Photo Gallery
 |
 |
K2 Security Platform by K2 Cyber Security

Additional Info
| Company | K2 Cyber Security |
| Company size | 10 - 49 employees |
| Website | http://www.k2io.com |
NOMINATION HIGHLIGHTS
Web applications are under attack more than ever before. Zero day exploits, based on new vulnerabilities, are expected to double in the next year. Yet, zero day attacks remain almost impossible to defend against with approximately 70% of zero day attacks going undetected by existing security tools.
K2’s Security Platform is the first to truly detect new zero day exploits as well as known vulnerabilities. Rather than rely on technologies that depend on prior attack knowledge, like signatures, heuristics, fuzzy logic, machine learning or Artificial Intelligence, the K2 Security Platform uses a deterministic approach to detect true zero-day attacks. Traditional security approaches are limited to detecting attacks based on prior attack knowledge or require weeks or months to learn behavior. K2’s Security Platform can detect new zero day attacks within seconds of application startup.
K2’s Security Platform is based on a unique, patent-pending technology called Optimized Control Flow Integrity (OCFI). OCFI uses application execution validation as the primary source of attack detection. K2 maps the application as it is running in memory and verifies the function calls and API calls within the application are executing the way the code intended. K2’s unique approach has virtually no false alerts, since it does not rely on any matching technologies.
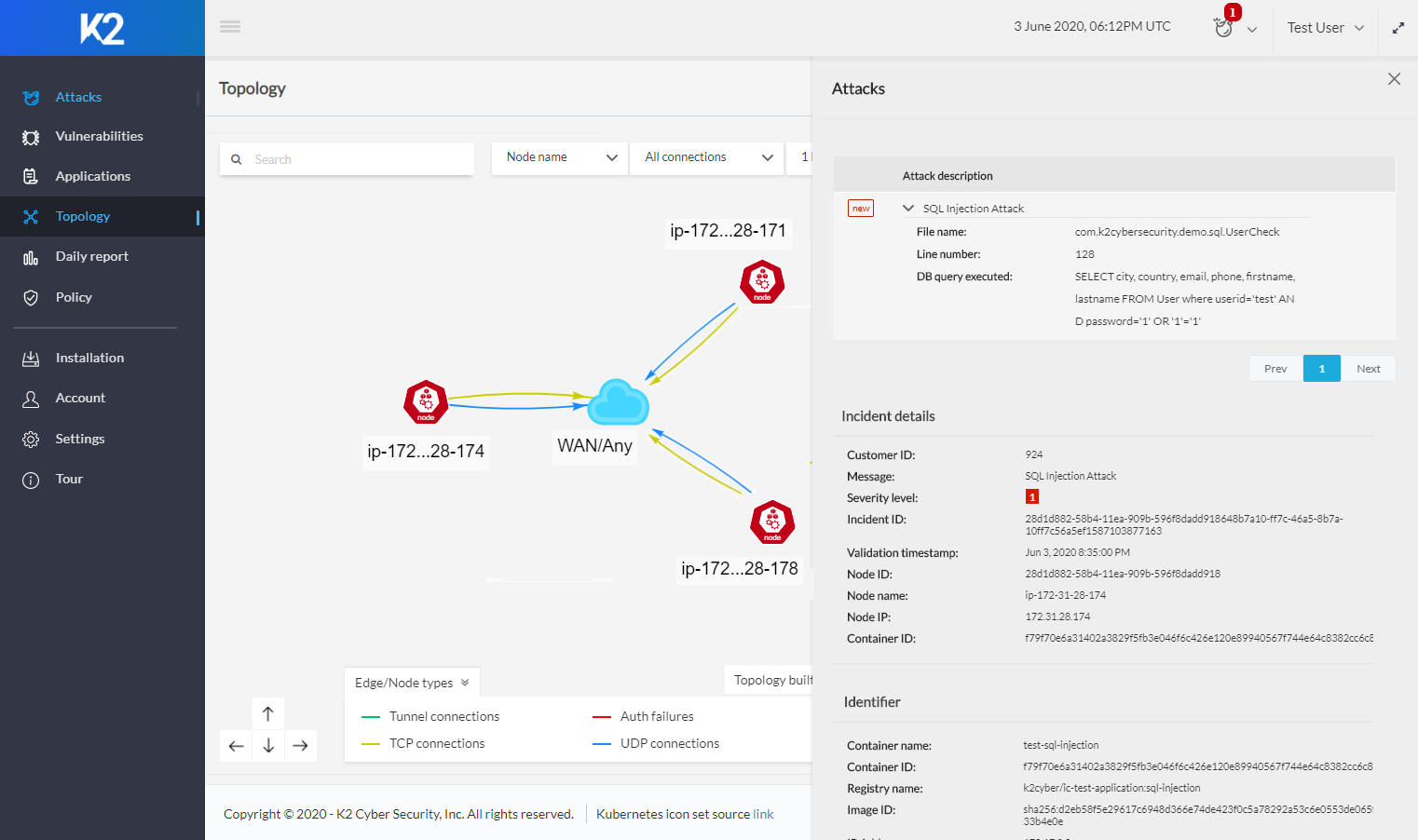
K2’s Security Platform issues alerts based on severity of the vulnerability and includes actionable alerts that provide complete visibility to the attacks and vulnerabilities. By providing the location of the vulnerability within the application, as well as details like file name and line of code where the vulnerability exists, security organizations can quickly address the vulnerability and remediate the problem.
K2’s Platform is easy to install and can be deployed in the cloud, on premise or in hybrid environments.
How we are different
o K2’s unique, deterministic approach offers industry’s first true detection of zero day attacks, with no need for prior attack knowledge, and uses patent-pending OCFI technology
o Detailed attack telemetry, including targeted filename and line of code, pinpoints exact vulnerability location for quicker remediation
o Lightweight, non-intrusive approach to security that validates code execution and protects the application in real time.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



