Photo Gallery
 |
 |
Infocyte HUNT

Additional Info
| Company | Infocyte |
| Company size | 10 - 49 employees |
| Website | https://www.infocyte.com |
NOMINATION HIGHLIGHTS
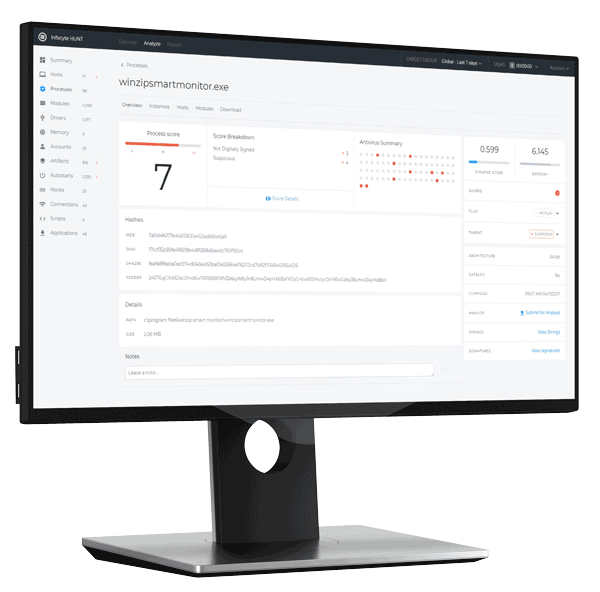
Infocyte HUNT is an advanced, intelligent, and surprisingly easy-to-use threat hunting platform. HUNT complements your defensive cybersecurity measures and automatically hunts down the threats (malware, breaches, vulnerabilities, etc.) that your AV, EDR/EPP, UEBA, and firewalls miss.
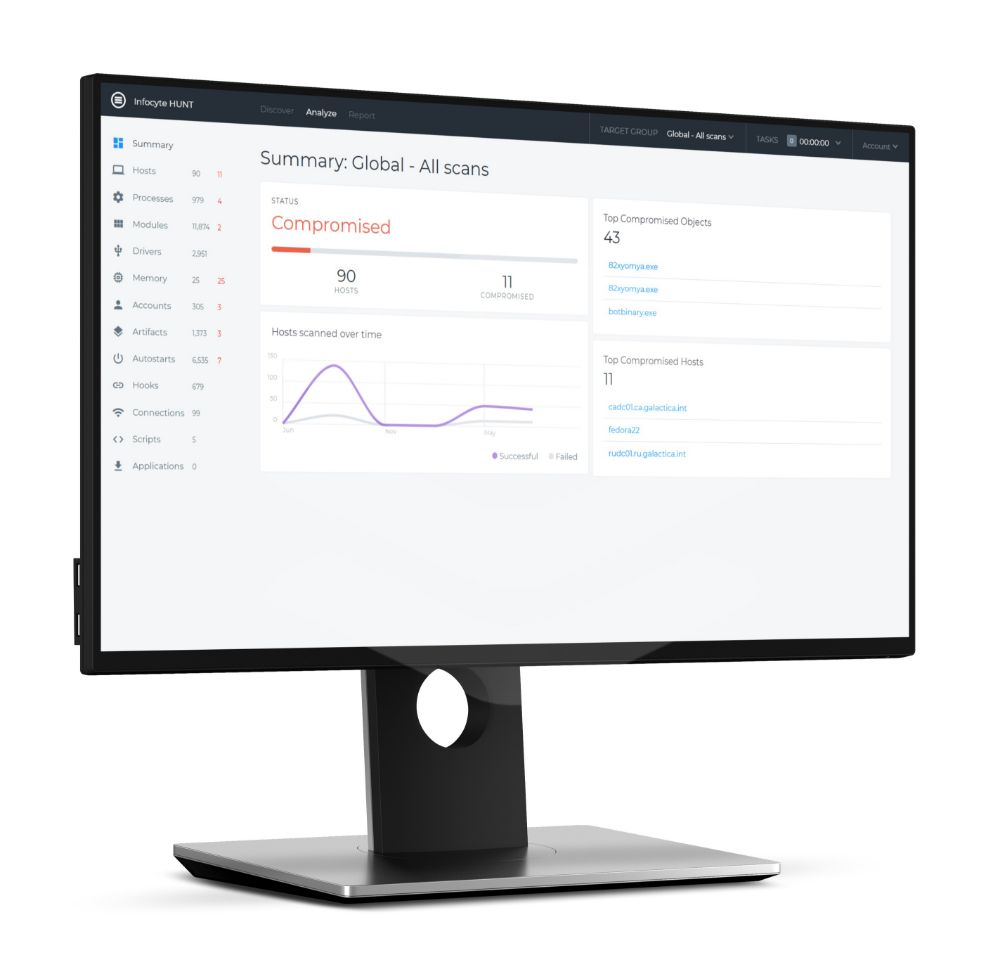
HUNT is a proactive cybersecurity product that forensically analyzes the endpoints on your network—including a deep scan of live volatile memory—helping organizations understand how exposed their networked assets are, identify threats capable of evading their existing defenses, and answer the questions:
1. Am I hacked?
2. Can I be hacked?
3. What can be hacked?
Threat hunting is traditionally services-heavy process and highly specialized skillset—requiring lots of time and resources. HUNT reduces the time/resources required by 90% by automating the threat hunting process.
Infocyte HUNT’s four core features include:
– Asset and Application Discovery
– Threat Hunting and Analysis
– Vulnerabilities and Vulnerability Management
– Reporting
To learn more and start a free trial, please visit https://try.infocyte.com.
How we are different
- HUNT uses Forensic State Analysis (FSA) which is radically different from other threat hunting solutions. Other hunting tools rely on analyzing SIEM and event-based security logs from cumbersome sensors and software installed on the endpoint. Rather than analyzing historical logs, Infocyte directly inspects volatile memory in the host in order to gather primary data including rootkit hooks, malware persistence mechanisms, application vulnerabilities, and other digital forensics artifacts.
- Those familiar with agentless vulnerability scanners will be familiar with how Infocyte HUNT is architected. By deploying lightweight dissolvable surveys, HUNT can sweep 5,000 endpoints per hour. This sweep gathers forensic data from each host, even those without conventional detection tools installed. The collected forensic data, when combined with Infocyte's analysis automation, provides a more comprehensive picture of the state of endpoints within minutes.
- Additionally, Infocyte HUNT is the only solution that can meaningfully facilitate compromise assessments. By automating the process of finding threats in live volatile memory, and combining that with cloud-based threat intelligence, Infocyte equips security operations teams and security assessors with the power to forensically evaluate the state of the network, without the lengthy manual process involved in traditional digital forensics.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



