ImmuniWeb Discovery. Third-Party Risk Management
Recognized in the Category:
Photo Gallery
 |
 |
ImmuniWeb Discovery. Third-Party Risk Management

Additional Info
| Company | ImmuniWeb |
| Company size | 100 - 499 employees |
| World Region | Europe |
| Website | https://www.immuniweb.com/use-cases/third-party-risk-management/ |
NOMINATION HIGHLIGHTS
Prevent supply chain attacks and mitigate third-party risks with ImmuniWeb® Discovery third-party risk management. The third-party risk management offering is bundled with our award-winning attack surface management technology and is also enhanced with Dark Web monitoring to ensure inclusive visibility of cybersecurity risks and threats that external suppliers may pose for your business. The third-party risk management is available both as a one-time assessment and continuous security monitoring for business-critical vendors.
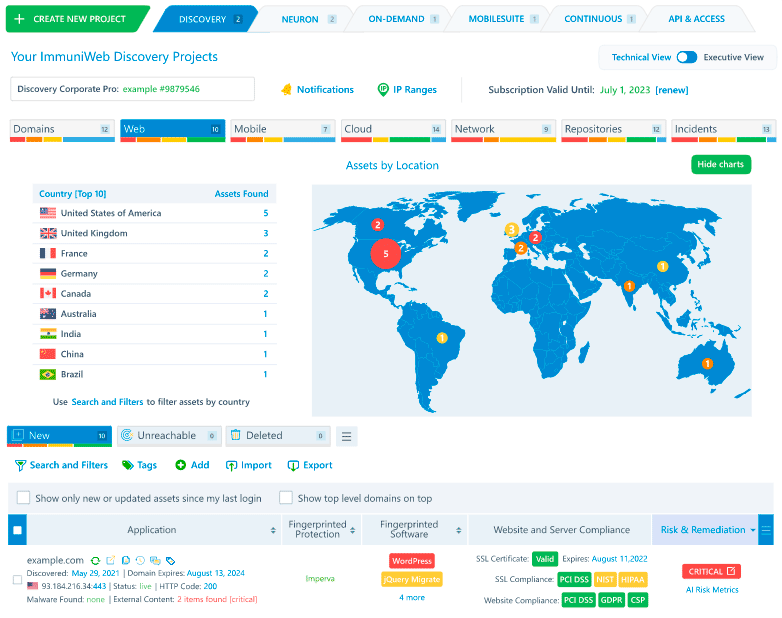
Just enter the name of your supplier or vendor to get a comprehensive snapshot of its external attack surface, misconfigured or vulnerable systems and applications, unprotected cloud storage, mentions on the Dark Web and data leaks, stolen credentials or compromised systems, ongoing phishing or domain squatting campaigns. The entire process is non-intrusive and production-safe, making it a perfect fit for your third-party risk management program. Our security analysts are available 24/7 may you have questions about the findings or need further assurance.
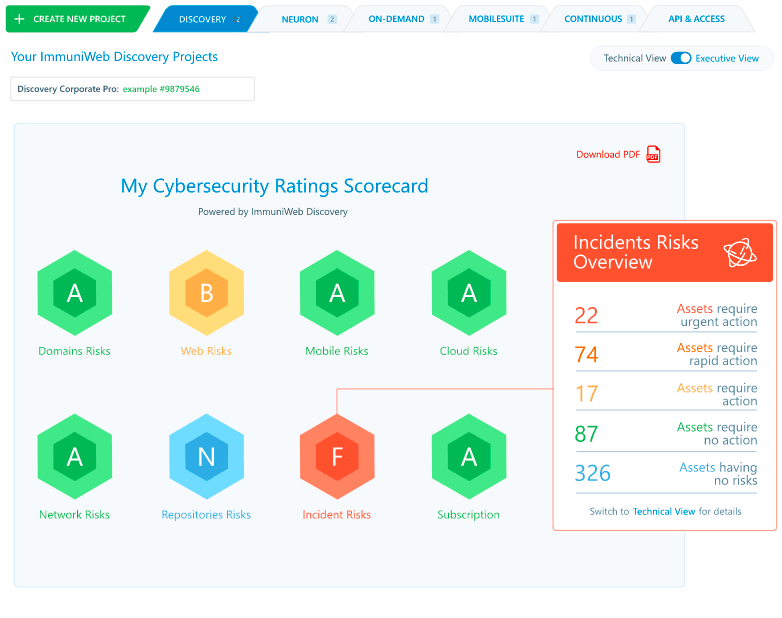
Get the risk-scored findings on the interactive dashboard where your vendors can also connect (with your permission) to see the details and rapidly remediate the problems. Prevent surging supply chain attack by taking your vendor risk management program to the next level. Fulfill the compliance requirements to regularly audit third-party systems that process personal, financial or other regulated data of your company. Enjoy a fixed price per vendor regardless the number of IT assets, mentions on the Dark Web or number of security incidents.
How we are different
- Instant alerts on shadow IT, abandoned, vulnerable, misconfigured assets
- Responding without delay to security incidents, data leaks or phishing
- In-depth security scoring of vendors and suppliers

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



