Photo Gallery
 |
 |
Infocyte HUNT

Additional Info
| Company | Infocyte |
| Company size | 10 - 49 employees |
| Website | http://www.infocyte.com |
NOMINATION HIGHLIGHTS
The reality of today’s cybersecurity landscape is that, within a complex enterprise network, no amount of investment in security controls will stop every breach, nor will it stop a well-resourced and determined attacker from getting in if they want to.
Firewalls, intrusion detection systems, and even antivirus are primarily in place for one reason – to prevent hacks and malicious software from getting onto a network. They employ reactive techniques to flag malicious activity and take immediate action via either alerting or blocking actions. Unfortunately, when they fail, they serve little use in searching for the missed threat.
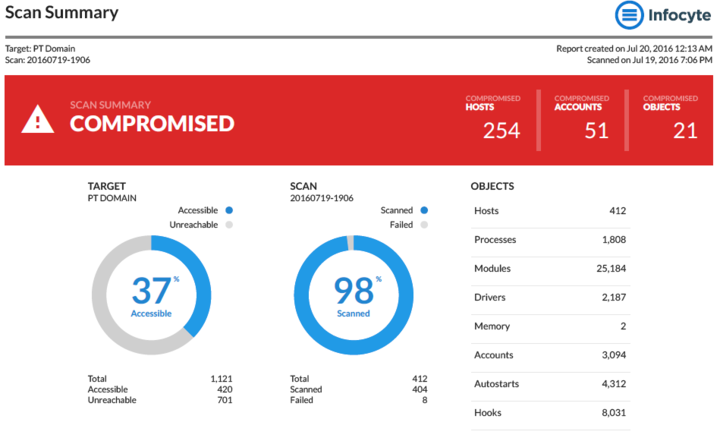
Infocyte HUNT enables security professionals to proactively discover the presence of attackers, active or dormant, who have successfully evaded their organization’s defenses and established a beachhead within the network. Infocyte’s unique, agentless threat hunting platform is designed to rapidly assess network endpoints for evidence of compromise without a forensics expert.
Infocyte HUNT automates the hunt process to improve the speed and efficacy of a hunt program with a unique, agentless threat hunting platform designed to rapidly assess network endpoints for evidence of compromise – without the burden of complicated equipment or endpoint software installations.
Infocyte HUNT gathers system information and scans volatile memory through patented technology with no pre-installation of software or agents; simplifying deployment and endpoint maintenance. Our unique architecture and approach enables operators to scan an enterprise network six times faster than other methods – delivering results in hours, not weeks.
It automates the search for threats and empowers an organization’s internal security teams to hunt without esoteric knowledge or a forensics expert. For the mature enterprise SOC already hunting, Infocyte HUNT enables you to do away with the custom scripts and other one-host-at-a-time DFIR processes you use to validate any suspicious behaviors that your team detects.
How we are different
• Other companies focus on real-time detection and behavioral analytics, Infocyte's unique approach scans the endpoints using forensic automation and patent-pending memory analysis techniques tailored to look for actual signs of malware or other compromises that made it past these first-line defenses.
• Infocyte HUNT gathers system information and scans volatile memory through patented technology with no pre-installation of software or agents; simplifying deployment and endpoint maintenance.
• Infocyte HUNT's unique architecture and approach enables operators to scan an enterprise network six times faster than other methods with no specialized training or forensics knowledge to use effectively – delivering accurate results in hours, not weeks.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



