Photo Gallery
 |

 |
IONIX, Attack Surface Management Platform


Additional Info
| Company | IONIX |
| Company size | 50 - 99 employees |
| World Region | Middle East |
| Website | https://www.ionix.io/ |
NOMINATION HIGHLIGHTS
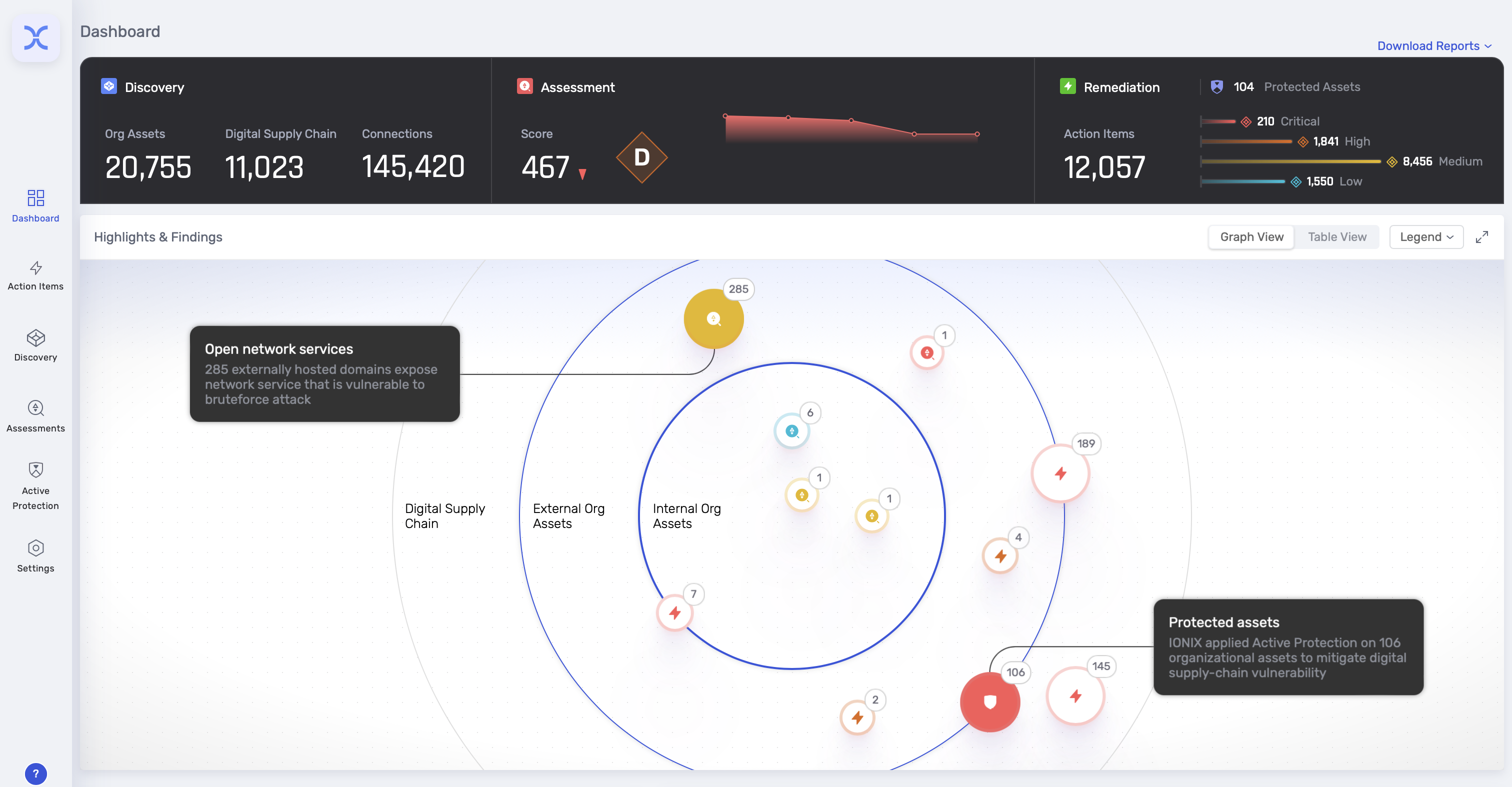
IONIX Attack Surface Management focuses on the discovery of every internet-facing asset and the ways those assets are connected, deep into an organization’s digital supply chain, shedding light on the most important risks to your business, and providing simple-to-follow recommendations to rapidly remediate exploitable threats and reduce attack surface risk.
By using Connective Intelligence, the platform shines a spotlight on exploitable risks across your entire attack surface – and its digital supply chain. Only IONIX Attack Surface Management monitors every internet-facing asset and connection, delivers laser focus into the most important risks to businesses, and provides recommendations to rapidly remediate exploitable threats and reduce attack surface risk. Global leaders including Lexmark, Infosys, The Telegraph, and E. ON depend on IONIX’s machine learning-powered discovery engine, contextual risk assessment and prioritization, and end-to-end remediation workflows to go on the offensive in managing their complex and ever-changing attack surfaces.
Key Capabilities / Features
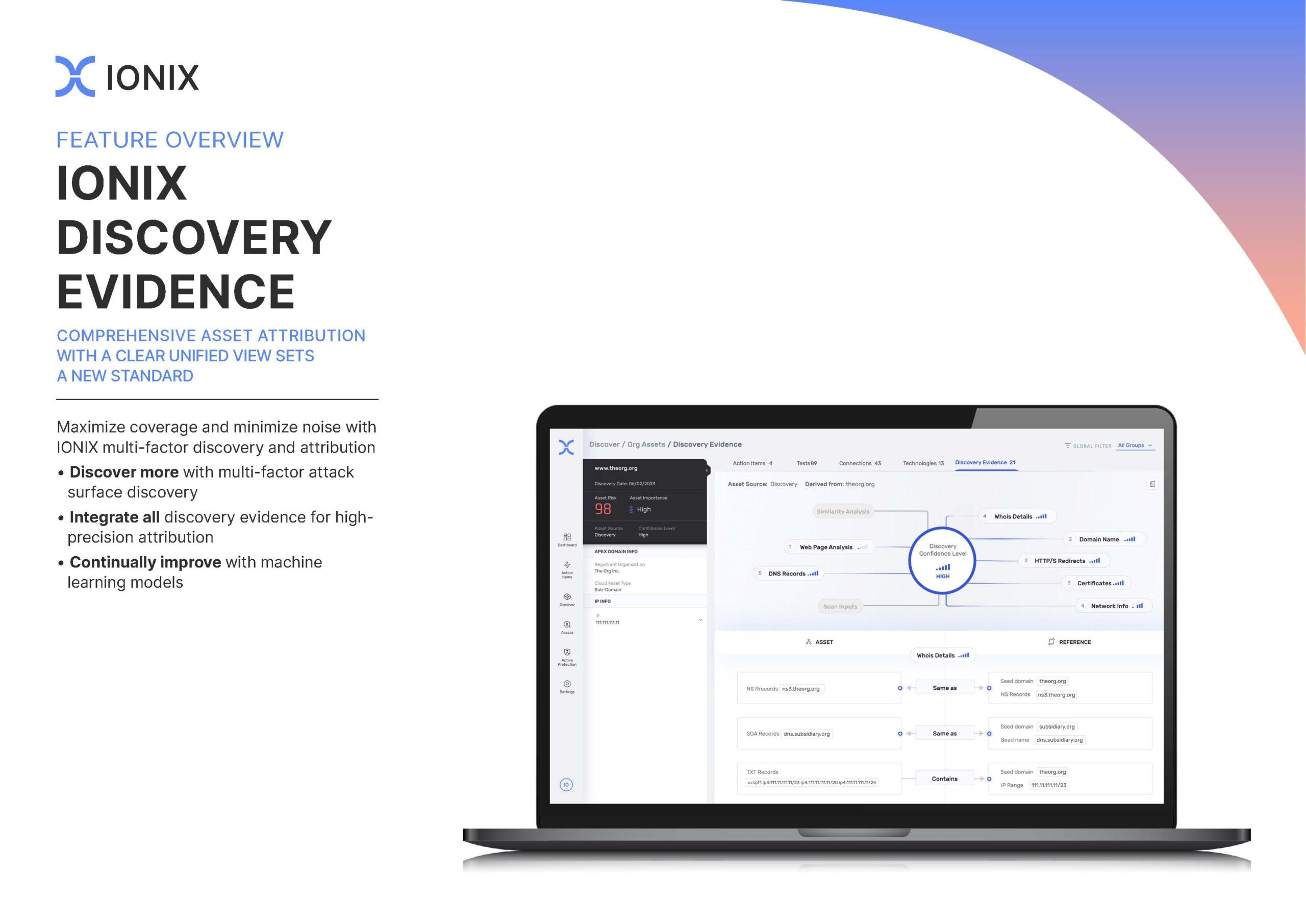
Attack Surface Discovery
-IONIX discovers customer assets, connected business partners and subsidiaries including third-, fourth- and fifth-party digital supply chain assets.
Cyber Risk Assessment
-The platform automatically conducts assessment of the organization's entire attack surface across 13 categories. Every asset is tested for vulnerabilities, misconfigurations, and security posture issues.
Security Validation – potential exploitability
-IONIX’s simulations use non-intrusive methods to validate security issues using stealthy operation techniques.
Prioritization
-IONIX prioritization framework provides risk severity, exploitability, asset importance and threat intelligence to help security teams stay focused on the most important risks.
Remediation
-The platform clusters multiple findings into clear recommendation actions, automatically attributed to the right subsidiary, leveraging integrated workflows with SIEM, SOAR and ticketing systems. IONIX’s innovative Active Protection can identify supply-chain-related misconfigurations and can automatically neutralize these threats.
Connective Intelligence
-IONIX is built on a graph data model, comprised of assets and connections. ‘Connective Intelligence’ refers to proprietary patented techniques that transform this data model into meaningful outcomes, for example, identifying digital supply chain-related vulnerabilities or misconfigurations to expose attack paths that may lead back to organizational assets.
IONIX Benefits:
Get full attack surface coverage
- Discover up to 50% more assets, even digital-supply chain assets
- Minimize false positives
- Map changes continuously
Assess further – focus only on what’s important and avoid noise
- Evaluate both assets and connections, Scan in context of 13 categories
Prioritize smarter – Not an inventory of assets, a connected map of exploitability
- Go beyond severity scores
- Integrated threat intelligence
- Analyze exploitability and blast radius
Remediate faster – MTTR of days, not months
Improve efficiency by clustering issues
- Simple-language action items for SOC and IT teams
- Streamline workflows with built-in integrations to SIEM, SOAR…
Protect automatically – take control of exploitable assets before hackers do
- Apply Active Protection on critically vulnerable assets, preventing attacks before they happen
How we are different
Deepest ASM Discovery (going deep into what’s known as 3rd and 4th party digital supply chain), with the capabilities to also let you know what is urgent and important for your security team to fix. We call this “Prioritization” and it encompasses many features of our product that together highlight only the critical risks that need to be fixed urgently.
Active Protection is a unique functionality of our product that, in cases where IONIX detects specific exploitable vulnerabilities, we can take over the asset before a hacker does. Active Protection automatically neutralizes the threat, with no action required on the security team's part.
The third unique feature is how we prioritize risk – even and especially within the digital supply chain. This is a combination of things that includes risk scores, asset importance, and what we call risky connections - meaning we know how assets are connected, and which connections are the most important. These features form the basis for our “Connective Intelligence”.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



