen by attackers for any point on the network. See your network based on accessibility, not physical connections – just as attackers do. Assess and mitigate potential risks – both insider and external threat risks.
Deploy Deceptions Everywhere™: Deploy threat deceptions that appear real such as users, shares, browsers, servers, FTP, and RDP across the entire network. Threat deceptions deployed everywhere across the network create a larger surface on which attackers must focus. Gain instant visibility on the deceptions’ effect on attacker’s lateral movement.
Track Movement and Extract Forensics: Follow and monitor attacker movements throughout the network. Attackers are unknowingly caught in action when illusive’s High Fidelity Forensics gathers relevant data, identifies their path, and extracts rich forensics in real-time.
Advanced attackers rely on one simple fact – that what they see is real and the data they collect is reliable.
What if we tamper with that data and create an environment where attackers cannot rely on the information they collect?
That is illusive.
How we are different
To beat an attacker, think like an attacker. Armed with a precise, detailed map of how attackers view and traverse a network with illusive networks Attacker View™, IT security professionals can now visualize attack paths for the first time ever, adapt their security strategy, and deploy threat deceptions to mitigate Advanced Attacker’s lateral movement.
- Unparalleled Cybersecurity DNA
illusive networks is a 2015 Gartner Security Cool Vendor, an RSA 2016 Innovation Sandbox Top 10 Finalist, CRN 25 Coolest Network Security Vendors 2016, and Worth Magazine 12 Companies that Could Change the Cyber Equation. illusive's Research and Development is conducted in Israel relying on the state-level security expertise of former IDF Unit 8200 leaders, researchers, and software developers.
- Using the Attacker's Psychology and Methods Against Him
illusive networks changes the asymmetry of APTs with threat deceptions that focus on the weaknesses of attackers: their need to use the data they find for lateral movement infiltration. Unlike old school honeypot deception technology that hopes an attacker will stumble upon it, illusive networks Deceptions Everywhere™ technology places thousands of pieces of false data across the network, on every network component directly in the path of would-be attackers. This is done on a level that actual network users will never encounter. An attacker's use of an illusive deception triggers the software and begins monitoring his movements and methods during, not post-attack. An illusive alert = an actionable alert.
- Ever Changing, Early Detection, High Fidelity, Low Maintenance, Agentless Deployment
Breakthrough cybersecurity that is simple to install, provides early detection, real-time rich forensics, is agentless (no executable code resides on the endpoints), no false positives - an illusive alert equals an attack, low maintenance for security professionals, and is ever changing and updating its Deception Families so attackers never know what to expect.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



