Photo Gallery
 |
 |
ImmuniWeb Discovery. Cyber Threat Intelligence


Additional Info
| Company | ImmuniWeb |
| Company size | 100 - 499 employees |
| World Region | Europe |
| Website | https://www.immuniweb.com/use-cases/cyber-threat-intelligence |
NOMINATION HIGHLIGHTS
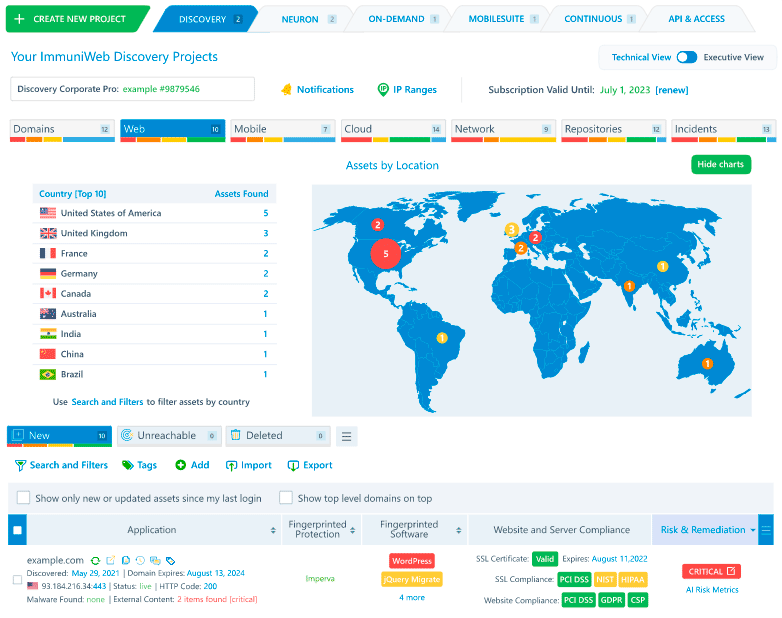
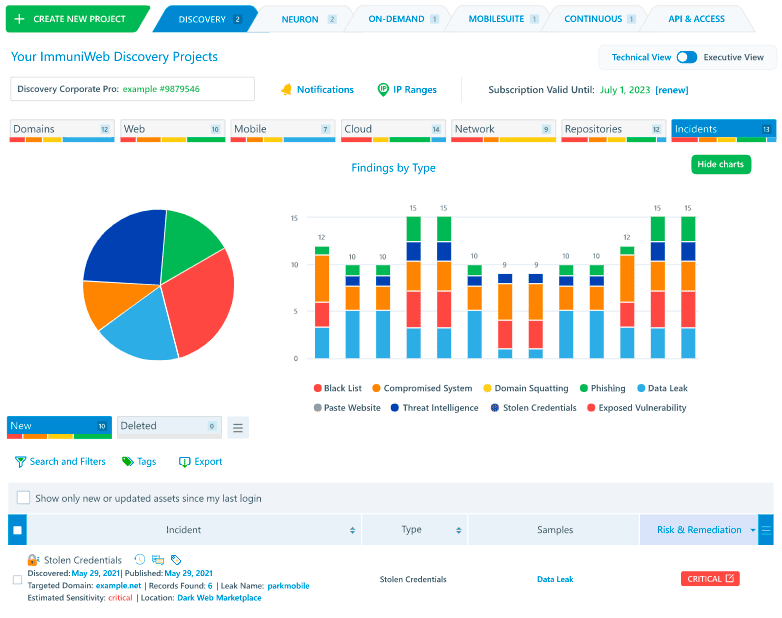
Monitor the surrounding cyber threat landscape and security incidents with ImmuniWeb® Discovery cyber threat intelligence offering. Bundled with our award-winning attack surface management technology, the cyber threat intelligence will automatically search for security incidents implicating any of your systems, domain names, applications, servers, cloud instances, brands or users, including shadow IT assets and shadow cloud resources.
Just enter your company name to get all mentions of your company or its IT assets on the Dark Web, hacking forums, underground marketplaces or Telegram channels. Our award-winning Machine Learning technology removes duplicates and fakes, offering reliable cyber threat intelligence feeds. Get instant alerts about the ongoing phishing campaigns, squatted domain names, fake accounts on social networks or malicious mobile apps usurping your corporate identity. Detect indicators of compromise (IoC) of your on-premise or cloud-based systems, as well as any mentions of your systems in various blacklists for suspicious or hacking activities.
Dispatch instant alerts about new security incidents, data leaks and cyber threats to relevant people in your DFIR or legal team by using groups and automated incident classification on the interactive dashboard. Export the cyber threat intelligence findings into a PDF or XLS file, or just dispatch them directly into your SIEM by using our API. Enjoy a fixed price per company regardless of the number of security incidents and mentions on the Dark Web. Our security analysts are here to help may you need additional details or support.
How we are different
- Instant alerts on shadow IT, abandoned, vulnerable, misconfigured assets
- Responding without delay to security incidents, data leaks or phishing
- In-depth security scoring of vendors and suppliers

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



