Photo Gallery
 |

 |
Ixia Application and Threat Intelligence

Additional Info
| Company | Ixia, a Keysight Business |
| Company size | 10,000 or more employees |
| Website | http://www.ixiacom.com |
NOMINATION HIGHLIGHTS
Ixia’s Application and Threat Intelligence (ATI) is developed by an elite group of application and security researchers from around the globe. Their expertise spans software development, reverse engineering, vulnerability assessment and remediation, malware investigation and intelligence gathering. Ixia’s ATI combines proficiency in cybersecurity threats and application protocol behavior. Ixia applies its application and threat intelligence across its test, visibility and security solutions to: create realistic application attacks from protocols, loading, and threats; block malicious inbound and outbound communications; collect ongoing intelligence on new threats; identify unknown applications; and detect traffic geolocation.
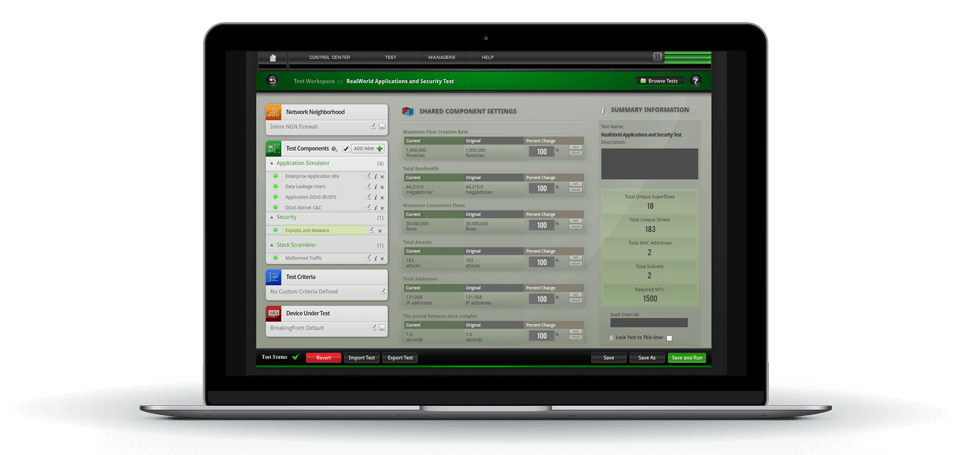
The ATI Research Center intelligence supports a wide range of Ixia products including AppStack capabilities on network packet brokers (NPBs), ThreatARMOR (threat intelligence gateway), and network security testing solutions BreakingPoint, IxLoad, IxChariot, and IxNetwork. ATI data sources are used in the test products used by every major security vendor, network equipment manufacturer, and service provider. Security vendors leverage the outputs of ATI research to verify their own products and applications run strong.
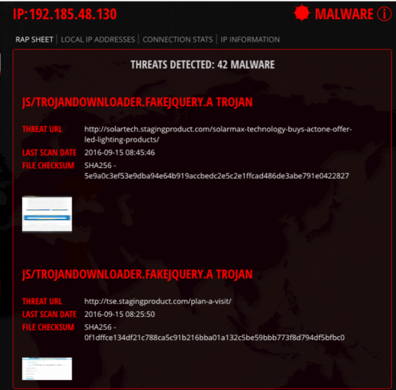
ATI operates a worldwide, distributed network of honeypots and web crawlers to actively identify known and unknown malware, attack vectors, and application exposures. In addition, the team regularly finds and discloses zero-day vulnerabilities. The team correlates this data with real world events, validate reported findings, and then push actionable intelligence to customers with continuous updates. ATI intelligence is sold to customer via subscription for Ixia’s network security products such as BreakingPoint, IxLoad, IxChariot, and IxNetwork as well as the ThreatARMOR threat intelligence gateway, including a daily malware service.
From their proprietary research, the ATI team aggregates newly discovered attacks and malware, providing application insight, including protocols, security attacks, and product enhancements on 400+ applications. It also aggregates intelligence to simulate realistic conditions and relevant attacks for a large database of exploits, including simulation of 100+ evasion techniques.
How we are different
1) Ixia's Application and Threat Intelligence is the foundation for Ixia's network visibility and network testing solutions.
2) ATI data feeds produce actionable security intelligence on application vulnerabilities
as well as threats across networks, endpoints, mobile devices, virtual systems, web,
and email. The ATI feeds automate the gathering and analysis of a wide range of threat
intelligence data from sources including:
• Billions of IPs and URLs
• Millions of spam
• Millions of malware attacks
• Open source data sets
• Millions of network intrusions
3) ATI Research Center team has a powerful understanding of how hackers exploit vulnerabilities missed before product launch or once they are in a live network. We partner with leading developers, monitor alerts across every layer of the Open Systems Interconnection (OSI) stack, and actively research threats around the globe to keep our application and threat intelligence feeds up to date with the latest data. The daily malware update service enables nearer-real-time malware threat intelligence that helps differentiate the most agile security systems from the rest.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



