Photo Gallery
|

|
InsightIDR


Additional Info
| Company | Rapid7 |
| Company size | 1,000 - 4,999 employees |
| Website | https://www.rapid7.com/products/insightidr/ |
NOMINATION HIGHLIGHTS
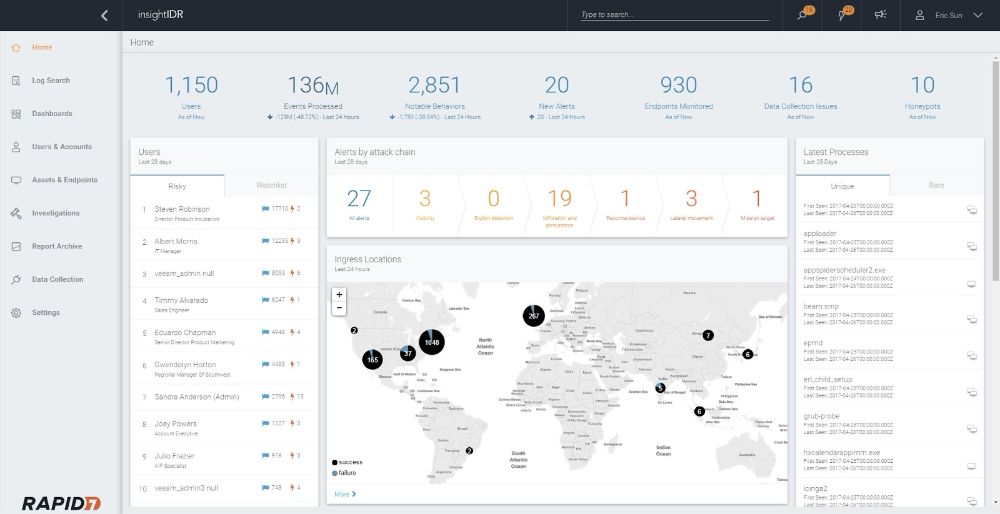
Historically, threat detection and response solutions require security professionals to parse through hundreds of vague false positives, manage an ever-growing mountain of data, and jump between siloed solutions to retrace user behavior. Investigators need both log search expertise and incident response experience in order to identify malicious behavior across the company.
In February 2016, Rapid7 launched InsightIDR to specifically tackle these challenges, giving security professionals the visibility and confidence they need to take better, faster action.
InsightIDR detects the threats other tools miss through a combination of User Behavior Analytics (UBA), deception technology, and native EDR agents. Security teams no longer need to write & tune rules or hire certified data splunkers to find answers hidden across users, log files and endpoints. Customers report that their investigations are 20 times faster now that real-time log search, user activity and endpoint data are in a single solution.
InsightIDR, running on a unique multi-tenant cloud architecture, comes with pre-built detections to find compromise earlier in the attack chain. It can serve as the SIEM you’ve always wanted or add security analytics to your existing deployment. Customers are getting up and running—and seeing value—in hours, without the worries of scaling or data management.
How we are different
InsightIDR is purpose-built for Incident Detection & Response (IDR), backed by our continuous research into the attacker. Our intelligent, patented detections are a result of collaboration with the Metasploit project, our elite red teams, and our Security Operations Centers. Most importantly, no more prolonged deployments, consulting, and support—you can identify compromise and check the box for compliance without it becoming a second full-time job.
Unify your data: Centralize, search, and visualize all of your logs—no data degree required.
Intelligent incident detection: Pre-built detections alert you of intruder presence at each step of the attack chain.
Prioritize your search: Automatically identify risky users and misconfigurations after adding in data sources.


